Understanding Golden Ticket Attacks
A Golden Ticket attack lets an attacker forge a Kerberos Ticket Granting Ticket (TGT) using the KRBTGT key to gain unlimited, persistent access to an Active Directory domain.
Attribute | Details |
|---|---|
|
Attack Type |
Golden Ticket Attack |
|
Impact Level |
Critical |
|
Target |
Businesses, Government, All large organizations |
|
Primary Attack Vector |
Credential Theft, Network Exploitation |
|
Motivation |
Espionage, Data Exfiltration, Financial Gain, Disruption |
|
Common Prevention Methods |
KRBTGT Password Rotation, Credential Guard, Least Privilege, AD Hardening, Monitoring |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Critical |
|
Ease of Execution |
Hard |
|
Likelihood |
Medium |
What is a Golden Ticket Attack?
Think about what a golden ticket meant in Charlie and the Chocolate Factory - unrestricted access to everything, no questions asked. In cybersecurity, a Golden Ticket attack gives hackers that same kind of VIP pass to your entire network.
So here is a Golden Ticket attack explained. A Golden Ticket attack is a Kerberos exploitation technique in which an attacker uses the KRBTGT account hash from Active Directory to forge Ticket Granting Tickets (TGTs). This allows them to impersonate any user, including domain administrators, and gain unrestricted, long-term access to all domain resources.
Attackers often employ tools like Mimikatz or Impacket to extract the KRBTGT hash and generate these forged tickets. Because the forged TGTs are cryptographically valid, the Key Distribution Center (KDC) will trust them, even if passwords are changed - revealing a fundamental weakness in the Kerberos protocol.
Domain controllers cannot distinguish these forged tickets from legitimate ones, so traditional authentication logs do not flag them. Cleaning up is not as simple as changing a password; you must rotate the KRBTGT key twice on every domain controller to fully cut off the attacker’s ability to create fake tickets.
The Kerberos Protocol: How Does it Work
- A user logs in and sends a timestamp encrypted with their password hash to the Key Distribution Center (KDC) for pre-authentication.
- The KDC has a stored hash of the user's password. It uses it to decrypt the timestamp, and if valid, authenticates the user.
- The KDC issues a TGT encrypted with the KRBTGT account hash (default validity is 10 hours).
- With the TGT, the user can request access to multiple domain services without re-authenticating.
- For each service request, the KDC’s Ticket-Granting Server (TGS) issues a service ticket, signed with the service account’s hash, which allows direct connection to the target server.
How do Attackers Exploit it?
In a Golden Ticket attack, adversaries bypass the KDC by generating their own TGTs to access domain resources. To craft this TGT, they need:
- The domain’s Fully Qualified Domain Name (FQDN)
- The domain’s Security Identifier (SID)
- The username of the account they intend to impersonate
- The KRBTGT account’s password hash
How Does a Golden Ticket Attack Work?
A Golden Ticket attack unfolds in a series of steps that let an attacker gain and maintain total control of an Active Directory environment. Let’s look at each stage.
1. Initial Compromise
The attacker first breaches a network, mostly using phishing emails, exploiting unpatched vulnerabilities, or stealing weak credentials.
2. Privilege Escalation
Once inside, the attacker hunts for higher privileges. They may crack additional passwords, exploit misconfigurations, or abuse privilege-escalation flaws until they gain domain admin or replication rights on a domain controller. These are powerful roles that give them direct access to Active Directory data.
3. KRBTGT Hash Extraction
Armed with those rights, the attacker uses malicious tools like Mimikatz and the DCSync technique to steal the password hash of the KRBTGT account — the cryptographic key that signs every Kerberos TGT and enables forging of new TGTs. They also capture the domain's Security Identifier (SID).
4. Ticket Forging
With the stolen KRBTGT password hash, an attacker can create a fake TGT (Golden Ticket) for any user they choose (often a high-privilege account). Attackers can set custom privileges and an extended validity period for the TGT, effectively giving themselves a ‘golden’ master key to the domain.
