Using native tools for managing Windows Server log files
When you need to manage and ensure compliance with standards like SOX, HIPAA, or PCI DSS, it’s crucial to review Windows Event logs across your network. However, Microsoft's native tool, Event Viewer, often requires manual inspection server by server. This process becomes cumbersome, especially considering the vast amount of uncompressed log data generated, leading to constant concerns about disk space availability.
To streamline this process, consider setting up a centralized logging solution. This solution brings together logs from various sources like Windows Event logs, security logs, and application services logs. The solution enables you to simplify reviewing logs and saves storage space.
With a centralized logging solution, you can get a single place to review logs. That may help make compliance monitoring more efficient and cut down the time needed for manual log checks.
Enabling complete control over Windows Server logs
Netwrix Auditor for Windows Server enables you to efficiently manage Windows Server log files, security events, and system logs from computers across your network. The application helps you stay on top of log monitoring and better manage Windows event logs by:
- Alerting you in real-time via email on the events you define as critical.
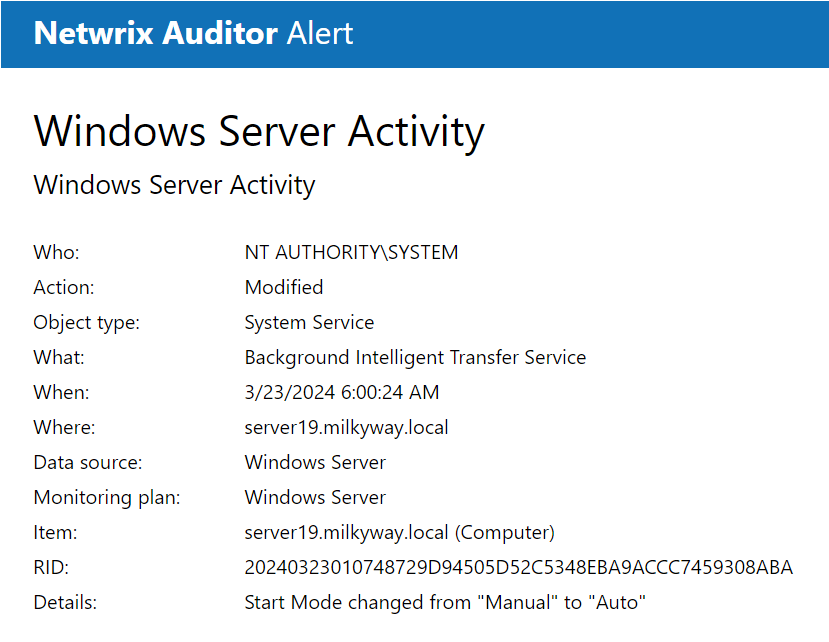
- Consolidating, compressing, and archiving logs in cost-effective, quick, easily accessible two-tiered storage for years.
- Enabling you to create custom views of reports. For example, filtering by a user or a computer of particular interest.
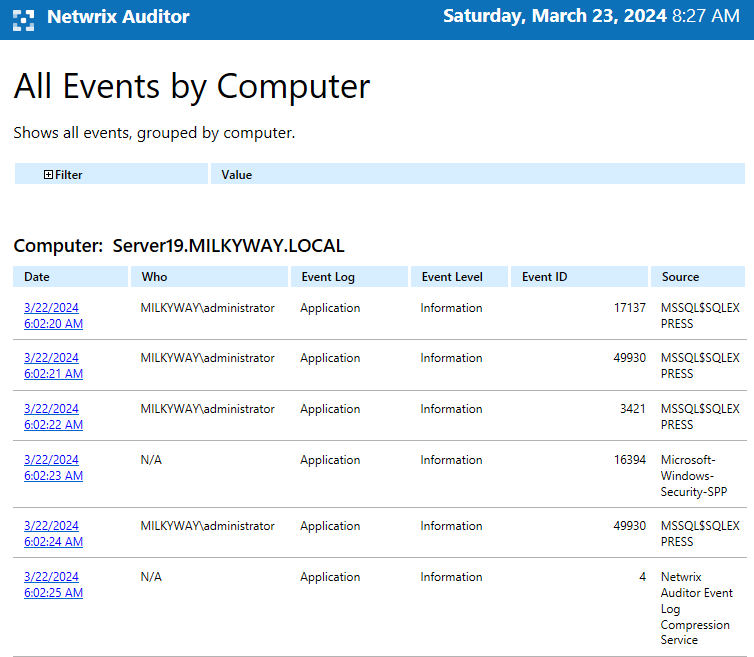
- Delivering all the necessary reports to your mailbox according to your schedule.
