Kerberoasting Attack – How It Works and Defense Strategies
Kerberoasting is a sophisticated credential attack that exploits weaknesses in Kerberos authentication within Active Directory (AD) environments. The primary goal is credential theft and privilege escalation, leading to privilege escalation within a network.
Attribute | Details |
|---|---|
|
Attack Type |
Kerberoasting |
|
Impact Level |
High |
|
Target |
Businesses, Governments |
|
Primary Attack Vector |
Internal Network Access (via compromised domain user) |
|
Motivation |
Credential Theft, Privilege Escalation, Espionage |
|
Common Prevention Methods |
Strong Passwords, AES Encryption, gMSAs, MFA, Ticket Auditing |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High |
|
Ease of Execution |
Medium |
|
Likelihood |
Medium to High |
What is Kerberoasting?
Kerberoasting is a credential-based attack in which an adversary leverages valid domain credentials to request Kerberos service tickets associated with Service Principal Names (SPNs) from Active Directory. The attacker then extracts the encrypted password hashes from these tickets and cracks them offline, typically targeting weak or easily guessable passwords. The primary goal of this attack is to gain elevated privileges within AD, facilitating lateral movement, persistence, or data theft.
How Does Kerberoasting Work?
Kerberoasting exploits inherent weaknesses in Active Directory's Kerberos authentication process. Below is a detailed breakdown of each step involved in performing a Kerberoasting attack.
1. Compromise a standard domain user account
Attackers first need access to any valid domain user credentials, typically gained through phishing, credential stuffing, exploiting vulnerabilities, or initial footholds on compromised endpoints. Even low-privilege user accounts are sufficient to initiate the attack.
2. Enumerate service accounts with SPNs
Once inside the domain, attackers enumerate Service Principal Names (SPNs) registered to service accounts. Enumeration can be performed using tools such as PowerShell scripts, LDAP queries, or specialized enumeration tools like BloodHound. Service accounts with SPNs often have higher privileges, making them ideal targets.
3. Request Kerberos TGS tickets
With identified SPNs, attackers use their valid domain credentials to first obtain a Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC). This TGT is then used to legitimately request Kerberos Ticket Granting Service (TGS) tickets for the target service accounts. These TGS tickets are encrypted with the service account’s password hash and can be extracted for offline cracking. Tools like Impacket’s GetUserSPNs, or PowerShell-based scripts, automate this process and are commonly used in Kerberoasting attacks.
4. Export tickets
Attackers then export or extract these service tickets from memory or storage on the compromised system. Popular hacking tools such as Rubeus and Mimikatz simplify the extraction and export of these tickets into a format suitable for offline cracking.
5. Crack tickets offline
The exported TGS tickets contain encrypted hashes of service account passwords. Attackers attempt to crack these hashes offline using password-cracking tools like Hashcat, John the Ripper, or pre-generated rainbow tables. Weak passwords can be quickly compromised, exposing clear-text credentials.
6. Use recovered credentials to escalate privileges
Once attackers successfully crack the hashes and recover plaintext credentials, they can use these credentials to log in as privileged service accounts. This grants elevated privileges, enabling lateral movement across the network, access to sensitive information, and potential long-term persistence within the AD environment.
✱ Variant: Kerberoasting without pre-authentication
User accounts with pre-authentication disabled can be exploited without valid credentials
In some Active Directory configurations, pre-authentication may be disabled on user accounts, meaning attackers do not need valid credentials to request Kerberos tickets. This allows attackers to obtain encrypted hashes without first compromising an existing domain account.
Tools like Rubeus allow this bypass under specific AD misconfigurations
Attackers leverage tools such as Rubeus specifically designed to exploit this misconfiguration, requesting TGS tickets directly without prior authentication. This variant makes it even easier for attackers to gain access.
Attack Flow Diagram
The following diagram illustrates the sequential stages of a Kerberoasting attack, beginning with an attacker compromising a domain user account and culminating in privilege escalation within the Active Directory environment.
