Microsoft Entra ID’s self-service capabilities facilitate mobility and provide a better user experience by enabling users to change their passwords without calling anyone for support or creating tickets. However, with this capability in place, admins have to be diligent about tracking password resets so they can spot any suspicious actions that could be indicative of identity theft.
Tracking Microsoft Entra ID password resets with audit logging in Microsoft Entra ID
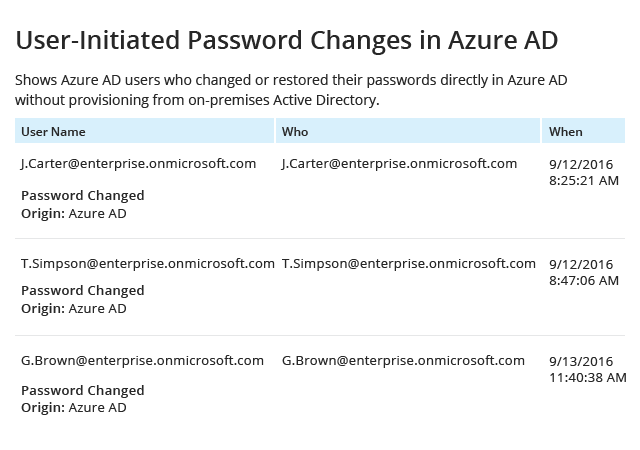
The Microsoft Entra ID (formerly Azure AD) password reset capabilities is convenient for users and reduces helpdesk costs. But because it enables any user to perform an Azure password reset from any device at any location and at any time, this capability can create security gaps in your Microsoft Entra ID environment.
Microsoft Entra ID security best practices recommend staying on top of all password changes in order to minimize the risk of anyone using another user’s credentials to make unauthorized changes or access sensitive data. To get insight into password reset and registration activity across your Microsoft Entra ID, you can use Microsoft Azure audit logging data. However, to find the exact information you need, you’ll have to spend valuable time filtering the data. Plus, you’ll have to plan ahead about where you’ll keep your audit logs for the long term, because you can store them in Microsoft Entra ID for only 90 days.
Keeping abreast of Azure password reset activity with Netwrix Auditor
Do you want to harden the security of your Microsoft Entra ID environment against the risk of identity theft and other unauthorized activity? Netwrix Auditor for Microsoft Entra ID delivers 360-degree visibility into Azure AD sign-in attempts (successful and failed); Microsoft Entra ID password resets; changes to configurations, groups, roles, applications and devices; and much more. Netwrix Auditor goes beyond traditional audit logging by delivering the security intelligence you need to keep tabs on what’s happening in your Microsoft Entra ID. With this solution at your fingertips, you can:
- Quickly detect and remediate suspicious sign-in attempts and changes, including Microsoft Entra ID password resets, using detailed easy-to-read reports that you can have delivered automatically on the schedule you specify.
- Easily investigate any aberrant activity and drill down to the root cause of a security incident with the Google-like Interactive Search feature.
- Finally get a good night’s sleep with custom alerts on critical activity and threshold-based alerts that help ensure your Microsoft Entra ID is protected from malicious insiders and external attackers.
- Keep your Microsoft Entra ID audit data stored securely for over 10 years in the cost-effective two-tiered (SQL database + file-based) storage, and easily access it whenever there is a need.
- Stay on top of activity across your on-premises Active Directory as well with Netwrix Auditor for Active Directory, and ensure your visibility gaps are close to zero.