Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
A Pass-the-Ticket (PtT) attack exploits weaknesses in the Kerberos authentication protocol used in Windows Active Directory environments. This allows attackers to bypass traditional password-based authentication and even MFA mechanisms, granting them unauthorized access to critical systems and resources.
Attribute | Details |
|---|---|
|
Attack Type |
Pass-the-Ticket (PtT) |
|
Impact Level |
High |
|
Target |
Businesses, Government, Cloud-connected Active Directory |
|
Primary Attack Vector |
Kerberos Ticket Reuse |
|
Motivation |
Espionage, Privilege Escalation, Persistence |
|
Common Prevention Methods |
Credential Guard, Least Privilege, Ticket Lifetime Limits, Smartcard-based Auth, Endpoint Hardening |
Risk Factor | Level |
|---|---|
|
Potential Damage |
High |
|
Ease of Execution |
Medium-High |
|
Likelihood |
Medium |
What is a Pass-the-Ticket Attack?
A Pass-the-Ticket (PtT) attack is a technique that attackers use to steals a valid Kerberos ticket, typically a Ticket Granting Ticket (TGT) or a Ticket Granting Service (TGS), and reuses it to impersonate the legitimate user. Because the attacker presents an already issued, cryptographically valid Kerberos ticket, they can access network resources without needing the user’s password and even bypass multi-factor authentication (MFA). Again, since these tickets are cryptographically valid, it is hard to detect their misuse without monitoring for unusual behavior or access patterns.
Attackers often combine PtT with Golden Ticket, Silver Ticket, and Kerberoasting to escalate privileges and maintain stealthy, persistent access within a Windows domain environment.
How Does a Pass-the-Ticket Attack Work?
A Pass-the-Ticket attack unfolds in a series of quiet moves: the attacker gains unauthorized access to the network, steals a valid Kerberos ticket from memory, and replays it to impersonate the user. This turns one stolen ticket into broad access to on-premises and cloud resources.
Here is how each stage of the attack unfolds.
1. Initial Compromise
The attacker gains initial access to the network through tactics like phishing, malware, or stolen credentials, and may then perform local privilege escalation to obtain access to the LSASS (Local Security Authority Subsystem Service) process memory where Kerberos tickets are stored.
2. Ticket Extraction
Using tools such as Mimikatz, Rubeus, Kekeo, or Creddump7, the attacker extracts Ticket Granting Tickets (TGTs) and Ticket Granting Services (TGSs) from LSASS memory.
3. Ticket Injection
The attacker injects the stolen ticket into his or her own session (for example, with mimikatz kerberos::ptt). This enables the attacker to impersonate the legitimate account.
4. Lateral Movement
Armed with a valid ticket, the attacker accesses other machines, network shares, or services across the domain, bypassing password and MFA checks.
5. Privilege Escalation
From newly compromised systems, the attacker steals tickets belonging to higher-privileged accounts, say Domain Admins, for greater control.
6. Persistence
Attackers take advantage of the default Kerberos ticket lifetime (about 10 hours) by reusing or renewing stolen tickets before they expire. They tend to automate this process of periodically extracting or refreshing tickets to maintain continuous access. For long-term persistence, they may create a Golden Ticket, which is a forged Ticket-Granting Ticket signed with the domain’s KRBTGT key. This Golden Ticket provides unlimited and undetectable access until the key is reset.
7. Hybrid Cloud Compromise
In single sign-on or hybrid environments, the attacker can use stolen Kerberos tokens to access cloud services like Microsoft 365 and Microsoft Entra ID.