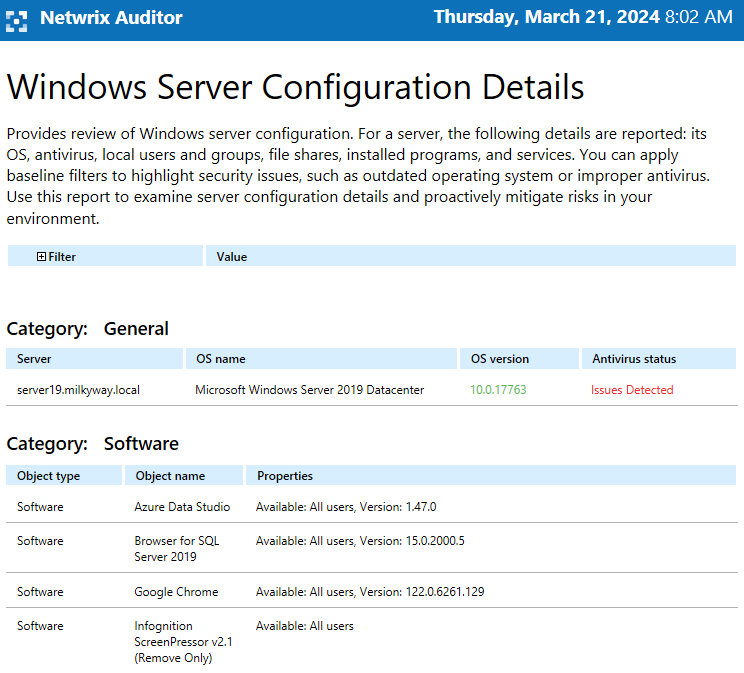
- Enabling you to review your server configurations and spot deviations from a known good baseline.
- Empowering you with predefined compliance reports so you can provide auditors with the evidence they require.
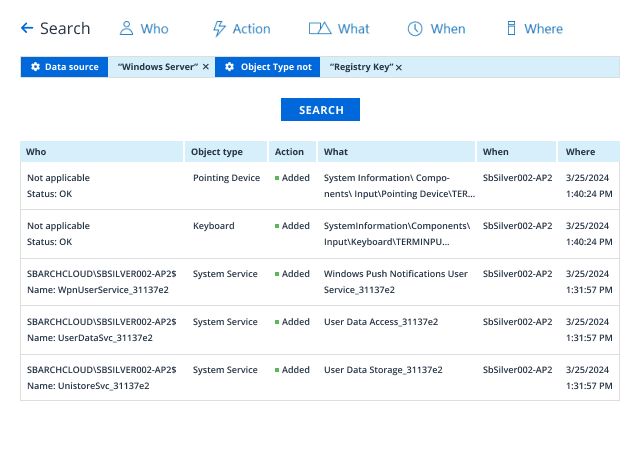
- Providing visibility into all changes made to server and IIS configurations via interactive search, out-of-the-box reports, and reports with custom views to strengthen security.
- Video recording of user screen activity, even in systems or applications that produce no logs.
FAQ
What is event log monitoring?
Event log monitoring means reviewing and analyzing the Windows event logs generated by systems and applications within an IT infrastructure. This process includes monitoring events such as user logins, system errors, security breaches, and other activities recorded in event logs.
The goal of event log monitoring is to identify and respond to any unusual or suspicious activities. It also aims to ensure compliance with security and regulatory requirements. This is achieved using specialized software tools that collect and analyze event log data. Additionally, it may involve setting up alerts and automated responses to specific events.
What are the Windows Server logs?
