DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
A DCShadow attack exploits Active Directory by stealthily creating or manipulating domain controllers, giving attackers full control over an environment. This technique has become a growing threat as it enables attackers to bypass traditional defenses and gain persistent access to critical systems.
Attribute | Details |
|---|---|
|
Attack Type |
Post-exploitation / Persistence / Privilege Escalation |
|
Impact Level |
Critical |
|
Target |
Microsoft Active Directory (Domain Controllers, AdminSDHolder, AD objects) |
|
Primary Attack Vector |
Abuse of AD replication protocol (MS-DRSR) via Mimikatz's lsadump::dcshadow |
|
Motivation |
Establish persistence, escalate privileges, avoid detection, maintain long-term domain control |
|
Common Prevention Methods |
|
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High |
|
Ease of Execution |
Medium |
|
Likelihood |
Medium |
What is DCShadow?
DCShadow is an advanced post-exploitation technique used in Active Directory (AD) attacks. It was first publicly disclosed by security researchers Benjamin Delpy (creator of Mimikatz) and Vincent Le Toux.
The DCShadow attack technique is part of the lsadump module in Mimikatz, a post-exploitation tool. It allows an adversary with Domain Admin or Enterprise Admin privileges to register a rogue domain controller (DC) within the AD environment. Once registered, the attacker can inject arbitrary changes directly into the AD database (NTDS.dit). The attack is used to stealthily modify sensitive attributes such as:
- SIDHistory
- userAccountControl
- adminCount
- Group memberships
These changes are propagated through AD’s native replication mechanism, which treats them as legitimate updates coming from a trusted DC. Because of this, normal auditing and security logging mechanisms are bypassed, making detection difficult.
New Insight
DCShadow does not exploit a software flaw or vulnerability; instead, it leverages the inherent trust and replication mechanisms built into Active Directory's architecture. For this reason, it cannot be patched. Mitigating DCShadow therefore requires strict operational controls.
How Does DCShadow Work?
Prerequisites
Before launching DCShadow, the attacker must have:
- SYSTEM-level privileges on a domain-joined machine (not necessarily a DC).
- Domain Admin or Enterprise Admin credentials to interact with the AD replication process.
- Access to Mimikatz, which provides the lsadump::dcshadow module.
- A good understanding of AD replication mechanics.
Attack Vector
DCShadow works by allowing an attacker to simulate a rogue domain controller and inject unauthorized changes directly into AD via the replication process. After gaining SYSTEM privileges and Domain Admin rights, the attacker uses tools like Mimikatz to register the rogue DC, craft modifications to AD attributes, and push those changes to the AD database. Once complete, the rogue DC is removed to erase traces. Over the next several months, the attacker uses the backdoor account to access systems and collect sensitive data — all while bypassing conventional SIEM alerts and AD audit logs.
Here is a step-by-step walkthrough of the attack process.
How Does DCShadow Work?
Prerequisites
Before launching DCShadow, the attacker must have:
- SYSTEM-level privileges on a domain-joined machine (not necessarily a DC).
- Domain Admin or Enterprise Admin credentials to interact with the AD replication process.
- Access to Mimikatz, which provides the lsadump::dcshadow module.
- A good understanding of AD replication mechanics.
Attack Vector
DCShadow works by allowing an attacker to simulate a rogue domain controller and inject unauthorized changes directly into AD via the replication process. After gaining SYSTEM privileges and Domain Admin rights, the attacker uses tools like Mimikatz to register the rogue DC, craft modifications to AD attributes, and push those changes to the AD database. Once complete, the rogue DC is removed to erase traces. Over the next several months, the attacker uses the backdoor account to access systems and collect sensitive data — all while bypassing conventional SIEM alerts and AD audit logs.
Here is a step-by-step walkthrough of the attack process.
1. Elevate to SYSTEM Privileges
The attacker first compromises a domain-joined machine and escalates privileges to SYSTEM using tools like Mimikatz or other privilege escalation techniques.
Using Mimikatz to elevate privileges to SYSTEM:
privilege::debug
!+
!ProcessToken
This allows the process to interact with the Local Security Authority (LSA) and register replication services.
2. Register the Rogue Domain Controller
Using Mimikatz's lsadump::dcshadow module, attackers can temporarily register the compromised, domain-joined machine as a rogue DC. This is achieved by programmatically:
- Modifying Service Principal Names (SPNs) to make the machine recognizable as a DC.
- Modifying msDS-HasDomainNC, msDS-HasFullReplicaNCs, and other replication-related attributes.
- Creating necessary AD objects like NTDS Settings under the Configuration partition.