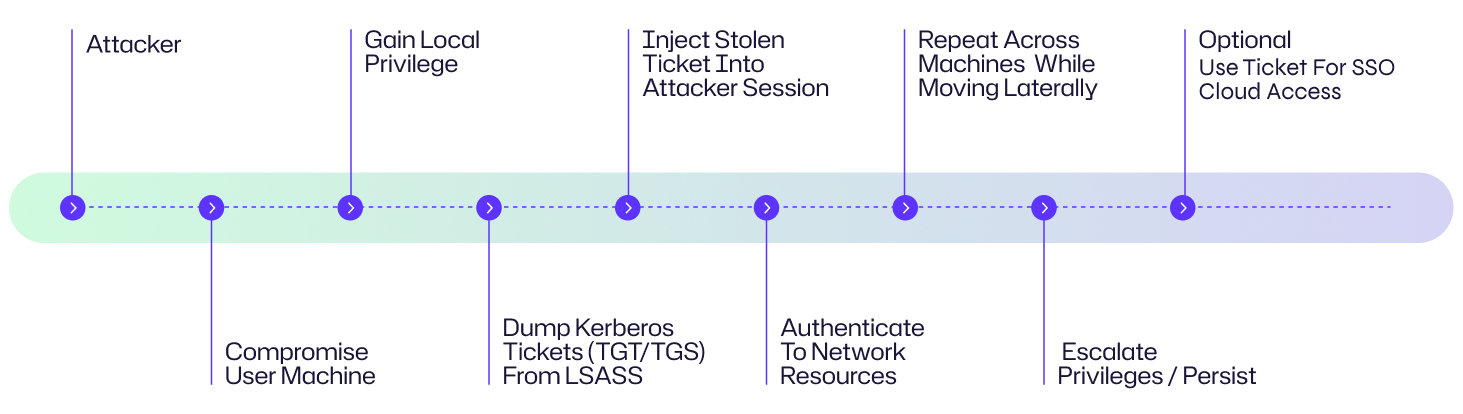
Attack Flow Diagram
The following example scenario can help you understand how a Pass-the-Ticket attack may look in a real world situation.
An employee at a financial services company unknowingly downloads malware from a phishing email, leading to a breach. The attacker exploits a local vulnerability to gain SYSTEM privileges and dumps LSASS memory to steal a Kerberos Ticket Granting Ticket. Injecting this valid ticket into their own session, the attacker moves laterally to file servers and a domain administrator’s workstation, harvests higher-privilege tickets, and eventually maintains persistence in the domain. Because the company’s on-prem and cloud environments are linked, the attacker reuses the stolen Kerberos credentials to access Microsoft 365 mailboxes and Microsoft Entra ID resources, all while appearing as a legitimate user. Security teams stay unaware until sensitive data has been exfiltrated.
The diagram illustrates a typical Pass-the-Ticket attack chain, from initial network foothold to undetected persistence across the network.
Examples of a Pass-the-Ticket Attack
Pass-the-Ticket techniques are widely used by advanced attackers and ransomware groups, as shown in the following real-world cases.
Case | Impact |
|---|---|
|
APT29 (Cozy Bear/Nobelium) |
APT29 (aka Cozy Bear/Nobelium) is known for sophisticated Kerberos abuse, including Pass-the-Ticket and Golden Ticket techniques. APT29 has repeatedly targeted US government agencies, political organizations, and global enterprises. During the 2016 intrusions into US political networks and the 2020 SolarWinds supply-chain campaign, this group leveraged Pass-the-Ticket techniques to move laterally, maintain long-term access to internal resources, and prolonged domain persistence across both on-premises and cloud environments. |
|
APT10 (Operation Cloud Hopper) |
Operation Cloud Hopper was a years-long global espionage campaign (roughly 2014–2017) in which APT10 (a Chinese state-sponsored threat group) compromised many managed-service providers (MSPs) and then their customers. Most of the victims were private companies or government agencies whose identities were not fully disclosed. Investigators (PwC/BAE’s 2017 report and later Mandiant analysis) observed that during these intrusions, APT10 used the Pass the Ticket attack to seal and replay Kerberos service tickets for lateral movement. |
|
BRONZE BUTLER (Tick) |
The advanced persistent threat group BRONZE BUTLER (also known as Tick), that targeted Japanese heavy industry (2016–2019), has been documented using the Pass-the-Ticket technique as part of its cyber espionage operations. According to MITRE ATT&CK®, BRONZE BUTLER has created and reused forged Kerberos Ticket Granting Ticket (TGT) and Ticket Granting Service (TGS) tickets for persistent administrative access across targeted networks, facilitating long-term surveillance and intellectual property theft. |
Consequences of Pass-the-Ticket Attack
The consequences of a Pass-the-Ticket attack can be severe and span multiple dimensions.