5. Ticket Injection & Lateral Movement
The attacker injects the forged TGT into an active session. Because the ticket is cryptographically valid, the attacker can now request legitimate Ticket-Granting Service (TGS) tickets to move laterally across servers, databases, file shares, and applications without triggering password prompts.
6. Persistence & Evasion
These forged tickets remain trusted until the KRBTGT key is rotated twice on every domain controller. Resetting passwords or disabling accounts will not help, as the attacker can keep creating fresh tickets. Hence they can maintain stealthy, long-term access by blending in with normal Kerberos traffic.
Attack Flow Diagram
The Golden Ticket attack follows a predictable chain of events. Let’s look at an example attack scenario and visualize the attack stages to understand how an intruder can move from an initial breach to complete control of an Active Directory environment.
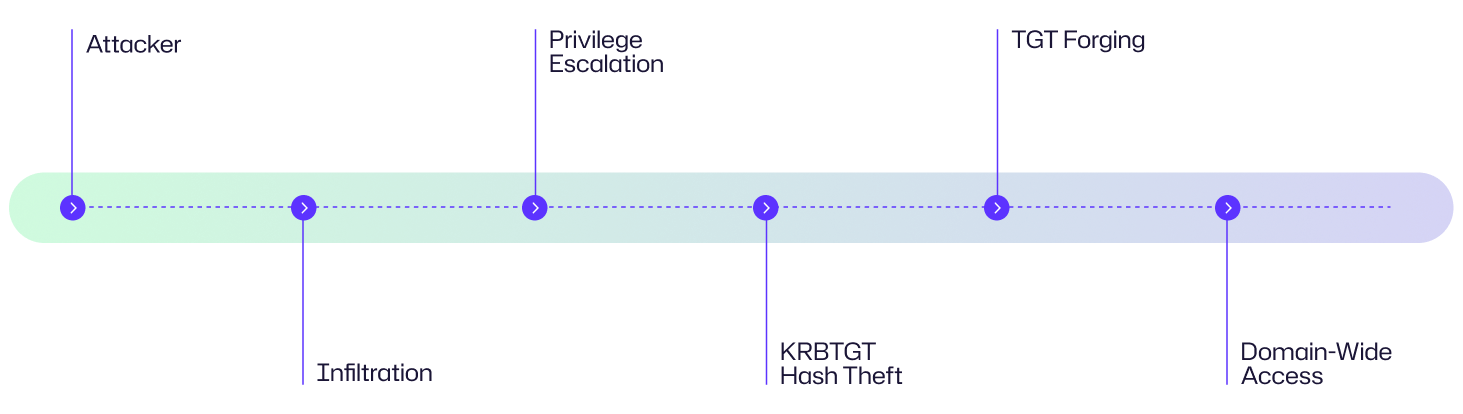
Imagine a regional healthcare provider where an employee clicks a phishing email, giving an attacker initial access to the network. The intruder quietly escalates privileges by exploiting a misconfigured file share and eventually gains domain admin rights. Using Mimikatz, they extract the KRBTGT hash, forge their own Kerberos tickets, and move laterally across critical systems, such as patient records and billing servers, without triggering password prompts or security alerts. Within hours, they have unrestricted, stealthy access to the entire domain.
Examples of a Golden Ticket Attack
Golden Ticket attacks have been used in real-world cyber-espionage campaigns to gain long-term, stealthy access to high-value networks. The following cases highlight how different threat groups have used this technique.
