HIPAA Compliance Software from Netwrix
See how Netwrix can helpyou pass compliance audits
Address Privacy & Security Challenges with HIPAA Compliance Software
The Health Insurance Portability and Accountability Act (HIPAA) establishes U.S. national standards for protecting the security of individually identifiable electronic health information. The requirements apply to healthcare providers, health information organizations, and other covered entities and business associates that store, transmit or manage protected health information. HIPAA security software can help you address the law’s provisions concerning the privacy and security of electronic protected health information, such as the rights of individuals to access or amend their protected health information; HIPAA security rules covering administrative and technical safeguards; requirements for policies and procedures; and documentation requirements. HIPAA compliance software from Netwrix can help you establish and maintain data security controls aligned with the following HIPAA privacy requirements:
- Part 164: Security and Privacy
- Subpart C: Security Standards for the Protection of Electronic Protected Health Information
- § 164.308: Administrative safeguards
- § 164.312: Technical safeguards
- § 164.316: Policies and procedures and documentation requirements
- Subpart D: Notification in the Case of Breach of Unsecured Protected Health Information
- § 164.404: Notification to individuals
- § 164.410: Notification by a business associate
- Subpart E: Privacy of Individually Identifiable Health Information
- § 164.524: Access of individuals to protected health information
- § 164.526: Amendment of protected health information
- § 164.528: Accounting of disclosures of protected health information
- Subpart C: Security Standards for the Protection of Electronic Protected Health Information
Depending on the configuration of your IT systems, your internal procedures, the nature of your business and other factors, Netwrix might also facilitate compliance with provisions of the HIPAA not listed above.
HIPAA Compliance Software Helps Satisfy Audit & Data Protection Standards
Netwrix solutions provide complete visibility into on-premises and cloud-based systems and applications to enable control over user actions and improve data security. This HIPAA compliance software delivers security features that empower you to conduct HIPAA risk assessments, detect anomalies in user behavior, and investigate threat patterns before they turn into security incidents or disrupt business services. Unlike many other HIPAA audit software solutions, Netwrix provides out-of-the-box compliance reports mapped to specific requirements of HIPAA and many other common regulations, reducing the time and effort required for the compliance preparation process.
Support your risk management program with continuous IT risk assessment
Use the IT risk assessment functionality in Netwrix Auditor to enable continuous IT risk analysis. With the resulting security intelligence, you can identify and mitigate risks in areas such as account management, security permissions and data governance.
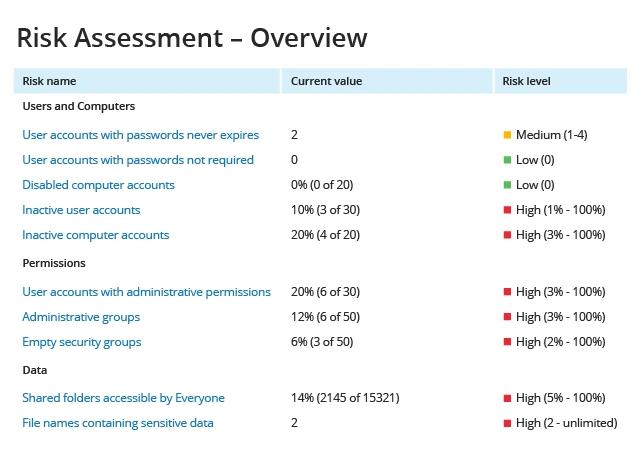
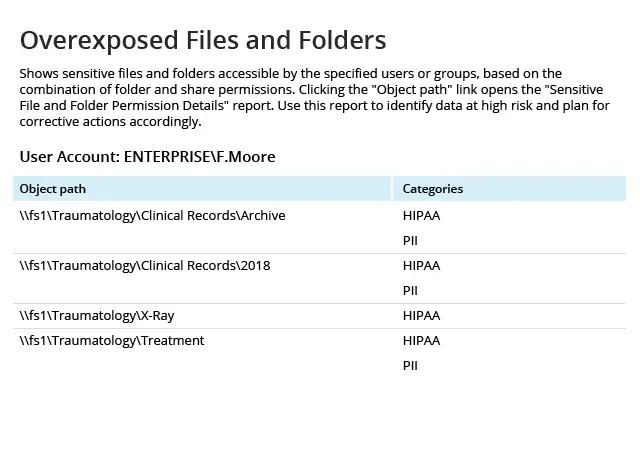
Identify the exact location of your PHI
With the Data Discovery and Classification, you can get a complete picture of where your sensitive data is located and know when any sensitive files surface outside of the secure locations. Use this information to remediate risk and to identify employees who require additional training on sensitive data management rules and procedures.