Impact Area | Description |
|---|---|
|
Financial |
A PtT attack can trigger severe financial losses. Stolen customer data, intellectual property, or financial records may be sold on the dark web, and attackers may demand ransom. Organizations may also face regulatory fines and legal fees, including litigation liabilities. Moreover, system recovery costs and forensic investigation expense can escalate the overall financial impact. |
|
Operational |
A PtT attack can disrupt daily operations as attackers can disable services, alter configurations, or deploy malware. IT teams must allocate significant resources to isolate and remediate affected systems as part of threat containment and recovery efforts. |
|
Reputational |
A PtT breach can erode customer trust and attract negative media attention, which can drive customers and partners away. This delivers a serious blow to the company’s reputation, and it may take years of significant investment in PR and security improvements to rebuild it. |
|
Legal/Regulatory |
Organizations may face hefty fines for violating data-protection laws such as Europe’s GDPR, or US healthcare laws like HIPAA, or even SOX. In addition to regulatory penalties, companies can face lawsuits from affected parties and be required to implement costly security upgrades to achieve compliance. |
|
Cloud Exposure |
PtT attacks can spread from on-premises Active Directory into cloud services like Microsoft Entra ID, letting attackers use stolen tickets for (unauthorized) access to cloud apps, data, and infrastructure. As the breach extends beyond on-premises system, containing it can become a complex affair. |
Common Targets of a Pass-the-Ticket Attack: Who is at risk?
Organizations that rely on Windows Active Directory and Kerberos authentication are prime targets for Pass the Ticket attacks. Environments with numerous privileged accounts, cached tickets, and interconnected systems also provide favorable conditions for undetected, broad access with stolen tickets. Some common targets are:
|
Large Enterprises |
These organizations are prime targets due to their extensive reliance on Kerberos for authentication across departments and services.When an organization has a large number of high-privilege user accounts and its systems store Kerberos tickets in memory for convenience, it creates a vast attack surface. |
|
Government Agencies |
Agencies store highly sensitive data and their AD environments are complex. Attackers benefit from the scale of the network and long ticket lifetimes to stay undetected and maintain long-term access. |
|
Financial Institutions |
Banks and other financial institutions are tempting targets because they extensively use single sign-on (SSO) and ticket-based authentication. If attackers steal Kerberos tickets, they can straight away access critical systems that handle financial records and payment operations. |
|
Healthcare Systems |
Healthcare systems store vast amounts of sensitive patient data, which in itself is very attractive to attackers. Their use of Active Directory and Kerberos authentication across clinical and administrative networks provides multiple opportunities to steal and reuse Kerberos tickets for lateral movement. |
|
Critical Infrastructure |
Utilities, energy providers, and manufacturing plants often depend on Windows-based control systems and Kerberos authentication. Compromised tickets can disrupt production or even operational technology (OT) environments. |
|
Cloud-Connected Organizations |
When a company connects its on-premises Active Directory to Microsoft Entra ID or other cloud services, stolen Kerberos tickets can let attackers hop from the internal network into cloud apps and data, turning a local breach into a much larger cloud compromise. |
Users and Roles at Risk
Any account that regularly holds or caches Kerberos tickets, especially those with elevated privileges or broad network access, is a prime target.
|
Domain Admins |
Kerberos tickets issued to Domain Admins provide full control of the Active Directory forest, so a stolen ticket can give attackers unrestricted access to every system. |
|
T Staff / System Admins |
These users frequently log into many servers and workstations, which increases the number of cached tickets in memory and creates more opportunities for theft. |
|
Service Accounts |
Often configured with long-lived or non-expiring credentials, service accounts can retain Kerberos tickets for extended periods. |
|
Privileged Users (Tier 0/1) |
These accounts manage core Active Directory components and often reuse credentials across endpoints, making any stolen ticket a powerful tool for lateral movement. |
|
Remote Workers with VPN/RDP |
Employees connecting over VPN or RDP may log into untrusted or compromised devices, which increases the risk of ticket theft. |
|
Users in Hybrid SSO Setups |
If a company’s on-premises Active Directory is federated with a cloud identity service such as Microsoft Entra ID through AD FS, stolen Kerberos tickets can be replayed to access cloud applications and data. |
Risk Assessment
Risk levels for the Pass-the-Ticket attack are based on its impact, prerequisites, and observed use by advanced threat actors.