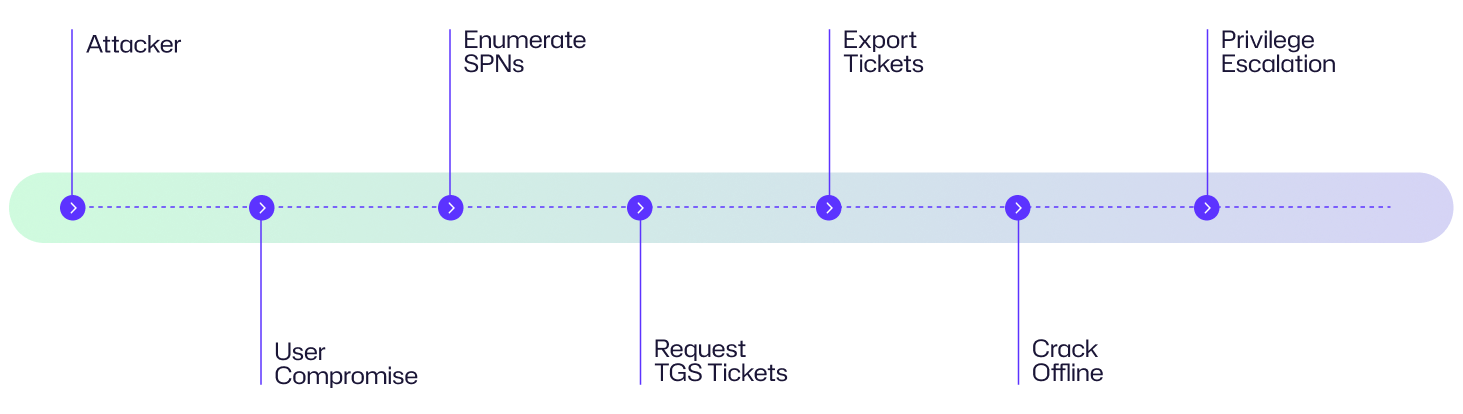
Here is Kerberoasting explained from an organization’s perspective.
An attacker gains access to XYZ Corp’s network by compromising a domain user via phishing. Once inside, they enumerate service accounts with SPNs and request Kerberos TGS tickets. Using tools like Rubeus, they export the tickets and crack a weak service account password offline. With the cracked credentials, they escalate privileges, access sensitive data, and move laterally, highlighting the risks of poor password hygiene and inadequate monitoring in AD environments.
Examples of Kerberoasting
The following are real-world examples of advanced threat groups that have effectively used Kerberoasting as part of their attack chains.
Case | Impact |
|---|---|
|
Akira Ransomware Group |
The Akira Ransomware Group commonly uses Kerberoasting to escalate privileges and maintain persistence in AD environments. By requesting and extracting service ticket hashes for service accounts, they crack these offline to retrieve credentials, often gaining access to high-privilege accounts. This tactic enables them to move laterally and deepen their foothold within the targeted network. |
|
FIN7 |
FIN7, a financially motivated threat group, has been observed using offline TGS cracking as part of its credential harvesting strategy. This technique involves exploiting the Kerberoasting attack method, specifically targeting service accounts in AD environments. This method aligns with FIN7’s broader tactics of leveraging legitimate system tools (like PowerShell, WMI, and native AD functions) to stay stealthy while expanding access for data theft or ransomware deployment. |
Consequences of Kerberoasting
A Kerberoast attack can have severe and far-reaching consequences for organizations. Once attackers obtain and crack service account credentials, they can escalate privileges and move laterally across the network. This not only enables data theft and system disruption but also exposes the organization to financial loss, reputational harm, legal penalties, and regulatory scrutiny.
Financial Consequences
Successful Kerberoasting attacks can give attackers access to privileged accounts, enabling data theft, financial fraud, or ransomware deployment. This often leads to direct financial losses, especially if the attackers steal or encrypt business-critical data. Organizations may be forced to pay millions in ransom demands to restore access. Additionally, breaches involving credential theft often trigger regulatory fines, particularly in regulated industries like finance and healthcare.
Operational Disruption
With access to privileged credentials, threat actors can disable critical systems, disrupt internal services, and interfere with IT operations. This can result in widespread downtime, halting business functions such as communication, data processing, or customer service. The recovery effort can be extensive and costly, often requiring manual resets, rebuilds of compromised domains, or complete AD remediation, which significantly impairs productivity.
Reputational Damage
A publicized breach involving Kerberoasting and AD compromise sends a clear message that the organization’s identity infrastructure was vulnerable. News coverage, regulatory disclosures, or leaked data can lead to a loss of customer trust, impact investor confidence, and damage relationships with partners or vendors. Rebuilding that trust may require costly PR efforts, customer outreach, or offering identity protection services.