Windows Server logs are records of events within the Windows Server operating system, marked with event IDs. These logs are essential for monitoring and troubleshooting the server's performance, security, and operational issues. Monitoring and analyzing these logs can help administrators identify and address security breaches, system errors, application failures, and other events that may impact the server's performance and stability.
What is the purpose of event logs?
The purpose of event logs is to provide a detailed record of events and activities that occur within an information system or application. Event logs provide valuable insights into the behavior of systems and applications, enabling administrators to manage and maintain their infrastructure proactively.
What types of events do exist?
Event types can vary depending on the operating system, application, or system component. Below are a few event types which you may see in event logs:
- Informational events record normal operational activities, such as system startup, application startup, or successful task completion.
- Warning events indicate potential issues or conditions that may require attention but do not necessarily indicate a critical problem. For example, you may see a warning event when a disk runs low on space.
- Error events indicate that a specific operation or task has failed. These events can help diagnose and troubleshoot issues within the system.
- Critical events represent severe errors or failures that can significantly impact the system's operation. These events often require immediate attention to prevent system downtime or data loss.
- Security events are related to login attempts, changes to user privileges, or potential security breaches.
- Audit events track and record specific activities for compliance, auditing, and accountability purposes. These events can include changes to system configuration, file access, or other administrative actions.
What is the purpose of using Windows event log monitoring tools?
Windows event log monitoring tools are critical in maintaining the security, stability, and operational efficiency of Windows-based IT environments. These tools are designed to collect, analyze, and manage event logs from Windows-based systems and applications.
The following are the primary purposes of Windows event monitoring tools:
- Security Monitoring: Event log monitoring tools help organizations detect and respond to security-related events, such as unauthorized access attempts, changes to user privileges, and potential security breaches. By analyzing event logs in real-time, these tools can provide early detection of security incidents and enable swift response.
- Diagnostics and troubleshooting: Event log monitoring tools can help IT teams diagnose and troubleshoot issues within Windows systems and applications by providing a centralized view of event logs. This can aid in identifying the root cause of problems, such as system errors, application crashes, or performance issues.
- Compliance and auditing: Many event log monitoring tools offer features to assist organizations in meeting regulatory compliance requirements. These tools can help collect and retain event logs for auditing purposes, ensure accountability, and provide a trail of actions taken within the system.
- Performance monitoring: Event log monitoring tools can monitor system performance, resource usage, and application behavior. By analyzing performance-related events, administrators can optimize system performance, identify bottlenecks, and plan for capacity upgrades.
- Centralized log management: Windows event log monitoring tools provide a centralized platform for collecting, storing, and managing event logs from multiple Windows-based systems and applications. This centralized approach simplifies log management and gives administrators a comprehensive view of the IT environment.
- Real-time alerts and notifications: Event log monitoring tools can generate real-time alerts and notifications based on predefined criteria, allowing administrators to respond quickly to critical events and security incidents.
What are the critical event logs to monitor?
When monitoring Windows event logs within an IT environment, several event logs can help organizations detect and respond to security incidents, system errors, and performance issues.
- Security logs: The security event log is crucial for monitoring security-related activities, such as user logins, logouts, failed login attempts, changes to user privileges, and other security-related events.
- System logs: The system event log records events generated by the Windows operating system components. It includes information about system errors, warnings, and other system-related events.
- Application logs: The event log records events generated by applications or programs running on the system. It includes information about application errors, warnings, and information messages.
- Network and firewall logs: Network and firewall logs are crucial for security and monitoring. They include records of network connections, source and destination IP addresses, ports, protocols, and timestamps. These logs also provide information on traffic type and volume passing through network devices like routers, switches, and intrusion detection/prevention systems. Firewall logs focus on activities at network boundaries, monitoring traffic flows, recording rule matches, and enforcing predefined policies.
- Active Directory logs: For organizations using Active Directory, monitoring the Active Directory logs is essential for tracking user and group management, authentication events, and changes to the directory structure.
- Database logs: Monitoring database logs provides insights into database performance, errors, and security-related activities for systems with databases.
- Compliance and audit logs: For organizations under regulatory compliance, it's important to monitor compliance and audit logs. These logs track changes to system configurations, file access, and administrative actions.