Risk Factor | Level |
|---|---|
|
Potential Damage |
High Successful PtT can provide domain-wide access, with attackers stealing sensitive data, disrupting critical services, and maintaining long-term persistence. It can also lead to full enterprise compromise if domain controllers are affected. |
|
Ease of Execution |
Medium–High Tools such as Mimikatz and Impacket can automate extraction of Kerberos tickets from LSASS memory and their subsequent injection or replay in an attacker-controlled session. However, the attacker must first gain administrative or SYSTEM-level access on at least one machine to extract the ticket. |
|
Likelihood |
Medium PtT attacks are well-documented and used by advanced groups like APT29. Although an attacker first needs high-level access to pull it off, organizations with weak monitoring and unpatched systems can still be prime targets. Hence the overall likelihood stands at medium: not high, but not low either. |
How to Prevent Pass-the-Ticket Attacks
To reduce the chances of a Pass-the-Ticket attack, organizations should implement measures such as harden the operating system, limit ticket lifetimes, minimize administrative exposure, and detect suspicious activity.
Enable Credential Guard
Windows Defender Credential Guard isolates the LSASS process in a secure virtualized environment. Enabling it on all compatible Windows systems significantly reduces the risk of ticket theft, as it prevents attackers from dumping Kerberos tickets or other credentials from LSASS memory.
Limit Ticket Lifetime
The default lifespan of a Ticket Granting Ticket (TGT) is 10 hours. You can reduce this lifespan and enforce shorter renewal periods, so that any stolen ticket quickly becomes invalid. This minimizes the window of opportunity for an attacker to reuse a ticket.
Apply Least Privilege Principles
As a rule of thumb, grant admin rights only when they are needed and discourage the use of shared admin credentials. Use role-based access so that each user gets just the access their job requires. By limiting the number of privileged accounts and their scope, you reduce the chances for attackers to obtain the access they need to steal Kerberos tickets.
Avoid Ticket Caching on High-Value Systems
High-value systems may include domain controllers, PKI servers, and critical application hosts. Configure these to avoid storing TGTs in memory or on disk. If no tickets are cached, there is nothing for an attacker to steal even if the system is compromised.
Train Privileged Users
Human error is a frequent cause of security breaches, with studies citing it as the reason for anywhere from 74% to over 90% of incidents. With this in view, it is important to educate administrators and other high-privilege users to avoid logging into untrusted or lower-tier hosts. Using admin credentials only on hardened management workstations greatly lowers the risk of their Kerberos tickets being exposed to attackers.
Use Certificate-Based Authentication (PKINIT)
Implement Kerberos PKINIT (smart-card logon) to move from password-based to certificate-based authentication. Each Kerberos ticket then carries proof of a valid cryptographic certificate, which makes stolen tickets useless to an attacker and strengthens the Kerberos authentication chain.
Patch Regularly
Remember the WannaCry ransomware attack in 2017, where a cryptoworm exploited an unpatched vulnerability in Windows systems! To avoid such incidents, you must keep domain controllers, Key Distribution Centers (KDCs), and all Windows systems fully patched. Timely updates close known privilege-escalation and credential-theft vulnerabilities that could otherwise lead to ticket compromise.
Harden Endpoints
Apply strong security baselines to all servers and workstations. This includes disabling unnecessary services, enforcing strong authentication policies, enabling tamper protection, and deploying reputable endpoint detection and response (EDR) tools. A hardened endpoint makes it far more difficult for attackers to gain the high-level access required to extract Kerberos tickets.
Segment the Network: Contain lateral movement paths across systems.
Use network segmentation and tiered administration to limit lateral movement. With these barriers in place, attackers can use a stolen Kerberos ticket only within a limited segment, rather than moving freely across the environment.
How Netwrix Can Help
The Netwrix ITDR (Identity Threat Detection and Response) solution can detect, contain, and respond to Pass-the-Ticket and other Kerberos-based attacks. By combining real-time monitoring, analytics, and automated remediation, it helps organizations spot suspicious ticket activity early and stop lateral movement.
- Real-Time Monitoring: Netwrix ITDR continuously monitors your identity infrastructure, detecting anomalies like unusual Kerberos ticket requests, abnormal ticket lifetimes, and irregular logon patterns.
- Behavioral Analytics: The solution uses behavioral analytics to identify deviations from normal user behavior, such as unexpected TGS requests, authentication attempts at odd times, and unusual access patterns across the network.
- Alert Mechanisms: ITDR offers alerts for signs of credential misuse, such as identical tickets used across multiple machines. This helps administrators respond promptly to suspected PtT activities.