Case | Impact |
|---|---|
|
APT15 (Ke3chang) – UK government contractor attack (2018) |
In 2018, the Chinese-linked threat group APT15 (also known as Ke3chang) compromised a UK government contractor responsible for highly sensitive projects. After gaining an initial foothold, the attackers escalated privileges to domain administrator and extracted the KRBTGT account hash from Active Directory. Armed with this key, they generated Kerberos Golden Tickets, which let them move laterally, harvest confidential government data, and exfiltrate it over an extended period. NCC Group’s investigation found that APT15 used Mimikatz to dump credentials and generate Kerberos Golden Tickets. Because Golden Tickets remain trusted until the KRBTGT key is rotated twice on all domain controllers, the attackers retained stealthy, persistent access long after the initial intrusion was detected. |
|
TA428 – Eastern Europe military-industrial enterprises (2022) |
In 2022, the China-linked threat group TA428 launched a cyber-espionage campaign against military-industrial enterprises and government institutions across Eastern Europe and Asia. After spear-phishing their way into networks and gaining domain controller privileges, they stole the KRBTGT account hash and carried out Kerberos Golden Ticket attacks. These forged tickets gave TA428 full, long-term control of victim networks, enabling extensive espionage and the theft of large volumes of sensitive military research, defense technology data, and confidential communications. |
|
Antlion – Financial institutions in Taiwan (2020–2021) |
From 2020 to 2021, the China-linked group Antlion infiltrated Taiwanese financial institutions through spear-phishing and custom malware. After gaining domain controller access, they stole the KRBTGT hash and launched Kerberos Golden Ticket attacks. This provided them persistent, domain-wide access to critical financial systems for surveillance, data theft, potential fraud, and sabotage. According to Symantec, Antlion used a “Kerberos golden ticket tool based on the Mimikatz” amongst other tools. |
Consequences of of a Golden Ticket Attack
A successful Golden Ticket attack can have a wide-ranging, long-lasting impact on an organization.
Impact Area | Description |
|---|---|
|
Financial |
A Golden Ticket attack can lead to massive financial costs. This includes direct losses from financial fraud through manipulated systems and regulatory fines under laws such as GDPR, HIPAA, and SOX for data breaches and the exfiltration of sensitive information. Organizations also face high expenses for incident response, forensic investigations, and remediation, plus revenue losses from downtime or interrupted services. In some cases, attackers may demand ransom or extortion payments. |
|
Operational |
Attackers can disrupt critical IT services, such as domain controllers, file servers, and business applications. This can lead to extended downtime that ripples through supply chains and production cycles. Compromised access controls may trigger widespread administrative and operational chaos, and even sabotage internal systems, making recovery slow and complex. |
|
Reputational |
A breach of this scale erodes customer and partner trust, strains long-term relationships, and draws negative media coverage. The organization’s brand image and market reputation can suffer, while investors and stakeholders may increase scrutiny that may affect the company’s valuation. |
|
Legal/Regulatory |
Organizations are typically required to issue data-breach notifications under privacy regulations, such as GDPR’s 72-hour rule. They may face lawsuits from affected customers and employees along with long-term compliance audits and sanctions from regulatory bodies. In cases of severe governance failures, executives could even face personal liability. |
|
Security Posture Degradation |
Because forged Kerberos tickets appear legitimate, Golden Ticket attacks undermine the effectiveness of security controls and monitoring tools. This leads to longer attacker dwell time, complicating breach detection and response. AD integrity could be compromised to the extent that organizations may consider a full rebuild of the environment. |
Common Targets of a Golden Ticket Attack: Who is at risk?