Legal and Regulatory Impact
Kerberoasting attacks that lead to the exposure of personal or sensitive information may place the organization in violation of data protection regulations such as GDPR, HIPAA, or SOX. Regulatory bodies can impose hefty fines, and affected individuals or entities may pursue legal action. Furthermore, organizations may be subject to investigations or audits. In regulated sectors, repeated incidents can even lead to license revocation or sanctions.
Impact Area | Description |
|---|---|
|
Financial |
Credential theft, data exfiltration, ransomware |
|
Operational |
Network outages, halted services |
|
Reputational |
Erosion of public trust, customer churn |
|
Legal |
Compliance penalties, lawsuits over data breaches |
Common Targets of a Kerberoasting: Who is at risk?
Service Accounts with SPNs
SPNs allow Kerberos to associate a service instance with a logon account, making these accounts retrievable via TGS requests. Manually created service accounts, especially those with weak or non-rotated passwords, are prime targets. Attackers can request TGS tickets for these accounts and attempt offline cracking.
Common examples include accounts tied to SQL Server, IIS, SharePoint, Exchange, and backup solutions. These accounts often run critical services and may have elevated privileges, making them especially valuable.
High-Privilege Accounts
Accounts with administrative roles — such as Domain Admins, Enterprise Admins, or Schema Admins — are major targets. Once compromised, they provide unrestricted access across the domain. These accounts may also be linked to legacy services or scheduled tasks, increasing their exposure.
Accounts Using RC4 Encryption
Accounts configured to use RC4_HMAC_MD5 are far more vulnerable to Kerberoasting. This encryption algorithm is faster to crack compared to AES-based alternatives. Unfortunately, many legacy systems still default to or require RC4 for compatibility, leaving those accounts open to offline brute-force or dictionary attacks.
Stale or Unmonitored Accounts
Older accounts that are no longer in active use or those flagged with “password never expires” pose a persistent risk. These accounts may go unnoticed, particularly in large environments with poor account lifecycle management. Because attackers can crack the credentials at their own pace offline, even an unused but still-valid account can become an entry point for lateral movement or privilege escalation.
Risk Assessment
Understanding the risk posed by Kerberoasting is essential for evaluating the overall security posture of an AD environment.
Risk Factor | Level |
|---|---|
|
Damage |
Very High
|
|
Ease of Execution |
Medium
|
|
Likelihood |
Medium to High
|
How to Prevent Kerberoasting
Preventing Kerberoasting requires a combination of strong password policies, secure account configurations, and proper encryption settings. Proactive monitoring and automated account controls further strengthen defenses against this common attack vector.
Password & Account Hygiene
Since a Kerberoasting attack relies on offline password cracking, increasing password complexity and limiting password age directly reduces the attacker’s success rate.
- Use Long, Complex PasswordsService accounts, especially those with SPNs, should use passwords that are at least 25 characters long, with a mix of uppercase, lowercase, numbers, and special characters. Length and randomness significantly slow down brute force cracking attempts.
- Rotate Passwords RegularlyService account passwords should be rotated at least annually, or more frequently in high-risk environments. This limits the window of opportunity for an attacker to crack a password offline.
- Audit and Enforce Expiration PoliciesRegularly audit password age across all service accounts. Avoid configurations with the “password never expires” flag, which makes accounts persistent targets. Enforce strict expiration policies through Group Policy or dedicated identity tools.
- Use gMSAs or dMSAsReplace manually managed service accounts with Group Managed Service Accounts (gMSAs) or Distributed Managed Service Accounts (dMSAs). These accounts automatically manage password changes, support complex credentials, and reduce human error — greatly decreasing Kerberoasting exposure.
Encryption Configuration
Configuring strong encryption for Kerberos authentication is critical in mitigating Kerberoasting risks, as weaker encryption algorithms like RC4 are far easier to crack.
- Enforce AES 128/256-bit EncryptionConfigure AD and domain-joined systems to use AES128_HMAC or AES256_HMAC for Kerberos ticket encryption. These algorithms are significantly more resistant to brute-force attacks than RC4 and are supported in modern Windows environments.
- Manually Disable RC4Although Microsoft has deprecated RC4_HMAC_MD5, it may still be enabled for compatibility, especially in legacy environments. Review Group Policy and account-level settings to explicitly disable RC4 where possible. This helps ensure that attackers cannot request tickets encrypted with weak ciphers.
- Update Passwords After Policy ChangesEncryption settings tied to Kerberos tickets only take effect after an account’s password is changed. Therefore, after enforcing new encryption policies, it is essential to reset passwords for existing service accounts.
