Native Auditing
Netwrix Auditor for Active Directory
Steps
- Run gpedit.msc → Create a new GPO → Edit it : Go to "Computer Configuration" → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy:
- Audit account management → Define → Success.
- Go to Event Log → Define:
- Set the maximum security log size to 4 GB
- Set the retention method for the security log to "Overwrite events as needed".
- Link the new GPO to OU with User Accounts: Go to "Group Policy Management" → Right-click the defined OU → Choose "Link an Existing GPO" → Choose the created GPO.
- Force a Group Policy update: Go to "Group Policy Management" → Right-click the defined OU → Click "Group Policy Update".
- Run adsiedit.msc → Connect to the Default naming context → Right-click the domain DNS object with the name of your domain → Click Properties → Select the Security (Tab) → Click Advanced (Button) → Select Auditing (Tab) → Add the principal "Everyone" → Type "Success" → Apply this to "This object and descendant objects" → Click Permissions → Select all check boxes except the following:
- Full control
- List contents
- Read all properties
- Read permissions → Click "OK".
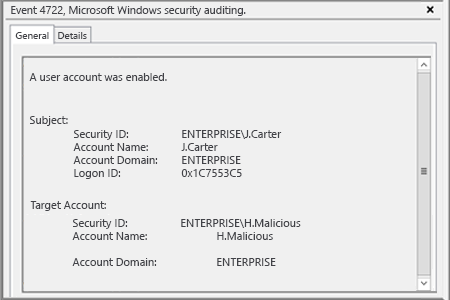
- Open Event Viewer and search the security log for event ID 4722 (a user account was enabled).
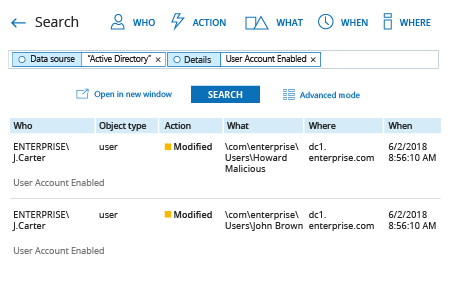
- Run Netwrix Auditor → Navigate to “Search” → Click on “Advanced mode” if not selected → Set up the following filters:
- Filter = “Data source”
Operator = “Equals”
Value = “Active Directory” - Filter = “Details”
Operator = “Contains”
Value = “User Account Enabled”
- Filter = “Data source”
- Click the “Search” button and review who enabled which user accounts in your Active Directory.
In order to create an alert triggered each time whenever someone enables a user account:
- From the search results, navigate to “Tools” → Click “Create alert” → Specify the new alert’s name.
- Switch to the “Recipients” tab → Click "Add Recipient" → Specify the email address where you want the alert to be delivered.
- Click “Add” to save the alert.