Simply stated, any organization that depends on AD for user access and identity management is a potential target of a Golden Ticket attack. Attackers prefer environments where a single compromise can grants broad, long-term access to critical systems and data. Some common targets may include:
|
Large Enterprises |
Enterprises with complex AD infrastructures and multiple domain controllers present a wide attack surface. Add to it, organizations with numerous privileged accounts and legacy systems usually have weak network segmentation and outdated security controls. This makes it easier for attackers to forge tickets and move laterally without detection. |
|
Government Agencies |
Government agencies have extensive internal networks that hold highly sensitive information, from defense and intelligence to law-enforcement data. A Golden Ticket attack provides persistent access to serve motives such as espionage, surveillance, and the exfiltration of classified material. |
|
Financial Institutions |
Banks and financial service providers rely heavily on AD to secure internal systems and authenticate users. By forging Kerberos tickets, attackers can maintain covert access to execute fraudulent transactions, manipulate financial records, and steal high-value customer and payment data. |
|
Healthcare Organizations |
Hospitals and healthcare networks manage large volumes of protected health information (PHI) and depend on AD to control access to EMR (electronic medical records) systems, critical medical devices, and patient data. This concentration of sensitive information and the need to keep systems running around the clock make healthcare organizations appealing targets for Golden Ticket attacks. |
|
Retail Chains |
Retailers normally use AD to manage point-of-sale (POS) systems, supply-chain networks, and customer databases. Attackers can exploit forged tickets to manipulate transactions, siphon payment-card information, and disrupt inventory and logistics on a large scale. |
|
Managed Service Providers (MSPs) and IT Service Companies |
MSPs maintain privileged access to client environments, making them an attractive ‘one-to-many’ gateway. Compromising an MSP’s AD lets attackers pivot into customer networks, which multiplies the impact across organizations. |
|
Organizations with Hybrid or Cloud-Integrated AD |
Enterprises with hybrid AD setups, such as on-premises AD synchronized with Microsoft Entra ID, often have complex trust relationships and replication paths. If the cloud connectors are misconfigured or not well secured, they widen the attack surface, making it easier for attackers to forge tickets and keep long-term access. |
Risk Assessment
The combination of critical impact and medium likelihood places Golden Ticket attacks in the high-risk category.
Risk Factor | Level |
|---|---|
|
Potential Damage |
Critical A compromise allows the adversary to exfiltrate sensitive data, disrupt business operations, and deploy ransomware. Recovery requires rebuilding the AD environment and re-securing all trust relationships, resulting in major downtime and financial loss. |
|
Ease of Execution |
Hard Attackers need domain controller access and Kerberos expertise to steal the KRBTGT hash and create forged tickets, making the attack technically challenging. |
|
Likelihood |
Medium While not as common as phishing, the likelihood remains moderate because well-funded, skilled, and persistent threat actors target Active Directory or hybrid environments with long dwell times. |
How to Prevent Golden Ticket Attacks
Golden Ticket attacks are one of the more severe threats to AD environments. Their detection is difficult and recovery is costly. To prevent these attacks, organizations must use a mix of technology, tools, and process controls.
Technical Measures
Some technical measures to prevent a Golden Ticket attack are:
- Regularly Reset the KRBTGT Account Password Twice: Securely rotate the KRBTGT key twice across all domain controllers, a process that must be carefully planned to avoid breaking authentication services. Here’s the right way to do it - change the KRBTGT password, wait for replication, then change it again. This invalidates any forged tickets created under the old or intermediate hash.
- Implement Strict Least Privilege Access: Make sure that only a minimal number of users and service accounts have high privileges. Limit membership in privileged groups like Domain Admins. Remove excessive admin rights and avoid giving administrative rights across forest/domain boundaries unnecessarily.
- Use Tiered Administration Models to Segment Access: Tiered administration models divide IT administration into separate ‘tiers’ or levels of privilege, each with its own set of accounts and tools.
- Tier 0: Domain controllers, AD forest-level services, and other critical identity infrastructure
- Tier 1: Servers and applications
- Tier 2: User workstations and standard desktops
With this approach, a compromise at a lower tier does not automatically lead to full domain compromise.
H3. Security Tools
Security tools can help prevent a Golden Ticket attack.
- Deploy EDR and Advanced SIEM to Detect Anomalies in Kerberos Ticket Usage: SIEM solutions detect suspicious Kerberos activity in real time by tracking authentication events, unusual ticket lifetimes, unexpected logins, and abnormal service ticket use. They parse Windows Security Logs for TGT/TGS events, correlate data across the network, and trigger timely alerts. EDR complements this by protecting endpoints from memory-based credential theft.
- Use Credential Guard / OS-Level Protections to Block Memory Credential Theft: Technologies like Microsoft Defender Credential Guard are designed to protect credentials in memory. By limiting LSASS memory access and keeping the OS properly patched and updated, organizations can reduce the risk of attacks such as Mimikatz Golden Ticket.
Non-Technical Measures
Some non-technical prevention measures include the following:
- Train Employees on Phishing and Social Engineering: Since many initial breaches stem from credential compromise (phishing, malicious attachments or links), organizations should roll out employee awareness programs to close these entry points.