Account Scoping
Limiting the exposure and capabilities of service accounts is a proactive way to reduce the attack surface available for Kerberoasting.
- Remove SPNs from User AccountsAvoid assigning Service Principal Names (SPNs) to standard user accounts, as these make them eligible for Kerberoasting. Instead, use dedicated service accounts or Managed Service Accounts (gMSAs/dMSAs) to isolate service functions from user identity.
- Restrict to Non-Interactive LogonsConfigure service accounts to disallow interactive logons using Group Policy or AD settings. This prevents attackers from using compromised credentials for direct login, limiting lateral movement after a successful Kerberoasting attempt.
- Limit Access Scope by Host and ServiceScope service account permissions narrowly to the specific hosts and services they support. Avoid granting unnecessary domain-wide privileges. Applying principle of least privilege ensures that even if a service account is compromised, the impact is contained.
Privileged Access Management (PAM)
Implementing Privileged Access Management (PAM) is a critical control for reducing the risk and impact of Kerberoasting by securing how privileged accounts are used, stored, and monitored.
- Vault and Rotate Privileged CredentialsUse a PAM solution to vault service account and administrative credentials, eliminating hardcoded passwords and manual management. These tools can automatically rotate passwords on a defined schedule or after each use.
- Monitor Account Usage with Session Recording and AnalyticsPAM platforms provide session monitoring and recording, allowing security teams to audit privileged activity in real time or retrospectively. Behavioral analytics can detect anomalies such as unusual access patterns, lateral movement, or off-hours usage, which may indicate Kerberoasting-related activity.
Netwrix Support
Netwrix offers strong support to defend against Kerberoasting attacks through its Active Directory and identity protection tools. Here are the top two Netwrix products that help prevent or detect Kerberoasting.
Netwrix Access Analyzer
This tool actively scans AD to identify service accounts vulnerable to Kerberoasting, especially those with SPNs and weak encryption settings such as RC4 or DES. A dedicated AD_KerberoastingRisk job produces a clear risk dashboard with customizable thresholds (for example, flagging AES 128, expired passwords, or "password never expires" flags), and highlights accounts that need remediation. By pinpointing high-risk accounts before an attack occurs, security teams can proactively tighten account configurations, update passwords, and disable problematic SPNs.
Run Netwrix Access Analyzer for free and get a clear view of privilege exposure instantly.
Netwrix Threat Prevention
Netwrix Threat Prevention offers real-time monitoring and enforcement at the source, rather than relying solely on Windows logs. It can detect suspicious Kerberos activity, such as abnormal TGS requests or SPN assignments to privileged accounts, and automatically block such actions or raise alerts in real time. With policies that prevent high-risk changes and contextual alerting, it stops Kerberoasting attempts in their tracks and escalates alerts for further investigation.
Try Netwrix Threat Prevention and get immediate alerts on risky activity before it impacts your business.
Detection, Mitigation and Response Strategies
Kerberoasting attacks often go unnoticed until significant damage is done. A strong defense requires effective detection mechanisms, rapid response protocols, and long-term mitigation strategies.
Detection
Here are some great tips for detecting Kerberoasting early in the attack chain.
- Monitor Event IDs 4769 and 4770 for TGS RequestsEvent ID 4769 (TGS request) and 4770 (TGS ticket renewal) are key indicators of Kerberos activity. A spike in 4769 events, especially from a single user querying multiple SPNs, may signal Kerberoasting.
- Flag RC4 Encryption Use (Type 0x17)Kerberos tickets encrypted using RC4_HMAC_MD5 (type 0x17) are far easier to crack. Monitoring for this encryption type can help identify high-risk accounts or active attempts to exploit weak ticket encryption.
- Detect Abnormal TGS Volumes or PatternsUnusual volumes of TGS requests — especially targeting multiple service accounts in a short window — can indicate ticket harvesting. Monitoring for such anomalies is critical for Kerberoasting detection.
- Use Honeypots/Honeytokens to bait attackersDeploy decoy service accounts with SPNs and monitor for access attempts. Any interaction with these accounts is a strong indicator of malicious reconnaissance or Kerberoasting.
- Configure UBA and SIEM for Baseline AnalyticsUse User Behavior Analytics (UBA) and SIEM platforms to establish normal Kerberos request behavior. Flag deviations from this baseline, such as new users requesting TGS tickets or off-hours activity.
Response
Following are some effective response strategies on detecting Kerberoasting.