3. Prepare Attribute Modifications
Attackers prepare changes to AD objects, such as:
- Adding SIDHistory to gain permissions via old SIDs.
- Modifying adminCount to evade protections.
- Adding accounts to sensitive groups like Domain Admins.
These changes are staged using Mimikatz commands, such as:
lsadump::dcshadow /object:User1 /attribute:SIDHistory /value:S-1-5-21-...
4. Push Changes via Replication
The attacker uses the following command to push the staged changes to Active Directory via standard replication protocols, causing the real domain controllers to accept the changes as if they came from a legitimate DC.
lsadump::dcshadow /push
5. Clean Up Traces
Once replication completes, the attacker removes all traces of the rogue DC by:
- Deleting the SPNs
- Removing NTDS Settings
- Restoring original system configurations
This reduces the chance of detection during forensic analysis.
New Insight
Attackers often target critical AD components like AdminSDHolder, KRBTGT, and Group Policy Objects (GPOs) for persistent control and widespread compromise.
- Modifying AdminSDHolder allows them to maintain elevated privileges by enforcing security settings on high-value accounts.
- KRBTGT manipulation enables Golden Ticket attacks, granting indefinite access.
- Altering GPOs lets attackers push malicious configurations or scripts to all domain-joined systems.
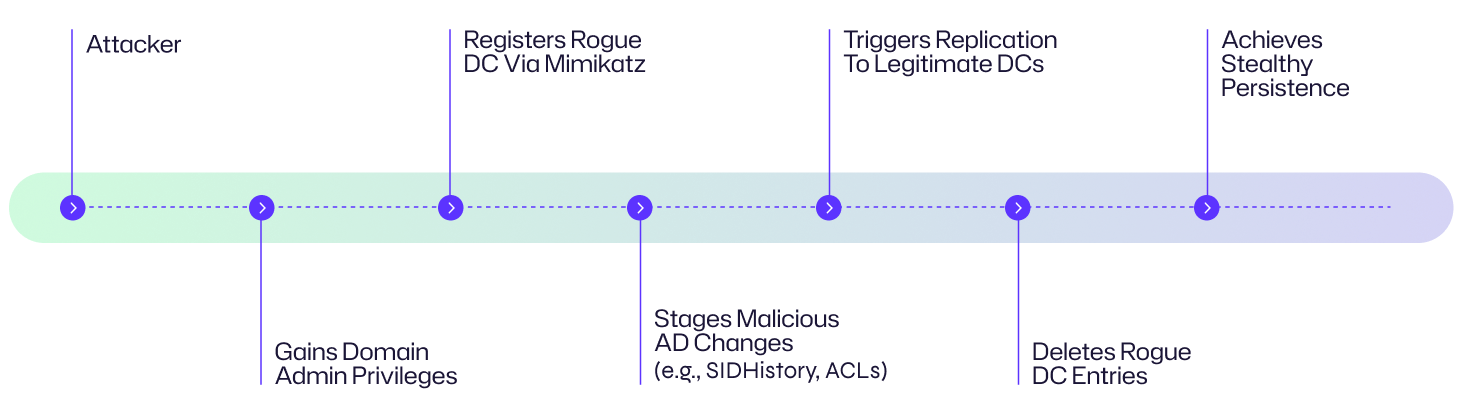
Attack Flow Diagram
The DCShadow attack flow illustrates how a threat actor can exploit legitimate AD replication mechanisms to inject unauthorized changes — such as modifying user attributes or group memberships — into the AD database, enabling long-term, covert control over the domain.
Here is a visual concept of the attack.
Let’s look at an example from an organization’s perspective.
In a mid-sized healthcare organization, an attacker exploits a VPN vulnerability to gain access and escalates privileges to capture Domain Admin credentials. Using Mimikatz, they register a compromised machine as a rogue DC and push malicious changes to AD, such as adding a stealthy admin account via SIDHistory. These changes are replicated across the domain without triggering alerts. After cleaning up traces of the rogue DC, the attacker maintains long-term, covert access and exfiltrates sensitive patient data over time, undetected by standard security tools.
Examples of DCShadow Attacks
By understanding real-world examples of DCShadow attacks, security professionals can gain insight into how attackers abuse replication mechanisms, what indicators to look for, and how to build effective defenses against such threats.