- Implement Change Management and Audit Processes: Implement formal change control and audit processes to all modifications made to privileged accounts, permissions, domain policies, etc. It is best to keep logs, review them regularly, and enforce least privilege and segregation of duties for any changes.
How Netwrix Can Help
Netwrix provides tools to strengthen Active Directory security and quickly spot signs of a Golden Ticket attack. Netwrix Threat Prevention has rick capabilities to:
- Continuously monitor Kerberos authentication, raising alerts on suspicious ticket activity such as unusual ticket lifetimes or forged PAC data.
- The Golden Ticket analytic type detects Kerberos tickets that exceed the configured maximum lifespan and generates alerts.
- The Forged PAC analytic type detects Kerberos tickets with modified PACs (Privilege Attribute Certificates), Since Golden Tickets often forge or manipulate PAC to elevate privileges, this is a direct signal.
- Detect privilege escalations and unauthorized changes to critical AD objects, helping security teams respond before attackers gain persistence. Threat Prevention provides templates for privilege escalation detection. You can convert a Privilege Escalation template into an active policy to monitor for unauthorized permission changes and when a non-admin account gains elevated rights.
- Offer real-time monitoring, alerting, and blocking of high-risk or unauthorized changes in Active Directory. Threat Prevention’s Active Directory solution watches all authentication (Kerberos and NTLM) access, object modifications, group memberships, GPO edits, AD replication, LSASS modifications, and more. It provides detailed audit trails (pre- and post-change values, who made the change), helping to catch early signs of misuse.
Detection, Mitigation and Response Strategies
Golden Ticket attacks are challenging to detect and mitigate because the forged TGTs are cryptographically valid and signed with the real KRBTGT key, so normal Kerberos checks treat them as genuine. Even if user account passwords are reset, the attacker can keep generating valid tickets as long as they have the KRBTGT hash. And it leaves little footprint because the attacker does not need to connect to the domain controller to request new tickets. Instead, they can create valid tickets on their own machine and present them when needed to access network resources.
IT teams should look for anomalies that indicate forged or long-lived tickets.
Unusual Ticket Lifetimes
Kerberos tickets normally have a default lifetime of about 10 hours and are renewable for 7 days. A forged Golden Ticket, however, might be configured to last months or even years. Security monitoring tools like Netwrix Threat Prevention or a SIEM can flag such tickets and raise alerts that an attacker may be trying to maintain access without re-authenticating.
Tickets for Non-Existent or Dormant Accounts
If you see Kerberos service tickets (Event ID 4769) being issued to accounts that have been disabled, deleted, or inactive for months, it strongly suggests that an attacker has control over the KRBTGT hash and is forging tickets to impersonate that account.
TGT Reuse after KRBTGT Password Changes
After rotating the KRBTGT account password, all previously issued tickets should become invalid. If you find successful logons or service requests using tickets issued before the password change, it means that forged tickets signed with the stolen hash are still working. Monitoring for Kerberos authentication events that reference an old key version number (KVNO) is an effective detection method.
Kerberos Log Anomalies
Watch for authentication requests originating from endpoints that do not normally interact with domain controllers or sudden spikes in Kerberos Event IDs (4768, 4769, 4771). These are Windows Security log event IDs generated by a DC (or other Kerberos Key Distribution Center) when Kerberos operations occur:
- Event ID 4768: Generated when a user or computer requests a TGT from the Key Distribution Center (first step of Kerberos authentication).
- Event ID 4769: Logged when the client requests a service ticket (TGS) to access a specific service after obtaining a TGT.
- Event ID 4771: Indicates that Kerberos pre-authentication failed, often due to an incorrect password, time synchronization issues, or possible brute-force attempts.
Also if you notice TGTs being generated repeatedly on a single host or from geographically unusual IP addresses, consider it a sign of ticket forging.
Mismatched Service Principal Names (SPNs)
Another red flag of forged tickets and lateral movement is when you notice tickets that reference services that you do not run or suddenly try to access several unrelated services in a short time.
