Centre de ressourcesGuide pratique
Comment détecter les modifications des éléments de démarrage dans le registre Windows
Comment détecter les modifications des éléments de démarrage dans le registre Windows
Audit Natif
- Exécutez gpedit.msc → Créez un nouveau GPO → Modifiez-le : Accédez à "Configuration de l'ordinateur" → Stratégies → Paramètres Windows → Paramètres de sécurité → Stratégies locales → Stratégie d'audit :
- Auditez l'accès aux objets → Définissez → "Succès" et "Échecs".
- Allez dans Event Log → Définir :
- Taille maximale du journal de sécurité à 4 Go
- Méthode de rétention pour le journal de sécurité à « Écraser les événements selon les besoins ».
- Associez le nouveau GPO à l'OU avec les serveurs Windows : Allez dans "Gestion des stratégies de groupe" → Cliquez droit sur l'OU défini → Choisissez "Lier un GPO existant" → Sélectionnez le GPO que vous avez créé.
- Forcez la mise à jour de la stratégie de groupe : Dans "Gestion de la stratégie de groupe" faites un clic droit sur l'unité d'organisation définie → Cliquez sur "Mise à jour de la stratégie de groupe".
- Exécutez "regedit" → Naviguez jusqu'à "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" → Cliquez avec le bouton droit sur la clé "Run" et sélectionnez "permissions" → Cliquez sur "Avancé" → Sélectionnez l'onglet "Auditing" → Cliquez sur le bouton "Ajouter" :
- Sélectionnez le principal : « Tout le monde »
- Sélectionnez le type : "Tous"
- Sélectionnez S'applique à : "Cette clé et ses sous-clés"
- Sélectionnez les autorisations avancées : "Créer une sous-clé", "Définir une valeur", "Créer un lien", "Écrire DAC" et "Supprimer".
- Suivez les mêmes étapes pour les clés de registre suivantes :
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\ CurrentVersion\Run"
- HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components"
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components\.
- Ouvrez l'Observateur d'événements → Recherchez dans le journal de sécurité l'ID d'événement 4657 (une valeur de registre a été modifiée).
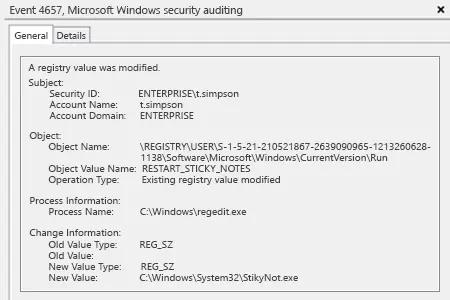
Netwrix Auditor pour Windows Server
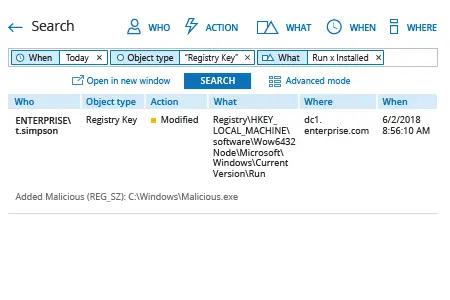
- Exécutez Netwrix Auditor → Allez dans "Recherche" → Cliquez sur "Mode avancé" si ce n'est pas sélectionné → Configurez les filtres suivants :
- Filter = "Quand"
Operator = "Égale"
Value = "Aujourd'hui" - Filter = "Type d'objet"
Operator = "Égale"
Value = "Clé de registre" - Filter = "Quoi"
Operator = "Contient"
Value = "Exécuter" - Filter = "Quoi"
Operator = "Contient"
Value = "Installé"
- Filter = "Quand"
- Cliquez sur le bouton « Rechercher » et examinez quelles clés de registre ont été modifiées et par qui.
Pour créer une alerte déclenchée chaque fois qu'une clé de registre est modifiée :
- À partir des résultats de recherche, naviguez vers « Outils » → Cliquez sur « Créer une alerte » → Spécifiez le nom de la nouvelle alerte.
- Passez à l'onglet « Destinataires » → Cliquez sur « Ajouter un destinataire » → Spécifiez l'adresse e-mail où vous souhaitez que l'alerte soit livrée.
- Cliquez sur « Ajouter » pour enregistrer l'alerte.
Partager sur
