Netwrix helps you comply with CIS CSC
About CIS CSC
The CIS Critical Security Controls (CSC) are a prioritized set of cybersecurity best practices developed by the Center for Internet Security (CIS). They are designed to help organizations reduce their risk of cyberattacks and strengthen their security posture.
What is the purpose of CIS CSC?
- Defending against common and severe cyber threats: The CIS Controls are based on threat intelligence and real-world attack patterns. They focus on the most prevalent attack vectors and provide specific actions to block or mitigate them.
- Focusing limited resources on actions with the greatest impact: The controls are prioritized, meaning you can start with high-impact, low-effort tasks that significantly improve security posture.
- Aligning with other frameworks: The CIS Controls map to popular compliance and security frameworks like NIST, ISO 27001, and CMMC, making them a practical foundation or supplement for broader governance programs.
How does Netwrix help you comply?
As one of the leading cybersecurity solution vendors and providers, Netwrix aims to enable organizations with all the necessary tools to govern, identify, detect, protect, respond, and recover from data breaches be it caused by user, data, or infrastructure-related security gaps.
Our solutions aim to aid security professionals in their Risk Assessment, Threat Identification, and Incident Management efforts by minimizing the cybersecurity impacts, identifying their nature, narrowing their scope, pinpointing their exact timing, and protecting the organization’s most valued assets.
Netwrix 1Secure DSPM
Netwrix 1Secure is a SaaS solution that provides visibility into on-premises and cloud environments. It discovers and classifies shadow and sensitive data, assesses, prioritizes, and mitigates risks to it, and detects threats in time to prevent a data breach.
Download PDF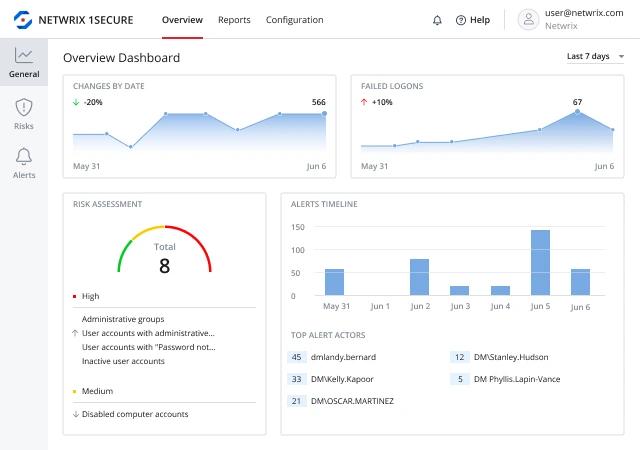
Netwrix Access Analyzer
Netwrix Access Analyzer automates the discovery, collection, and analysis of information from more than 40 systems and data sources, including Active Directory, Entra ID, file systems, databases, and major cloud storage services, so you can locate, manage, and secure sensitive data and access rights on-premises and in the cloud.
Download PDF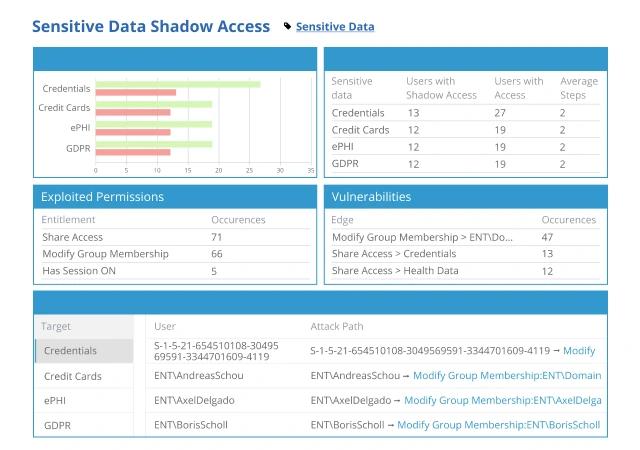
Netwrix Auditor
Netwrix Auditor is a visibility platform that tracks changes, configurations, and access across hybrid IT environments. It delivers security analytics to detect abnormal user behavior and investigate threats before breaches occur.