Case | Impact |
|---|---|
|
UNC2452 (SolarWinds-related, 2020–2021) |
The advanced persistent threat (APT) group UNC2452, attributed to the SolarWinds supply chain compromise, is suspected of leveraging DCShadow techniques during their post-exploitation phase. Reportedly, attackers manipulated AD permissions and replication metadata, likely through DCShadow. By injecting changes directly into the AD replication process, UNC2452 managed to establish stealthy, long-term persistence while evading conventional monitoring tools. |
|
APT29 / Nobelium (2021) |
In 2021, the Russian-linked threat group APT29 (also known as Nobelium), was suspected of employing DCShadow techniques to compromise cloud-hybrid AD environments. Following initial access — often achieved through spear-phishing, token theft, or exploitation of federation services — APT29 reportedly leveraged DCShadow-like methods to plant hidden accounts and modify SIDHistory attributes. These changes allowed the group to escalate privileges and maintain long-term access across on-premises AD and Microsoft Entra ID infrastructures. |
|
TrickBot (2020) |
In 2020, the notorious banking Trojan and malware framework TrickBot expanded its capabilities beyond financial fraud to include AD manipulation techniques using Mimikatz’s DCShadow module. Between July and October 2020, multiple cybersecurity forms, including DFIR Report, SentinelOne, and Cybereason documented TrickBot-led intrusions where DCShadow was explicitly used. These attacks targeted enterprise networks in healthcare, education, and manufacturing sectors, often leading to ransomware deployment. |
|
Red Team Simulation – BlueHat IL (2018) |
The Red Team Simulation at BlueHat IL 2018 marked the original proof-of-concept demonstration of the DCShadow attack, presented by security researchers Vincent Le Toux and Benjamin Delpy (creator of Mimikatz). This showcased how an attacker could register a rogue DC and silently push unauthorized changes into AD using legitimate replication protocols, without triggering traditional event logs or detection mechanisms. This simulation laid the foundation for real-world abuse of DCShadow. |
Consequences of a DCShadow Attack
DCShadow attacks represent a high-impact threat to Active Directory environments, leading to serious consequences.
Complete Domain Compromise
By exploiting replication mechanisms, DCShadow allows attackers to impersonate a legitimate DC and inject arbitrary changes into AD. This gives them the ability to alter permissions, create privileged accounts, and modify security descriptors. Once executed successfully, the attacker owns the domain in the same way a domain admin would.
Invisibility from SIEMs and Log-Based Monitoring
A DCShadow attack can operate beyond the visibility of conventional monitoring tools. Since the attack mimics legitimate DC replication using protocols like MS-DRSR, changes are made at the replication layer and do not trigger standard event logs. As a result, even sophisticated SIEM platforms and log-based detection tools may miss the unauthorized modifications, giving attackers freedom to operate undetected.
Persistence Beyond Admin Password Resets
Even if defenders reset administrator passwords or remove known backdoors, attackers using DCShadow may have already embedded persistent changes directly into AD, such as modified replication rights or rogue service principals. These stealthy footholds are difficult to trace and may survive traditional remediation efforts. Hence, attackers can return even after incident response actions are taken.
Potential to Escalate Across Domain Trusts
In environments with multiple domains or trust relationships between forests, DCShadow attacks can be used to abuse those trust paths. By injecting changes that affect trusted accounts or altering trust-related attributes, attackers can escalate privileges across domains, moving laterally and compromising additional segments of the infrastructure with minimal resistance.
Full Privilege Escalation and Infrastructure Backdooring
With the ability to grant or modify high-level AD permissions silently, DCShadow enables attackers to conduct full privilege escalation. They can also backdoor the infrastructure by implanting persistent privileges, manipulating sensitive AD objects, or modifying ACLs and group memberships in a way that ensures long-term covert access. These changes are difficult to audit or revert without forensic-level investigation.
Privilege Abuse in Hybrid Environments
In hybrid identity environments, where on-premises AD is synchronized with Microsoft Entra ID using tools like Microsoft Entra Connect, a DCShadow attack can have cascading consequences beyond the local domain. If an attacker compromises the on-premises AD and makes unauthorized changes, those modifications are automatically synchronized to Microsoft Entra ID, depending on the configuration. This may enable attackers to gain elevated roles in Microsoft 365, Microsoft Entra subscriptions, or other federated SaaS applications.
Complete Forest-Level Compromise
When combined with techniques such as Golden Ticket or Pass-the-Ticket, a DCShadow attack can escalate into a complete forest-level compromise. This powerful combination allows attackers to forge Kerberos tickets while silently altering AD replication to maintain persistence and elevate privileges. In such scenarios, the integrity of the entire AD forest is jeopardized, often leaving a full forest rebuild as the only reliable remediation option.
Consequences on Key Business Areas
A DCShadow attack can have consequences across critical business dimensions.
