Netwrix Access Analyzer: The Entra ID & Active Directory Reporting Tool
Clean up cluttered AD and Entra ID environments with actionable insights. Automate governance, spot security gaps, and strengthen compliance.
Read their Stories
Trusted by




































































An intuitive Active Directory reporting tool for stronger, more compliant security
Visibility into security gaps
Pinpoint and fix critical security threats like weak passwords, vulnerable accounts, and dangerous configuration settings.
Strong governance automation
Automate ongoing housekeeping of stale, duplicate, or risky AD objects, including disabled or inactive user and workstation accounts.
Control AD permissions
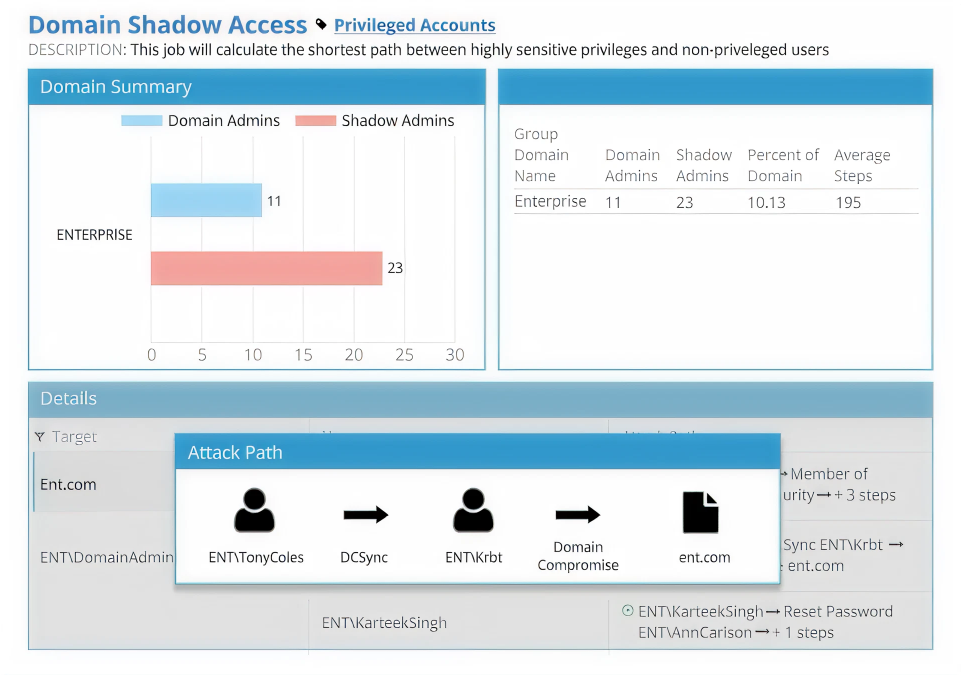
Identify risky permissions, misconfigurations, and hidden shadow admins with our AD reporting tool to reduce exposure and strengthen security.
Streamlined compliance reporting
Simplify AD compliance reporting with preconfigured reports tailored for HIPAA, PCI-DSS, GDPR, SOX, and other key regulatory requirements.
Capabilities
Everything you need to generate clear, comprehensive Entra ID and Active Directory reports
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.







