Netwrix helps you comply with CJIS
About CJIS
The CJIS Security Policy is a set of security standards created by the FBI’s Criminal Justice Information Services (CJIS) Division. It governs how Criminal Justice Information (CJI) is accessed, handled, transmitted, and stored by criminal justice and noncriminal justice entities. It outlines technical and procedural requirements to protect sensitive data used in law enforcement operations and ensures consistent data protection across jurisdictions and systems.
What is Criminal Justice Information?
- Biometric and Identity Data
Personal identifiers such as fingerprints, facial recognition data, iris scans, and DNA profiles, as well as identity history like names, aliases, dates of birth, and identification numbers. - Criminal History Information
Records related to an individual’s interactions with the justice system, including arrests, charges, prosecutions, convictions, sentencing, and incarceration. - Case-Related and Investigative Information
Details from police reports, investigative files, case notes, surveillance findings, and information gathered during ongoing investigations. - Administrative and Legal Records
Documents such as warrants, court orders, protection orders, and records related to probation, parole, or supervised release.
Why is complying with CJIS needed?
- Protecting sensitive Law Enforcement Data
CJI includes highly sensitive data such as arrest records, fingerprints, mugshots, investigative files, and biometric identifiers. It sets strict technical and administrative controls to safeguard this data from internal misuse or external threats. - Preventing Unauthorized Access to CJI
The policy enforces background checks, user access reviews, multi-factor authentication, and logging to reduce these risks and ensure that only authorized personnel can access CJI. - Enabling Secure Data Sharing between Jurisdictions
The CJIS Security Policy ensures that all entities follow the same rules, regardless of size or location, so that information can be exchanged without creating vulnerabilities in the system. - Ensuring Trust Among Agencies Using Shared FBI Systems
The FBI manages shared systems like NCIC, IAFIS, and NICS background checks for firearms. These databases are only as secure as their weakest link; if one agency has poor security practices, it can jeopardize the integrity of the entire network.
How does Netwrix help you comply?
As one of the leading cybersecurity solution vendors and providers, Netwrix aims to enable organizations with all the necessary tools to govern, identify, detect, protect, respond, and recover from data breaches be it caused by user, data, or infrastructure-related security gaps.
Our solutions aim to aid security professionals in their Risk Assessment, Threat Identification, and Incident Management efforts by minimizing the cybersecurity impacts, identifying their nature, narrowing their scope, pinpointing their exact timing, and protecting the organization’s most valued assets.
Netwrix Access Analyzer
Netwrix Access Analyzer automates data collection and analysis across over 40 modules, helping you manage and secure critical IT assets—from operating systems to Office 365—across on-premises and cloud environments.
Netwrix Access Analyzer and CJIS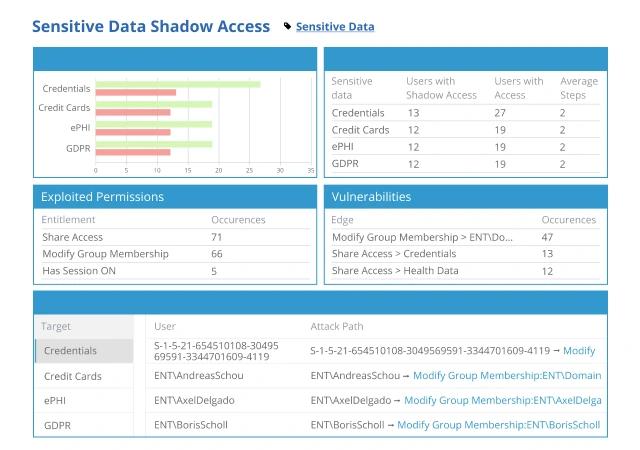
Netwrix Auditor
Netwrix Auditor is a visibility platform that tracks changes, configurations, and access across hybrid IT environments. It delivers security analytics to detect abnormal user behavior and investigate threats before breaches occur.
Netwrix Auditor and CJIS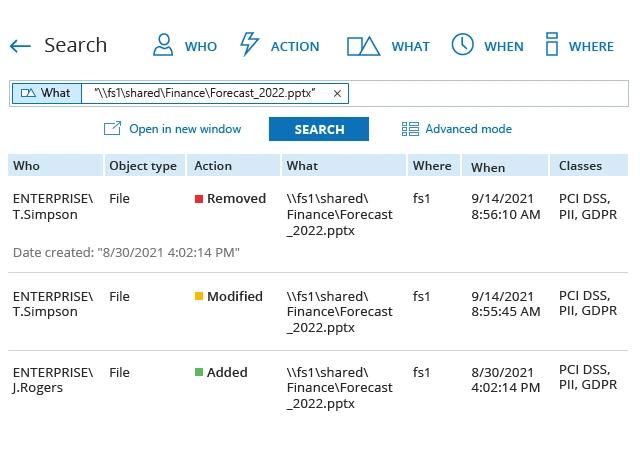
Netwrix Change Tracker
Netwrix Change Tracker is a system configuration and integrity assurance product, used for compliance programs, host intrusion detection, and change control management for enterprise IT systems.