Impact | Description |
|---|---|
|
Financial |
A successful DCShadow attack can lead to significant financial losses that may stem from:
|
|
Operational |
DCShadow can cripple IT infrastructure and day-to-day operations.
|
|
Reputational |
Breaches involving advanced AD exploitation can severely damage an organization’s reputation.
|
|
Legal/Regulatory |
DCShadow attacks can lead to serious legal and compliance consequences, including regulatory penalties and legal action.
|
Common Targets of a DCShadow Attack: Who is at Risk?
While any Active Directory environment can be at risk of a DCShadow attack, certain types of organizations are more vulnerable due to their architecture, operational scale, or the sensitivity of their data.
Large Enterprises with Complex AD Environments
Enterprises with expansive and multi-tiered AD structures often have numerous domain controllers and trust relationships, which can provide attackers with multiple entry points and replication paths to exploit.
Organizations with Excessive Privileged Accounts
Environments where privileged access is poorly controlled or where admin accounts are overly abundant present an easy target. Attackers can more easily compromise such accounts to initiate DCShadow attacks and maintain persistence.
Companies with Inadequate Monitoring & Logging
Businesses that lack comprehensive AD replication monitoring, SIEM integration, or anomaly detection mechanisms are at a higher risk. DCShadow attacks often bypass traditional logs, while visibility is essential for early detection.
Government Agencies and Critical Infrastructure
Public sector entities and operators of critical national infrastructure (CNI) are frequent targets of nation-state actors who may use DCShadow as part of advanced persistent threat (APT) campaigns to maintain covert access over long periods.
Organizations with Inter-Forest Trusts
Companies that maintain multiple AD forests with trust relationships are especially vulnerable, as a compromise in one forest can be leveraged to escalate privileges across others using DCShadow techniques.
Industries with Valuable Intellectual Property (IP)
Sectors such as aerospace, pharmaceuticals, and technology that house sensitive R&D data are high-value targets. Attackers may use DCShadow to stealthily maintain access while exfiltrating IP without triggering alerts.
Hybrid/Multi-Cloud Environments
Organizations with integrated on-prem AD and Microsoft Entra ID environments are susceptible to extended impact. DCShadow can be used to manipulate local AD, which then propagates unauthorized changes into the cloud, expanding the scope of compromise.
Risk Assessment
Assessing the risk of DCShadow attacks requires analyzing their likelihood, potential impact, the advanced nature of the techniques used, challenges in detection, and the severity of the consequences they may cause.
Risk Factor | Level |
|---|---|
|
Potential Damage |
Very High
|
|
Ease of Execution |
Medium
|
|
Likelihood |
Medium
|
How to Prevent DCShadow Attacks
Preventing DCShadow attacks requires a layered defense strategy focused on limiting privileged access, securing Active Directory configurations, and monitoring for unauthorized replication activities. The following best practices help reduce the attack surface and improve detection and response capabilities.
Minimize Domain Admin and Enterprise Admin Membership
Limit the number of users with highly privileged accounts, such as Domain Admin or Enterprise Admin rights, as DCShadow attacks require such privileges to succeed.
- Use Privileged Access Management (PAM) to assign elevated permissions only when necessary.
- Audit and remove inactive or unnecessary admin accounts.
- Use just-in-time (JIT) access models to reduce persistent administrative rights and limit exposure.
Protect High-Value Accounts with Tiered Access Models
Implement a tiered administrative model (Tier 0/1/2) to isolate high-privilege accounts, reducing the risk of lateral movement and privilege escalation.
- Tier 0: Domain controllers, domain admin accounts – isolated completely
- Tier 1: Server/workstation admin accounts
- Tier 2: Standard user environments
Use dedicated accounts and workstations for each tier to avoid credential leakage across levels.
Implement Secure Admin Workstations (SAWs)
Use hardened, dedicated workstations for administrative tasks to reduce the risk of credential theft and prevent tools like Mimikatz from being executed on exposed endpoints.
- Prohibit internet browsing and email access from SAWs.
- Enable full-disk encryption, disable local admin rights, and enforce multi-factor authentication (MFA).
- Monitor for unauthorized software or access attempts.
Restrict Access to Modify AD Schema and Configuration
Apply strict permissions to control who can modify directory schema or replicate changes, as DCShadow requires such rights to register rogue domain controllers.
- Restrict "Replicating Directory Changes" and "Replicating Directory Changes All" permissions.
- Disable unneeded schema admin roles and monitor for attempts to re-enable them.
- Use Group Policy to limit rights to AD schema or Configuration naming contexts.
Constrain SPN Creation and Computer Object Rights
Misconfigured permissions on Organizational Units (OUs) can allow attackers to create rogue machines and register SPNs.
- Prevent low-privileged or standard users from registering Service Principal Names (SPNs) or creating/joining computer objects to the domain without oversight.