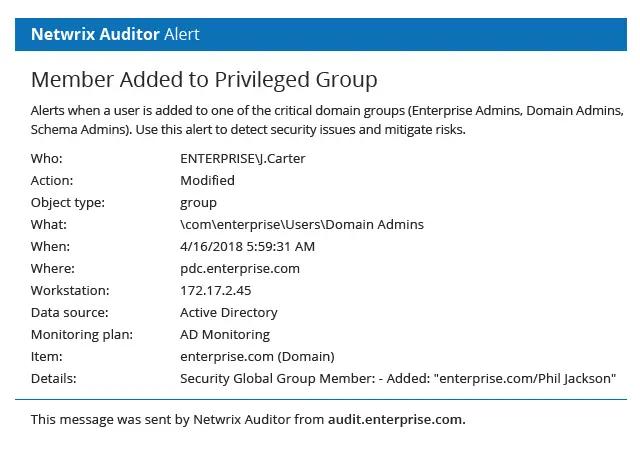
Stay on top of privilege escalation
Get notified any time a user is added to a privileged group, such as Enterprise Admins or Domain Admins, so you can quickly revert any improper changes to mitigate risks to your critical resources and protected health information.
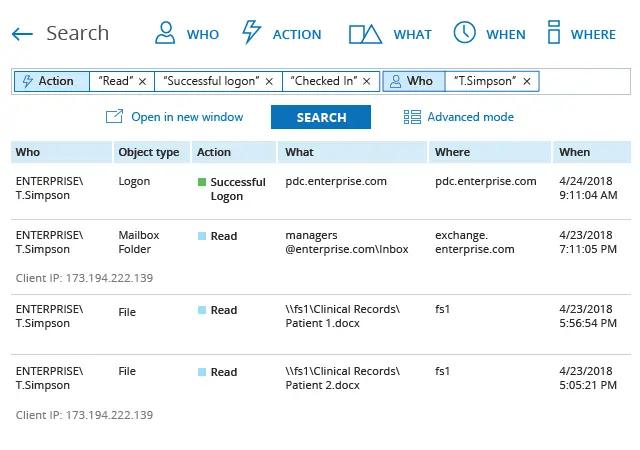
Investigate insider threats with cross-system visibility
If you spot suspicious changes or data access, use the Interactive Search feature to investigate the activity before it turns into a data breach. For example, if you see that one of your admins was accessing protected health records, you can easily get a list of all resources that employee accessed during a particular time period to check for other security violations.
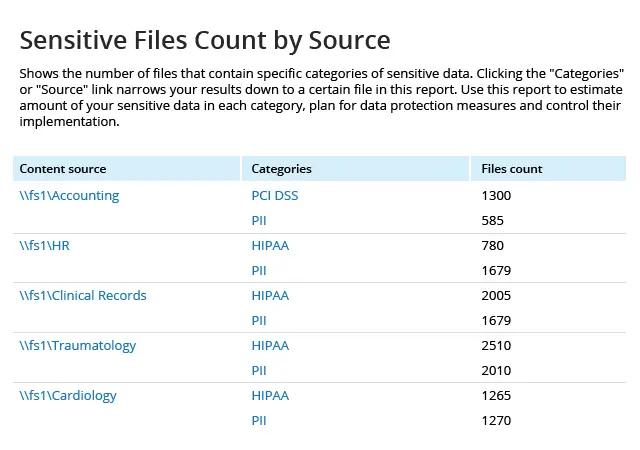
Determine the severity of a data breach
If a data breach occurs, use Data Discovery and Classification reporting to analyze which protected health information a malicious insider or a compromised account had access to, and which pieces of data were actually viewed. Use this data to contact all affected parties as prescribed in the requirement regulating breach notifications.
Check out real examples of organizations like yours that are using Netwrix to ensure the privacy and security of ePHI
Share on
View related compliance concepts
Netwrix helps you comply with Korea’s National Network Security Framework (N2SF)
Netwrix helps you comply with APRA CPS 234
Netwrix helps you comply with the Philippines Data Privacy Act (DPA)
Netwrix helps you comply with India’s Digital Personal Data Protection (DPDP) Act
Netwrix helps you comply with Indonesia’s Personal Data Protection (PDP) Law