Mimikatz installation
If your antivirus detects malicious software, such as credential-dumping tools or other post-exploitation utilities, it can be an indirect sign of a Golden Ticket attack.
Immediate Response
When you suspect a Golden Ticket attack, act fast:
- Reset the KRBTGT Account Password Twice: This ensures that all existing forged tickets become invalid, as discussed earlier in the Technical Measures section.
- Isolate Affected Systems and Accounts: Disconnect compromised hosts from the network and disable any accounts showing suspicious Kerberos activity to stop further lateral movement.
- Revoke Active Sessions: To cut off attacker access, you can force logoffs or use tools such as klist purge or PowerShell’s Revoke-ADAuthentication to terminate all Kerberos sessions.
- Keep Forensic Evidence: Preserve security logs, memory dumps, and system images before cleaning up to aid in investigation and potential legal action.
- Notify Stakeholders: Notify your incident-response team, management, and legal or compliance personnel right away, so that they can handle communication, regulatory requirements, and potential customer impact.
Long-Term Mitfigation
Organizations should reduce future risk through proactive controls, such as those listed here.
- Improve Active Directory Hygiene: Limit the number of privileged accounts, apply the least privilege principle, and monitor membership of Domain Admins and Enterprise Admins. You should also enforce strong password policies and remove legacy or unused accounts to reduce the attack surface.
- Regular Threat Hunting: Schedule hunts focused on Kerberos anomalies, such as unusual ticket lifetimes, unexpected key version numbers (KVNOs), or logon activity from atypical hosts. Combine event-log analysis with your SIEM or tools like Netwrix Threat Prevention to identify suspicious patterns.
- Periodic Privileged Account Reviews: Review all privileged accounts (including service accounts) at least quarterly. Verify ownership, necessity, and password rotation, especially for the KRBTGT account. It is best to disable accounts that are stale or unneeded.
Industry-Specific Impact
Golden Ticket attacks can disrupt any organization, but the risks and regulatory consequences vary by industry. By understanding sector-specific implications, organizations can optimize defenses and response plans.
Industry | Impact |
|---|---|
|
Healthcare |
Healthcare networks hold vast amounts of sensitive patient data and depend on continuous system availability. A Golden Ticket compromise could expose electronic health records, disrupt clinical operations, and lead to HIPAA violations, resulting in heavy fines and reputation damage. |
|
Finance |
Banks and financial services can suffer severe consequences because attackers can use forged tickets to access core banking systems, execute unauthorized transfers, and manipulate transactions. Such breaches can result in massive financial losses, fraudulent account activity, serious penalties under SOX or other financial regulations, and sheer loss of customer trust. |
|
Retail |
Retailers maintain complex supply chains and hold volumes of customer data, so a Golden Ticket attack can be especially damaging. Attackers can pivot from corporate networks into point-of-sale systems and partner environments, leading to large-scale theft of payment card data, exposure of customer records, and costly PCI DSS compliance penalties. All these can disrupt operations and erode customer trust. |
Attack Evolution & Future Trends
Emerging technologies and changing attacker behaviors are making Golden Ticket attacks more automated, stealthy, and difficult to contain.
Increasing Use of AI
Attackers are beginning to integrate artificial intelligence into their workflows to automate ticket forging and lateral movement. AI-driven scripts can quickly identify privileged accounts, craft valid tickets, and adjust activity to stay undetected. This reduces the time from initial compromise to full domain control.
Deepfake-Driven Social Engineering
Deepfake audio and video add a new twist to phishing and pretexting attacks. Threat actors can impersonate executives or IT staff in voice or video calls, and trick employees into sharing passwords or approving multi-factor authentication prompts. After acquiring initial credentials, they can gain the foothold needed to steal the KRBTGT hash and launch a Golden Ticket attack.
Rise of Sophisticated Ransomware Groups
Advanced ransomware groups are now combining file-encrypting malware with Golden Ticket techniques. By forging long-lasting Kerberos tickets, they can maintain stealthy domain-admin access even after IT teams discover the initial compromise. This enables them re-encrypt systems, quietly steal data, and push for higher ransom demands.