- Audit and restrict ms-DS-MachineAccountQuota, which controls how many machines a user can join to the domain.
- Monitor SPN registrations for anomalies using tools like ADRecon or BloodHound.
Use Host-Based Firewalls and Network Segmentation
Proper segmentation and firewalling prevent lateral movement and replication abuse.
- Isolate domain controllers from the rest of the network.
- Only allow necessary RPC and LDAP replication ports between legitimate domain controllers.
- Block inbound replication traffic from unauthorized hosts.
- Implement ACLs on network devices to limit communication to/from domain controllers.
Audit AD Changes and Replication Traffic
Monitor and log directory changes, especially replication activities, schema modifications, or unauthorized changes to sensitive objects. Look for unusual events like:
- Unauthorized NTDS Settings modifications.
- Spontaneous changes to the Server-Reference attribute.
Use Event IDs (for example, 4662 for object permissions changes) and Directory Services logs for auditing.
Deploy Real-Time Threat Detection Tools
Modern security solutions can detect indicators of DCShadow activity.
- Microsoft Defender for Identity can detect abnormal replication behavior and privilege escalations.
- SIEM integrations (e.g., Splunk, Sentinel) can correlate logs from AD, endpoints, and network.
- Use honeypot domain controllers to detect rogue replication attempts.
Isolate and Monitor Mimikatz & PowerShell Usage
DCShadow attacks typically involve Mimikatz and advanced PowerShell scripting.
- Use AppLocker or Windows Defender Application Control (WDAC) to prevent unapproved script execution.
- Implement PowerShell Constrained Language Mode and enable script block logging.
- Monitor for known YARA signatures or behavior-based detections associated with Mimikatz.
Conduct Regular Security Audits and Hygiene Checks
Perform regular reviews of AD permissions, group memberships, and audit policies to identify misconfigurations or privilege escalations before attackers can exploit them.
- Run AD Security Assessments using tools like PingCastle, ADACLScanner, or Purple Knight.
- Review GPOs, delegated permissions, group memberships, and privileged access reports.
- Test incident response procedures related to AD attacks to ensure readiness.
Netwrix Support
Netwrix provides powerful tools to detect and mitigate DCShadow attacks. Solutions like PingCastle and Threat Prevention enable organizations to enhance their ability to identify and block suspicious activity, significantly improving the security and resilience of their Active Directory environment.
Netwrix PingCastle
PingCastle is a widely used AD security auditing tool. While it does not directly block DCShadow attacks, it plays a crucial role in identifying the conditions that make such attacks possible.
- Identifies excessive privileges — Detects accounts with Domain Admin, Enterprise Admin, or replication rights, which are prerequisites for launching DCShadow.
- Highlights misconfigurations — Reports on schema admin roles, weak permissions, or accounts with replication privileges.
- Exposes delegation risks — Finds over-permissive ACLs on critical objects like Domain Controllers or AdminSDHolder.
- Risk scoring — Offers a high-level security score that draws attention to attack paths, privilege exposures, and structural weaknesses.
Want to uncover excessive privileges, misconfigurations, and delegation risks in your Active Directory? Download Netwrix PingCastle for free and get your AD security score today.
Netwrix Threat Prevention
Netwrix Threat Prevention helps monitor, detect, and alert on suspicious changes and behaviors in Active Directory environments.
- Real-time monitoring of AD changes — Detects unauthorized schema or replication metadata modifications, which are key indicators of DCShadow activity.
- Active Defense Controls — It can intercept and block unauthorized replication activity, such as attempts to register rogue domain controllers or inject replication metadata.
- Policy Enforcement — Implements rules to prevent specific users, hosts, or processes from performing replication-related actions, even if they hold privileged credentials.
- Behavioral analytics — Identifies anomalous use of privileged accounts or lateral movement patterns that precede DCShadow.
- Alerting on replication events — Can be configured to watch for unrecognized domain controller registration or NTDS settings changes.
Want to stop unauthorized replication attempts and detect DCShadow activity in real time? Request a free trial of Netwrix Threat Prevention today.
Detection, Mitigation and Response Strategies
Effectively defending against DCShadow attacks requires a combination of proactive detection, strategic mitigation, and well-defined response procedures.