Netwrix Change Tracker and CJIS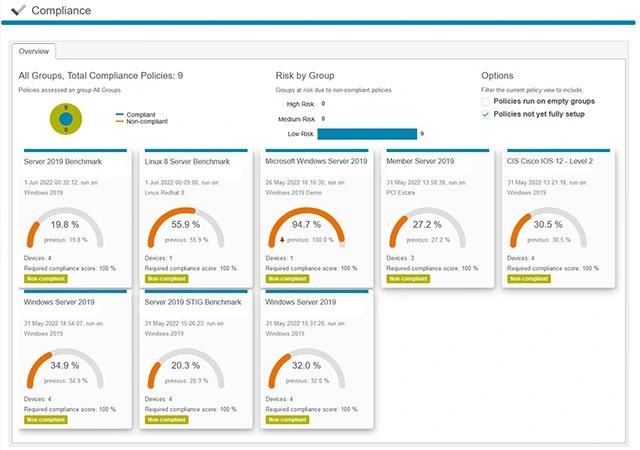
Netwrix Data Classification
Netwrix Data Classification is a data identity platform that enables your organization to reduce risk and unleash the true value of this data.
Netwrix Data Classification and PCI DSS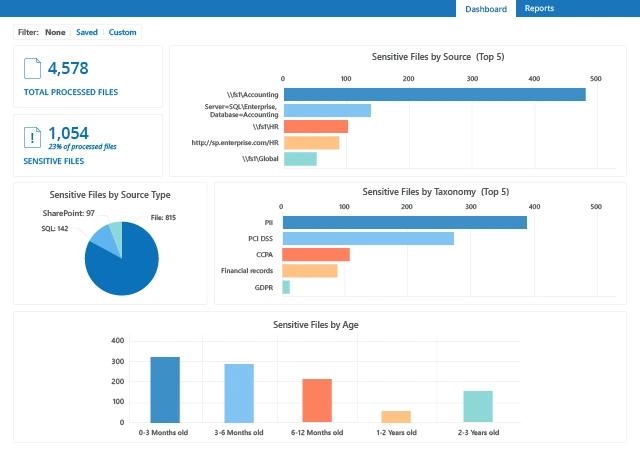
Netwrix Endpoint Policy Manager
Netwrix Endpoint Policy Manager simplifies policy management across diverse endpoints—virtual desktops, thin clients, domain-joined and non-domain-joined devices—ensuring consistent security in hybrid environments.
Netwrix Endpoint Policy Manager and CJIS
Netwrix Endpoint Protector
Netwrix Endpoint Protector is a multi-OS DLP solution that protects data in real time across Windows, macOS, and Linux—even offline. It helps prevent unauthorized data transfers via USB, email, browsers, and messaging apps, enabling stronger endpoint security and risk management.
Netwrix Endpoint Protector and CJIS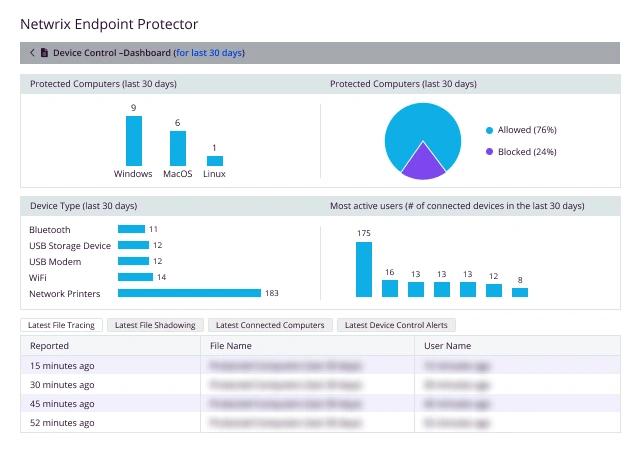
Netwrix Privilege Secure
Netwrix Privilege Secure is a next-gen PAM solution that simplifies privileged task management by focusing on actions rather than accounts, reducing complexity and minimizing the attack surface.
Netwrix Privilege Secure and CJIS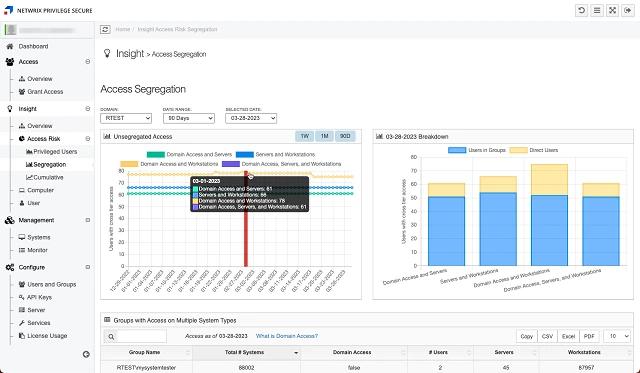
FAQs
Share on
View related compliance concepts
Netwrix helps you comply with Korea’s National Network Security Framework (N2SF)
Netwrix helps you comply with APRA CPS 234
Netwrix helps you comply with the Philippines Data Privacy Act (DPA)
Netwrix helps you comply with India’s Digital Personal Data Protection (DPDP) Act
Netwrix helps you comply with Indonesia’s Personal Data Protection (PDP) Law
