Netwrix Data Access Governance + Netwrix Identity Management
Automate and Govern What Matters Most
Unify Data Access Governance and Identity and Access Management
Your sensitive data and critical infrastructure deserve more than patchwork identity governance. The Netwrix Access Analyzer + Netwrix Identity Manager Solution Accelerator combines Access Analyzer’s visibility into sensitive data and entitlements with Identity Manager’s automation, extending discovery into lifecycle governance and enriching certifications with clean entitlement data and ownership context. This ensures every permission is intentional, every entitlement is reviewed, and every user has access only to what they truly need — no more, no less.
How Netwrix Delivers Unified Governance in Action
Why Integrate Your Netwrix DAG and IGA Solution?
Combining DAG and IGA unlocks scalable, secure, and automated access governance. Here’s how:
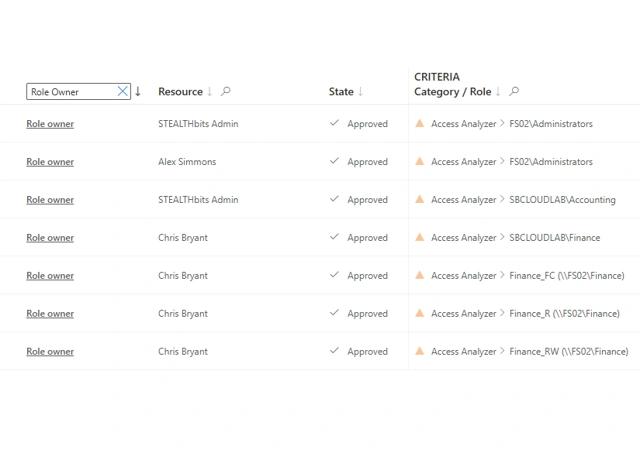
Good Identity Management Starts with Good Data
Netwrix Access Analyzer discovers and classifies sensitive data, giving Identity Manager the clean entitlement data it needs for accurate decisions.
Centralized Policy Management
Define and enforce access policies in one place with Netwrix Identity Manager to ensure consistent governance across on-prem and cloud systems.
Centralized Certification of Entitlements
Unify access certifications across files, apps, and data to eliminate silos and reduce review fatigue.
Real-Time Role Synchronization
Sync changes in roles, org structure, and policy triggers instantly — no stale roles.
Full Audit Trails of Entitlement Approvals and Certifications
Every decision logged, tracked, and exportable for audit-ready reporting.
A Holistic Approach to the Governance Life Cycle
From access request to offboarding — every step governed, visible, and controlled.
Popular Use Cases
Automated Offboarding of Sensitive Data
Immediately revoke access to files, shares, and systems tied to critical data when users leave.
Role-Based Access Provisioning
Assign entitlements automatically based on roles and business logic, reducing manual errors.
Entitlement Certification Campaigns
Launch department-wide or org-wide reviews with built-in reminders and escalation workflows.
Certify All Types of Access, Human and Non-Human
Whether it’s a contractor, bot account, or integration — ensure only valid identities retain access.
Automate Access Safeguards and Approvals
Enforce policy checks and approvals with automated workflows to keep access compliant and prevent over-entitlement.