Detection
Monitoring the following Event IDs can help detect suspicious activity associated with a DCShadow attack:
Event ID | Description | Relevance to DCShadow |
|---|---|---|
|
4928 |
An attempt was made to modify the directory service replication configuration object |
Indicates a potential attempt to alter replication settings — one of the first signs of DCShadow activity. |
|
4929 |
An attempt was made to change the replication configuration between two sites |
Could signal unauthorized changes to replication pathways used to introduce a rogue DC. |
|
5136 |
A directory service object was modified |
Captures attribute changes to AD objects. DCShadow uses replication to push stealth changes, which this can flag. |
|
5141 |
A directory service object was deleted |
Tracks deletion of AD objects. Could be used in conjunction with DCShadow to cover tracks or manipulate schema roles. |
|
4742 |
A computer account was changed |
Monitors changes to computer objects, including DCs. DCShadow may create or modify DC accounts to impersonate a replication partner. |
New Insight
- Network-based detection is one of the most effective ways to catch DCShadow attacks. Organizations should look for DRSUAPI RPC requests, especially DRSUAPI_REPLICA_ADD, originating from non-DC hosts. These requests typically travel over TCP port 135 and dynamic RPC ports (49152–65535) and are normally only seen between legitimate DCs. Any such activity from an unauthorized source is a strong indicator of malicious replication attempts.
- Deploy honeypot domain controllers with tripwire Service Principal Names (SPNs) for early alerting. These decoy systems mimic legitimate DCs but are not used for actual operations. Since no real services interact with them, any replication traffic or SPN queries they receive can be flagged as suspicious.
Mitigation
Mitigating DCShadow attacks requires a proactive approach to hardening AD, restricting administrative privileges, and closely monitoring replication-related activities.
1. Limit Admin Access
Minimize the number of users with Domain Admin or Enterprise Admin rights by implementing least-privilege access controls. Use a tiered administrative model (Tier 0/1/2) to isolate high-value accounts and infrastructure, preventing lower-tier accounts from accessing critical AD components. This reduces the risk of an attacker gaining control of accounts needed to execute DCShadow attacks.
2. Reduce Delegation
Restrict delegation rights that allow users to join machines to the domain or create/modify computer objects. Improper delegation can allow attackers to register rogue DCs or modify replication settings. Use Group Policy and ACL reviews to ensure only trusted accounts have these privileges, and regularly audit them for compliance.
3. Firewall Configurations
Configure host-based firewalls on critical infrastructure (especially DCs) to allow only necessary communication. This limits lateral movement and prevents attackers from initiating replication-related traffic from non-DC hosts. Focus on restricting RPC and LDAP ports unless explicitly needed between known systems.
4. Segment Replication Traffic
Use network segmentation to isolate replication traffic between domain controllers. By placing DCs on dedicated VLANs, organizations can monitor and control replication pathways and ensure no unauthorized systems are involved in directory synchronization.
5. Audit SPNs & DC Registrations
Service Principal Names (SPNs) are often manipulated in attacks involving rogue DCs. Regularly audit SPNs to detect suspicious or duplicate entries and monitor for unexpected NTDS Settings or DC object registrations in AD. Use automated tools to flag anomalies early.
6. Enforce Secure Admin Workstations (SAWs)
Require that all administrative tasks involving Tier-0 assets (like DCs) be performed from SAWs. These hardened devices are isolated from internet access and general-purpose use, significantly reducing the chance that credentials or administrative tools will be compromised and used in a DCShadow attack.
New Insight
- To prevent unauthorized replication attempts such as those used in DCShadow attacks, organizations should implement network-level controls that filter and restrict replication traffic. This includes applying a deny-by-default approach, where only explicitly approved DCs are allowed to communicate for replication, especially across different sites.
- To mitigate the risks posed by DCShadow attacks, it is crucial to monitor and control the creation and registration of Service Principal Names (SPNs), particularly those associated with GC/ (Global Catalog) and E3514235-4B06-11D1-AB04-00C04FC2DCD2, which is the GUID for the Directory Replication Service (DRS).
Response
A DC Shadow attack represents one of the most covert and dangerous threats to AD. Due to its stealthy nature and potential to compromise the integrity of the entire AD environment, an immediate and structured response is critical.
Activate Full Incident Response Protocol
DCShadow attacks indicate a deep compromise and privileged access that can subvert DC behavior and evade traditional logging. This requires an enterprise-wide, coordinated response to contain the threat and recover from the impact. You must:
- Immediately alert the Incident Response (IR) team, security leadership, and relevant stakeholders.
- Escalate to Critical Severity and initiate the full incident response (IR) policies and playbooks specific to AD threats or attacks.
- Enforce a freeze on all AD changes (schema, configuration, domain controllers).
- Begin forensic evidence collection (memory dumps, disk images, event logs).
- Coordinate with legal, compliance, and business continuity teams.
Assume Complete AD Compromise
Unauthorized changes made through DCShadow may not be visible through standard logs. To tackle the situation, you must:
- Treat the entire AD forest as untrusted.
- Assume that privileged credentials (Domain Admins, Enterprise Admins) and group policy objects may have been tampered with.