Download PDF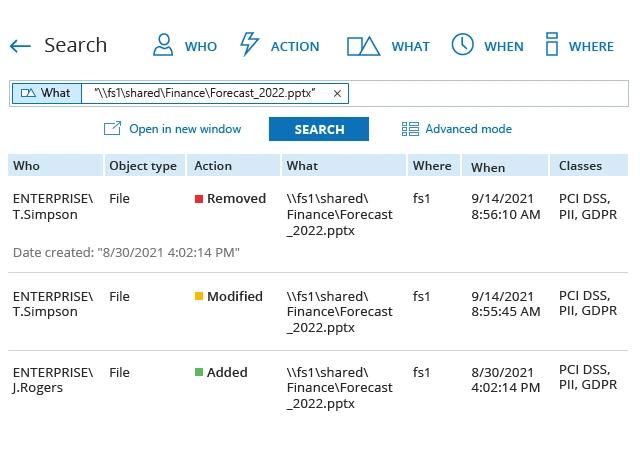
Netwrix Change Tracker
Netwrix Change Tracker is a system configuration and integrity assurance product, used for compliance programs, host intrusion detection, and change control management for enterprise IT systems.
Download PDF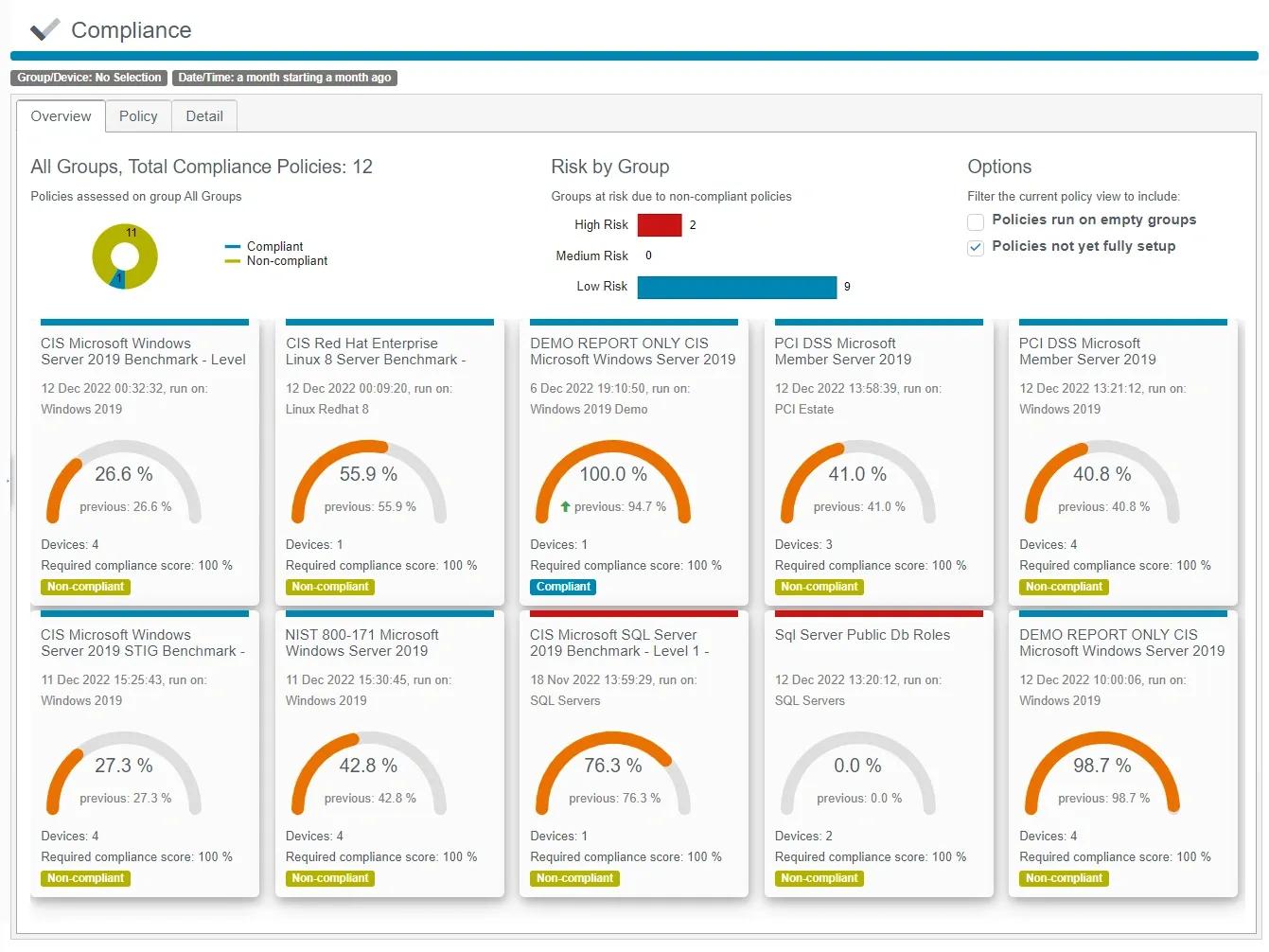
Netwrix Data Classification
Netwrix Data Classification identifies and classifies sensitive and business-critical content, mitigates the risk of data breaches, and fulfills compliance requirements with less effort and expense.