- Disable and Reset Affected Accounts ImmediatelyIf a Kerberoasted account is identified, disable it and force a password reset to prevent continued unauthorized access.
- Review AD Logs for Lateral MovementExamine logs for signs of account misuse, privilege escalation, or access to sensitive systems. Focus on login events, group membership changes, and service access patterns.
- Invalidate Existing Tickets and Force LogoutForce all users to re-authenticate by invalidating Kerberos tickets using klist purge or restarting services, ensuring stolen credentials no longer grant access.
Mitigation
The following strategies support effective Kerberoasting mitigation.
- Implement Zero Trust PrinciplesAdopt a Zero Trust model where no account or system is inherently trusted. Enforce least privilege, continuous validation, and access segmentation to contain damage from credential-based attacks.
- Use Deception Technologies (Decoy SPNs)Create fake SPNs or decoy service accounts to detect scanning and Kerberoasting attempts. These deception assets trigger alerts when accessed, giving early warning of malicious behavior.
Industry-Specific Impact
The impact of a Kerberoasting attack can vary across industries, depending on the nature of systems and data at risk. In sectors like healthcare, finance, and retail, compromised service accounts can lead to regulatory violations, financial losses, and operational disruption.
Industry | Impact |
|---|---|
|
Healthcare |
|
|
Finance |
|
|
Retail |
Retail networks commonly use service accounts to support point-of-sale (POS) systems, inventory control, and e-commerce platforms.
|
Attack Evolution & Future Trends
Kerberoasting is evolving with stronger tools, automation, and advanced tactics. While Microsoft hardens Kerberos (for example, with RC4 deprecation), attackers are improving their ability to crack tickets quickly and use them in complex, multi-stage attack chains. Staying aware of these trends is key to effective defense.
RC4 deprecation in Windows 11 24H2 and Server 2025
Microsoft is officially deprecating RC4_HMAC_MD5 encryption for Kerberos in upcoming releases like Windows 11 24H2 and Windows Server 2025. This move reduces exposure to offline cracking, as RC4 is far easier to brute-force than AES-based encryption. While this is a major security improvement, organizations using legacy systems may still be at risk if they fail to update encryption policies and rotate passwords post-upgrade.
GPU cracking tools now guess >100B passwords/sec
Modern GPU-based cracking tools (for example, Hashcat, John the Ripper) can now exceed 100 billion guesses per second, drastically reducing the time needed to crack weak service account passwords. Combined with dictionary attacks and precomputed hash tables, even moderately complex passwords can be broken in minutes. This trend makes it imperative for organizations to enforce very long and complex passwords, especially on accounts with SPNs, and to detect and limit RC4 usage.
Use of AI + automation in cracking tools
Attackers are beginning to incorporate AI and automation into password cracking workflows. Machine learning models can predict password patterns, adapt cracking strategies based on previous successes, and even identify naming conventions across enterprise accounts. Automation platforms streamline the process of ticket extraction, hash parsing, and credential brute-forcing, making attacks faster and more scalable. This increases the threat posed even by less sophisticated actors using prebuilt tools.
Kerberoasting increasingly used in multi-stage attack chains
Kerberoasting is now frequently used as part of multi-stage intrusions. After cracking a service account, attackers may:
- Create Golden Tickets for persistent domain access.
- Use Overpass-the-Hash to impersonate accounts without knowing the password.
- Launch Pass-the-Ticket attacks to move laterally across systems.
These chained attacks often bypass standard detection methods and require advanced correlation across authentication events.
Key Statistics & Infographics
Here is a bar chart summarizing key statistics related to Kerberoasting and credential security risks. The chart highlights areas where organizations are most vulnerable, including password hygiene, account management practices, and the rapid advancement of cracking technology.