- Evaluate exposure of Kerberos tickets, SIDHistory abuse, replication metadata tampering, or backdoors (for example, rogue admin rights or lingering accounts).
Disable Affected Accounts and Isolate Machines
To contain lateral movement and prevent further replication of malicious changes or reintroduction of DCShadow components, it is recommended to:
- Immediately disable any accounts identified as compromised, especially those used in the attack (admin, service, or replication accounts).
- Disconnect suspected systems from the network, including:
- Machines that registered rogue SPNs or impersonated DCs.
- Hosts showing abnormal DRS replication behavior.
- Block suspicious RPC and DRS traffic from affected endpoints.
Review Replication Logs and Metadata
Identify what was changed, who made the changes, and when, so you can accurately assess the scope of the compromise.
- Use tools such as:
- repadmin /showmeta – Inspect metadata like timestamp and version number for changes to sensitive objects.
- repadmin /showobjmeta – View replication attributes on specific objects.
- Event IDs: 4662, 5137, 4929, and other directory service audit events.
- LSASS memory analysis for injected SPNs or stolen tokens.
- Focus on:
- Suspicious SPNs (especially those with E3514235-..., GC/, or ldap/).
- Unusual replication partners.
- Object metadata with time/date anomalies or admin attribution to unknown users.
Restore from Known-Clean AD Snapshots or Backups
Rollback is the safest way to undo changes made by DCShadow, especially any persistent backdoors.
- If supported, use Volume Shadow Copy Service (VSS) or System State Backups for authoritative restore of affected objects.
- For forest-wide impact:
- Consider Directory Services Restore Mode (DSRM) to rebuild trusted DCs.
- Verify backups with offline malware scans before restoring.
- Validate restored objects with hashing or golden backups.
If Necessary, Perform a Domain or Forest Rebuild
Some attacks so deeply corrupt AD that restoring trust is not feasible, so a clean-slate rebuild is the only path to full recovery and assurance.
- In cases of widespread trust violation, begin planning for:
- A new AD forest in parallel
- Migrating clean systems and accounts with proper scrubbing
- Using Red Forest design, tiered administration, and admin workstations in the rebuild
- Remove all DCs and replication configurations from the compromised domain.
Industry-Specific Impact
DCShadow attacks pose significant risks across industries that rely heavily on centralized identity infrastructure. Because these sectors store sensitive data and operate under strict regulatory requirements, the impact can be both operationally devastating and legally consequential.
Industry | Impact |
|---|---|
|
Healthcare |
A DCShadow attack can grant attackers stealthy access to systems that handle Protected Health Information (PHI). This can lead to HIPAA violations, data breaches, and compromise of Electronic Health Record (EHR) systems. Delayed detection increases the potential for patient safety risks, financial penalties, and reputational damage. |
|
Finance |
A DCShadow attack can subvert identity and access controls, enabling attackers to impersonate privileged users or inject backdoors into AD. This can facilitate unauthorized transactions, wire fraud, and manipulation of financial systems. The breach of regulatory controls such as SOX, GLBA, or PCI-DSS can result in severe legal, financial, and reputational consequences. |
|
Retail |
DCShadow attacks can be used to push unauthorized Group Policy Object (GPO) changes, allowing attackers to compromise Point-of-Sale (POS) terminals, inventory management systems, or payment gateways. This can lead to data theft, transaction manipulation, and large-scale customer information breaches. The result could be disrupted operations across multiple locations, potential violation of PCI-DSS compliance, financial loss and brand damage. |
|
Education |
DCShadow attacks can enable attackers to manipulate student or staff records within AD, potentially altering access to grading systems, exam portals, financial aid platforms, or learning management systems (LMS). This can lead to academic fraud, denial of service, and disruption of institutional integrity. Additionally, such breaches may expose personally identifiable information (PII), triggering violations of privacy laws like FERPA. |
Attack Evolution & Future Trends
As DCShadow attacks continue to evolve, it is important to understand where they might be headed in the future.
Potent Threat in Hybrid Identity Environments
Hybrid environments that integrate on-premises AD with Microsoft Entra ID or other identity providers remain vulnerable to DCShadow. Even though DCShadow targets the on-prem layer, malicious changes made locally can synchronize upstream to cloud services, thereby extending the reach of compromise. This makes DCShadow particularly dangerous in environments with federated identities, where AD functions as the core trust authority for cloud-based authentication and access control.
Automation Scripts for DCShadow Attacks
Advanced attackers are now leveraging automation frameworks to set up and execute DCShadow attacks. By reducing manual steps (such as SPN registration, privilege escalation, and metadata manipulation), threat actors can execute these attacks faster and more consistently, with fewer indicators of compromise. Automation also enables less skilled adversaries to use these complex techniques by packaging them into scripts or modular attack chains.