Download PDF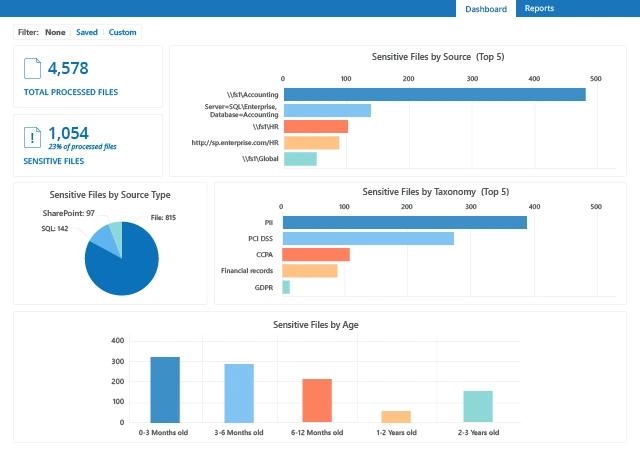
Netwrix Directory Manager
Netwrix Directory Manager simplifies identity and access management by providing automated group, user, and entitlement management capabilities.
Download PDF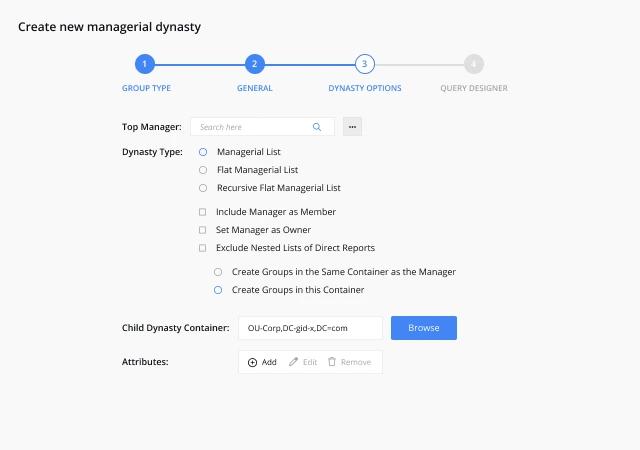
Netwrix Endpoint Policy Manager
Netwrix Endpoint Policy Manager simplifies policy management across diverse endpoints—virtual desktops, thin clients, domain-joined and non-domain-joined devices—ensuring consistent security in hybrid environments.
Download PDF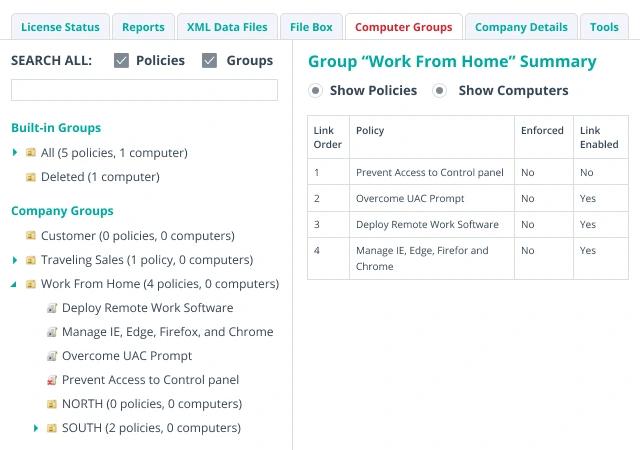
Netwrix Identity Manager
Netwrix Identity Manager is an IGA solution that automates user lifecycle management to enhance security, ensure compliance, and improve productivity for joiners, movers, and leavers.
