Identity Threat Detection & Response (ITDR)
Proactively prevent threats, detect and contain attacks faster, and recover quickly to keep your business resilient with Netwrix ITDR.
Read their Stories
Trusted by





































































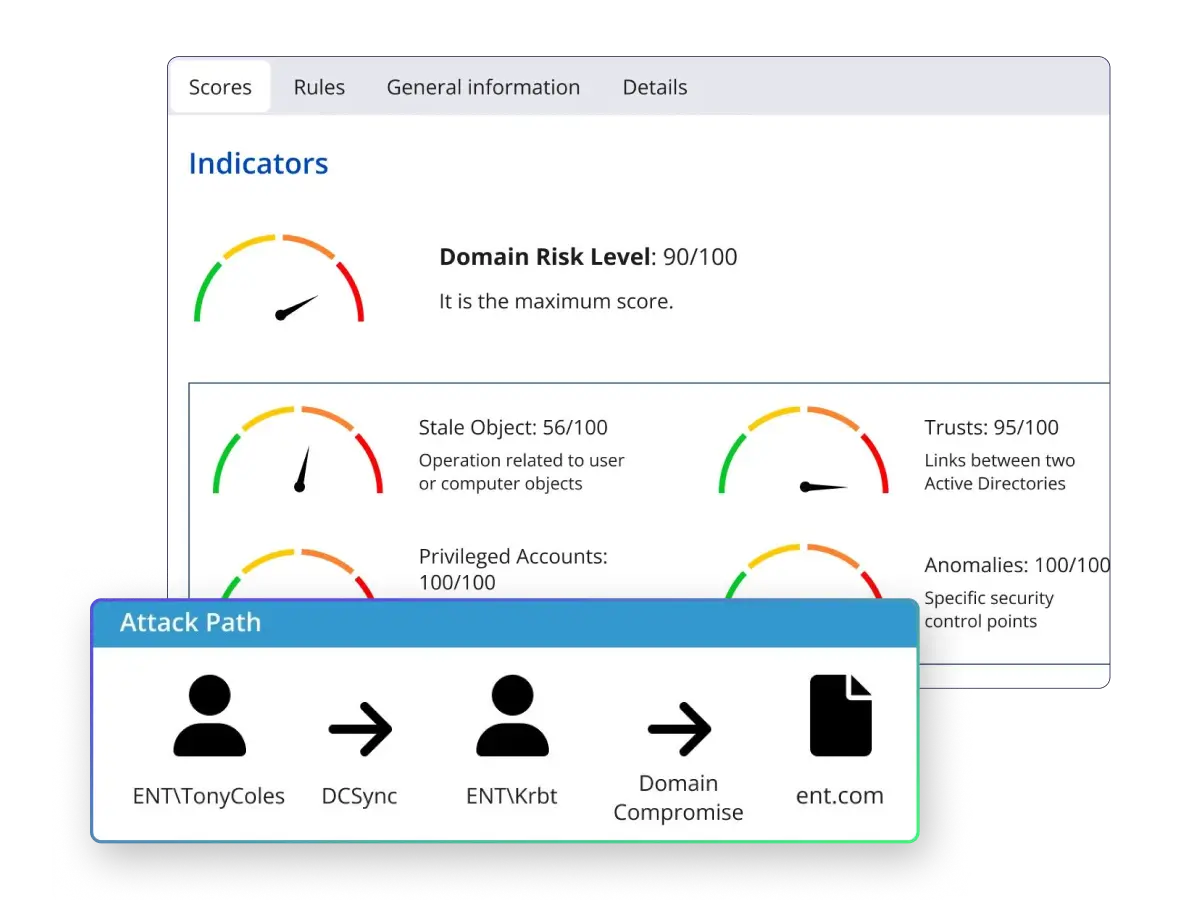
Identity is today’s primary attack vector but traditional tools lack visibility into identity systems and let adversaries move freely through hybrid AD
Concealed vulnerabilities
Misconfigurations expose attack pathways that go unnoticed until breaches are in progress.
Reactive threat detection
Threats are only addressed when they’re in progress and the damage has already been done.
Manual response delays
Slow response times give attackers escalation time while teams scramble to react.
Slow, manual recovery
Rebuilding your Active Directory can take days or weeks, prolonging downtime and increasing business impact.
Use cases
Stop identity attacks before they escalate with threat detection and response solutions
Advanced persistent threats
Detect identity-based threats like Kerberoasting, DCShadow, password spraying, and Golden Ticket in real time so you can stop them fast.
Insider threat detection
Spot unusual behavior and catch abuse from privileged or service accounts, like mass group changes or suspicious logins, with behavioral analytics.
Identity ransomware defense
Stop ransomware operators who exploit AD for lateral movement by isolating compromised accounts and protecting critical identity assets.
Non-human identities defense
Detect and contain misuse of non-human identities, such as service accounts, to close the hidden backdoors attackers use for persistence and stealthy access.
Business continuity assurance
Ensure AD and Entra ID can be rapidly restored after an attack, minimizing downtime and reducing the impact of ransomware or destructive incidents.
AD threat prevention
Detect and block unauthorized changes to Tier 0 groups like Domain Admins, Enterprise Admins, or DCSync attempts, stopping attackers before they seize AD control.
The Netwrix approach
Comprehensive ITDR security that shuts down the avenues of attack
Get in touch
Let’s talk security
An end-to-end identity threat detection and response solution
Netwrix ITDR solutions deliver comprehensive protection for your identity infrastructure. From proactive risk assessment and threat blocking to real-time detection and automated response, our solution stops attackers while ensuring your operations stay resilient. With continuous monitoring, instant attack neutralization, and fast recovery, you can confidently secure AD and Entra ID environments all from one simple solution.

Unified identity threat protection
Protect both AD and Entra ID from a single platform that eliminates tool sprawl and provides complete visibility across your environments.
Patented innovation
Patented technologies detect advanced threats and proactively block attacks across your Active Directory and Entra ID environments.
Remediation at scale
Bulk remediation of risks and misconfigurations across your identity infrastructure without relying on manual management.
Swift and seamless recovery
Restore operations quickly with automated forest recovery that cuts down disruption time and maintains seamless operations.
Identity Threat Detection & Response (ITDR) FAQs
Have questions? We’ve got answers.
See ITDR in action