Increasing Overlap with AI-Driven Privilege Escalation Tools
Attackers are increasingly using AI-powered reconnaissance tools to map out administrative paths, trust relationships, and misconfigurations within AD. When combined with DCShadow, these tools can pinpoint the optimal entry point for deploying a rogue DC, identify weak links in tiered admin models, or even select the high-impact replication targets. This fusion of automation and intelligence allows attackers to move with precision within enterprise environments.
Likely to be Weaponized in Supply Chain Intrusions
Attackers are likely to use DCShadow to target compromised managed service providers (MSPs), software vendors, or identity providers — basically, any place where Active Directory plays a key role in trust and security. By injecting malicious changes into AD environments, attackers can create stealthy persistence, grant themselves privileged access, or poison replication paths. Leveraging the interconnected nature of supply chains and federated identity could result in wide-scale compromise across multiple organizations.
Key Statistics & Infographics
Quantified data on DCShadow attacks across organizations is not commonly published in detailed reports. Assessments of readiness are usually qualitative or derived from broader surveys on Active Directory security posture.
Here's an infographic that attempts to visualize stats such as when the attack gained prominence and how its detection has evolved. It uses conceptual industry analysis and trends where precise data is unavailable:
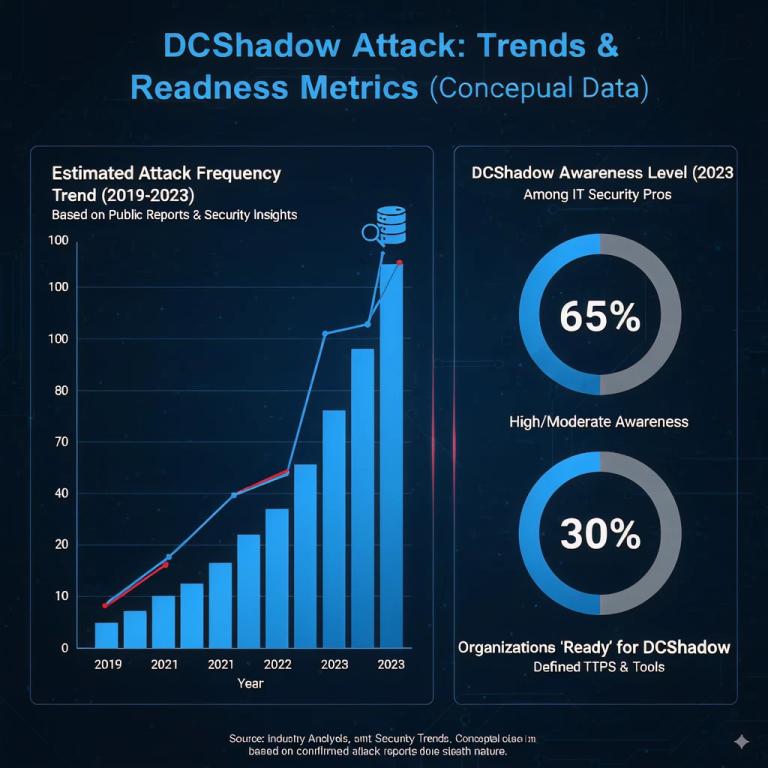
The infographic presents the following key points:
- Estimated Attack Frequency Trend (2019–2023): The frequency of DCShadow attacks seems to have sharply increased, which aligns with the growing sophistication of cyber attacks.
- DCShadow Awareness Level (2023) Among IT Security Pros: 65% High/Moderate Awareness: This pie chart indicates that an estimated 65% of IT security professionals are considered to have a high or moderate level of awareness regarding DCShadow attacks as of 2023. This suggests that about one-third of the security community may not be up-to-date on its nuances.
- Organizations 'Ready' for DCShadow (2023): 30%: This figure represents a conceptual estimate that only about 30% of organizations are adequately "ready" to detect and mitigate DCShadow attacks. This points to a significant gap between awareness and actual defensive capabilities.
Final Thoughts
DCShadow represents one of the most covert and technically sophisticated methods of compromising Active Directory, exploiting trusted replication mechanisms to inject unauthorized changes while bypassing standard auditing. Its stealth and reliance on privileged access mean that prevention is less about patching and more about architectural hardening, access control, and vigilant monitoring. Organizations must adopt a zero trust mindset, enforce tiered administrative models, and deploy advanced detection tools to identify anomalies in replication behavior.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
Kerberoasting Attack – How It Works and Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