Download PDF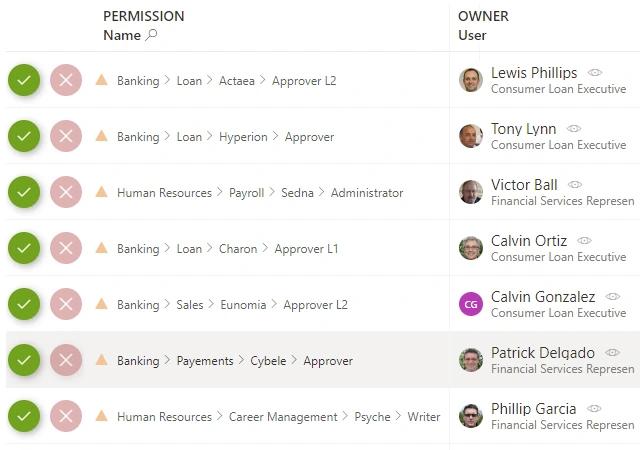
Netwrix Password Secure
Netwrix Password Secure helps enforce strong, compliant password practices by managing credentials, replacing weak passwords, applying role-based policies, auditing usage, and securing privileged access to boost both security and productivity.
Download PDF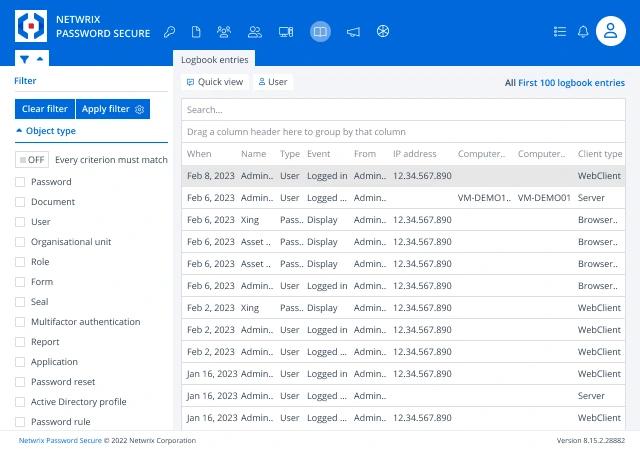
Netwrix PingCastle
Netwrix PingCastle identifies misconfigurations and hidden risks in Active Directory and Entra ID, delivering actionable insights to help organizations proactively reduce identity-based threats.
Download PDF
Netwrix Platform Governance
Netwrix Platform Governance helps you safely manage changes in NetSuite and Salesforce by identifying hidden risks, minimizing downtime, and preventing data loss—ultimately improving productivity.
Download PDF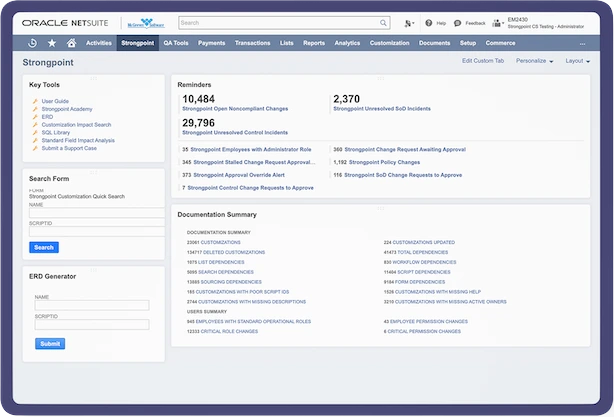
Netwrix Privilege Secure
Netwrix Privilege Secure is a next-gen PAM solution that simplifies privileged task management by focusing on actions rather than accounts, reducing complexity and minimizing the attack surface.