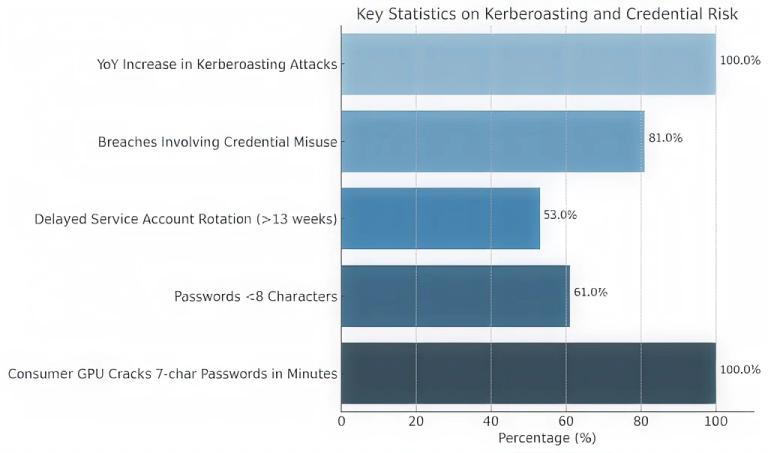
100% YoY increase in Kerberoasting attacks (IBM X-Force 2023)
According to the IBM X-Force Threat Intelligence Report 2023, Kerberoasting attacks have doubled year over year, showing a 100% increase in observed activity compared to the previous reporting period. This sharp rise reflects the growing popularity of Kerberoasting among both nation-state actors and cybercriminal groups due to its:
- Low detection profile (uses native Kerberos protocol).
- No need for elevated privileges — any authenticated domain user can launch the attack.
- High payoff — cracked service account credentials often lead to domain-level compromise.
The report attributes this growth to a combination of factors, including the increasing use of automated attack frameworks, the ease of execution with publicly available tools like Rubeus and Impacket, and the lack of strong password enforcement in many environments.
81% of breaches involve credential misuse
This statistic, widely cited in industry reports such as Verizon's Data Breach Investigations Report (DBIR), underscores the critical role of compromised credentials in modern cyberattacks. Specifically, 81% of data breaches involve the misuse of usernames, passwords, or other forms of identity access — either stolen, phished, guessed, or cracked. Note that:
- Kerberoasting directly supports credential misuse.
- Once credentials are compromised, attackers can blend in with legitimate users, making detection difficult.
- Misused credentials often serve as the entry point for ransomware, data exfiltration, and persistent access.
53% of organizations delay service account password rotation >13 weeks
A recent industry survey found that 53% of organizations wait more than 13 weeks (over three months) to rotate passwords for service accounts, and some don't rotate them at all. These accounts often have elevated or persistent access to critical systems (for example, databases, backups, ERP), making them prime targets for Kerberoasting attacks. This matters because:
- Static passwords give attackers more time to crack service ticket hashes offline using tools like Hashcat.
- Long password lifecycles often correlate with “password never expires” flags, increasing exposure.
- Kerberos encryption types are tied to account password changes. Without regular rotation, weak algorithms like RC4 may remain in use, even after policy updates.
Operational Challenges:
- Organizations often delay rotation due to fear of downtime, lack of automation, or unclear ownership of service accounts.
- Manual tracking and updating is error-prone and hard to scale in large environments.
It is recommended to use Group Managed Service Accounts (gMSAs) or Privileged Access Management (PAM) solutions to automate password rotation without affecting service availability.
61% use passwords <8 characters long
Despite years of security awareness campaigns, 61% of users or service accounts in enterprise environments still use passwords that are shorter than 8 characters, based on findings from internal audits and industry surveys. This poses a significant risk, particularly in the context of Kerberoasting.
- Short passwords have fewer possible combinations, making them susceptible to brute-force and dictionary attacks, especially when encrypted with RC4.
- Modern password-cracking tools using consumer-grade GPUs can break <8-character passwords in seconds to minutes.
- Many organizations lack enforcement policies for minimum password length or complexity on service accounts.
Consumer GPUs crack 7-character passwords in minutes
Modern consumer-grade GPUs, like NVIDIA's RTX or AMD's Radeon series, have made offline password cracking highly efficient and accessible. A high-end GPU can attempt billions of password guesses per second, enabling it to brute-force a 7-character password in just a few minutes, especially when the password lacks complexity.
Why This Matters for Kerberoasting:
- When attackers extract service ticket hashes via Kerberoasting, they can crack them offline without alerting defenders.
- 7-character passwords, particularly those using only lowercase letters or common words, are easily defeated using tools like Hashcat or John the Ripper.
- This makes weak service account passwords a high-value target and a low-effort win for attackers.
Final Thoughts
Kerberoasting remains one of the most powerful and stealthy attack techniques targeting Active Directory environments — often undetected until significant damage is done. Effective defense requires a holistic approach that includes strong encryption standards, robust credential hygiene, and proactive monitoring. By combining identity protection, advanced behavioral analytics, and deception tactics like honeytokens and decoy SPNs, organizations can not only detect Kerberoasting attempts early but also disrupt them before they escalate. A layered, intelligence-driven defense strategy is essential to staying ahead of this persistent threat.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