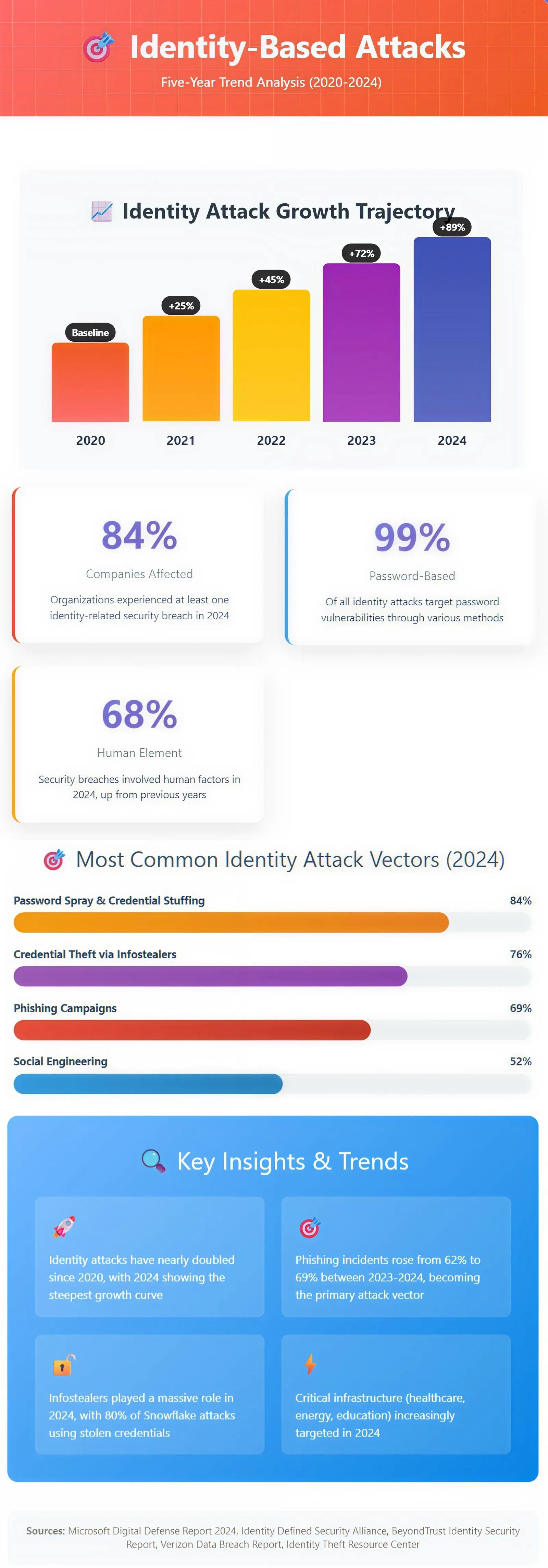
Key Statistics & Infographics
A growing body of evidence shows that Golden Ticket attacks are being used more often, and with more stealth. Google Cloud reports that median dwell time (time between initial compromise and detection) across many types of attacks has dropped from 16 days in 2022 to 10 days in 2023.
Infographic: Trend of Identity-Based Attacks
The following infographic shows trends in identity-based attacks over the last five years.
Sources: Microsoft Digital Defense Report 2024, Identity Defined Security Alliance, BeyondTrust Identity Security Report, Verizon Data Breach Report, Identity Theft Resource Center
Final Thoughts
Golden Ticket attacks strike at the heart of your Active Directory security. Their stealth, persistence, and ability to bypass traditional safeguards make them a potential nightmare for any organization. Holistic security demands more than piecemeal defenses: it calls for a strategy that blends prevention, continuous detection, and quick response to defend against a Golden Ticket cyber security threat. Strengthen your AD security posture today with Netwrix solutions and stay one step ahead of attackers who are constantly stalking new targets.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Kerberoasting Attack – How It Works and Defense Strategies
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