Download PDF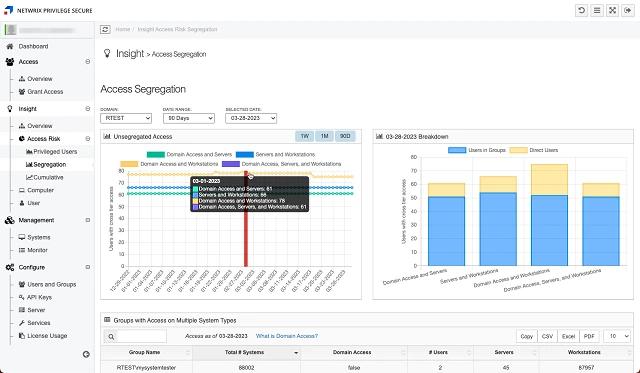
Netwrix Identity Recovery
Netwrix Identity Recovery lets administrators quickly restore objects or attributes to a known good state. It includes automated Active Directory forest recovery and Entra ID recovery—minimizing downtime and preventing damage.
Download PDF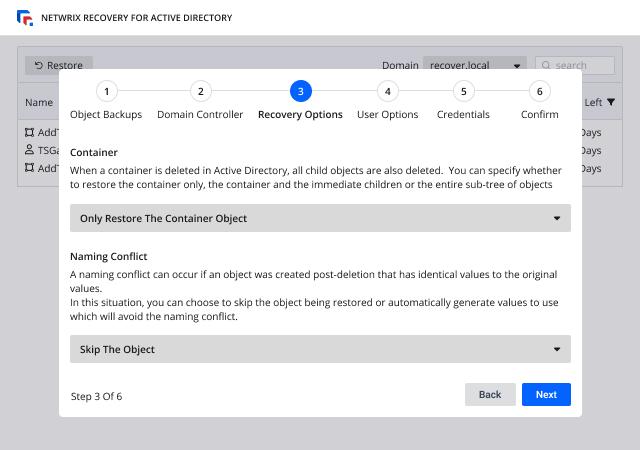
Netwrix Threat Manager
Netwrix Threat Manager detects and responds to advanced threats against Entra ID, Active Directory, and file systems with high accuracy. It offers automated, customizable response actions and delivers threat data via tools like Teams, Slack, ServiceNow, and SIEM platforms.
Download PDF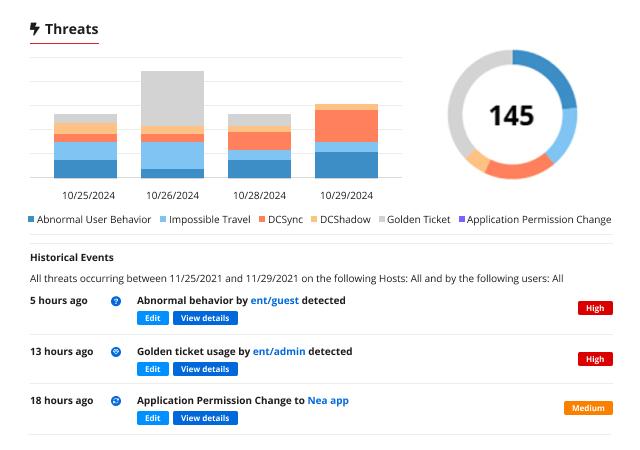
Netwrix Threat Prevention
Netwrix Threat Prevention protects critical systems like Active Directory, Exchange, and file systems by monitoring user behavior, alerting on suspicious activity, and intercepting threats at the source for added visibility and security.
Download PDF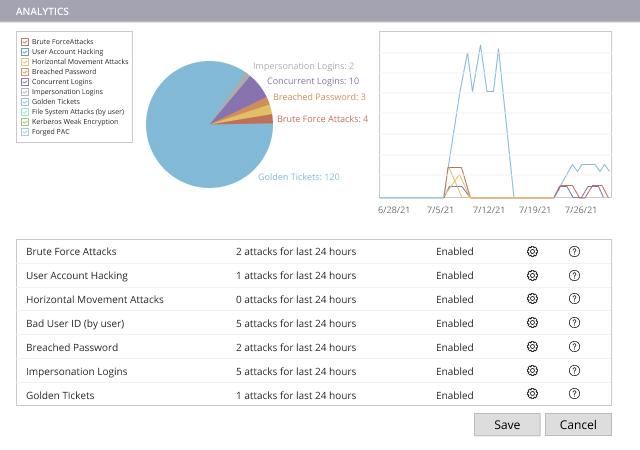
FAQs
Share on
