Netwrix Auditor: The Microsoft Entra ID Auditing Tool
Put the brakes on identity-based attacks. Secure Microsoft Entra ID with panoramic change monitoring, sign-in tracking, and threat detection.
Read their Stories
Trusted by




































































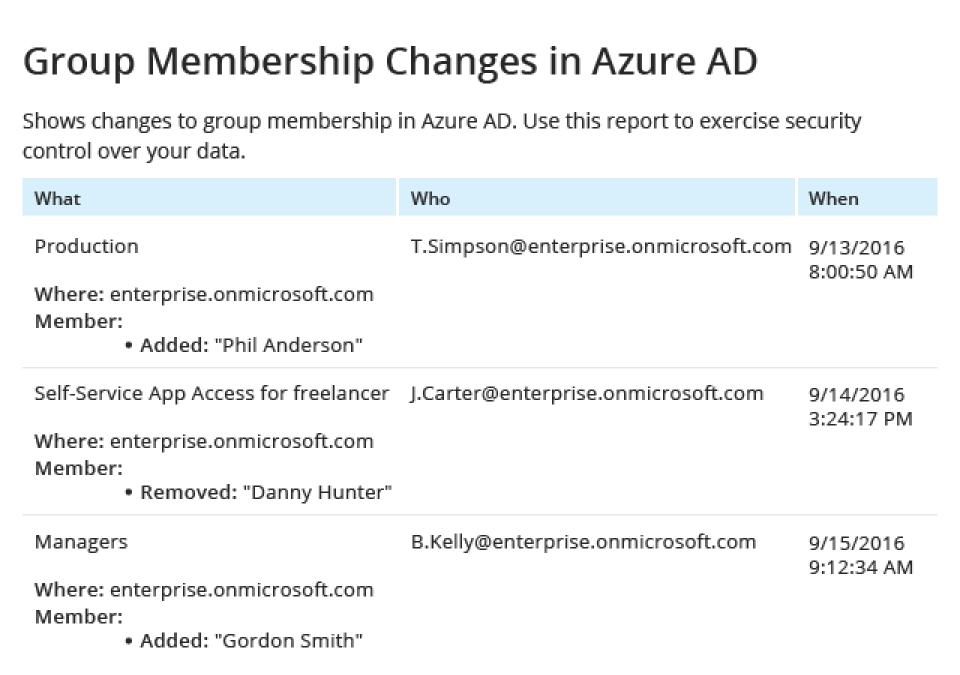
Complete Entra ID monitoring that gives you a unified view
Unlock unified hybrid visibility
Use our Microsoft Entra ID auditing tool alongside on-premises Active Directory for a single platform to detect threats that cross cloud boundaries.
Boost IT team productivity
Quickly uncover the root causes of problems that affect your data security and business continuity. Automate change control and reporting tasks.
Spot compromised accounts
Get visibility into security and configuration changes, such as privilege escalation, anomalous administrator activity, and more.
Pass audits with less effort
Preset-ready reports for PCI DSS, HIPAA, GDPR, and SOX compliance and an interactive search to quickly answer auditors’ questions.
Capabilities
Entra ID auditing with the intelligence you need to stay ahead of cloud-based identity threats
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.