- Automated Incident Response: ITDR automates responses to detected threats, such as revoking compromised tickets, quarantining affected endpoints, and resetting passwords for impacted accounts to contain an attack without delay.
- Session Isolation: It aids in quarantining or isolating affected endpoints and user sessions. In this way, attackers who have injected stolen Kerberos tickets into their sessions cannot move laterally.
- Integration with UEBA and SIEM: By integrating with UEBA (User and Entity Behavior Analytics) and SIEM (Security Information and Event Management) systems, ITDR ensures comprehensive tracking and correlation gaps that can detect credential abuse.
- SACL Application: It enables you to apply System Access Control Lists (SACLs) selectively to high-risk AD objects and systems, which helps monitor changes or access on those objects, as well as monitor ticket access and potential exploitation paths.
- Response Planning: Netwrix ITDR helps security teams create recovery playbooks, ensuring that a domain or even an entire forest is restored swiftly in the event of a compromise. It also equips teams with readiness to reset compromised credentials and review suspicious access logs tied to ticket activity.
Detection, Mitigation and Response Strategies
To contain Pass-the-Ticket attacks, organizations should combine strong detection, proactive mitigation, and rapid incident response.
Detection
To detect a PtT attack early, organizations must continuously monitor major security events and behavior patterns. And early detection is critical because attackers can move laterally as soon as they steal a Kerberos ticket.
- Monitor Event IDs 4768, 4769, 4624 (type 3), 4672: Track these event IDs to spot unusual authentication activity. Windows Event Viewer is good for spot checks and small environments, but not scalable for 24/7 monitoring. For enterprise-scale detection, set up continuous forwarding to a SIEM system with alerts tuned for these event IDs and suspicious patterns such as unusual ticket lifetimes or logons from unexpected endpoints. Here is what each ID represents:
- 4768: Kerberos TGT (Ticket Granting Ticket) request
- 4769: Service Ticket (TGS) request
- 4624 (Type 3): Network logon
- 4672: Special privileges assigned to a new logon (for example, admin rights)
- Watch for suspicious patterns, such as:
- TGS requests without recent TGTs from the same host - This may indicate forged or replayed tickets
- Logins from unusual endpoints or at odd times - Signals lateral movement or compromised accounts
- Logs with missing fields like Account Domain or Logon GUID - Can point to tampered or forged tickets
- Identical tickets used across multiple machines - Suggests ticket reuse or replay
- Unusual ticket lifetimes or forged expiration timestamps - A hallmark of Golden Ticket attacks
- Monitor use of tools like Mimikatz, Rubeus, Kekeo, etc.: Detect attempts to run tools such as Mimikatz, Rubeus, or Kekeo, which attackers use to extract and inject Kerberos tickets. Use EDR or antivirus to flag known signatures and suspicious LSASS memory access, enable detailed Windows/Sysmon logging (for example, Event 4688 for process creation, Event 10 for LSASS access), and forward these logs to a SIEM for real-time alerts.
- Leverage UEBA and SIEM: Use UEBA and SIEM platforms to spot Pass-the-Ticket activity by correlating authentication logs, Kerberos events, and user behavior across the environment. This centralized approach highlights anomalies, such as unusual logon times, abnormal ticket lifetimes, and identical tickets on multiple hosts, that isolated system monitoring might overlook.
- Apply SACLs to sensitive AD accounts and systems: System Access Control Lists (SACLs) generates detailed audit logs whenever Kerberos tickets are requested or used, so you can audit and track Kerberos ticket access to high-value resources.
Mitigation
Proactive steps can greatly reduce the chances of a successful Pass-the-Ticket attack and invalidate stolen tickets before they can be abused.
- Rotate the KRBTGT account password twice: Perform a double password rotation on the KRBTGT account to invalidate all existing Kerberos tickets, including any Golden Tickets that the attackers may have forged. With this, only freshly issued tickets remain valid.
- Use Credential DoubleTap: When a user or service account is compromised, quickly reset its password twice. This ensures that any Kerberos tickets issued under the old password hashes are immediately rendered useless.
- Enforce Session Isolation and Purge Cached Tickets: Administrators should be required to log in only from hardened management workstations, so as to separate privileged sessions from everyday endpoints. It is also important to schedule regular klist purge tasks to remove cached Kerberos tickets from memory, minimizing what an attacker could steal.
Response
When a Pass-the-Ticket incident is detected, swift containment and thorough remediation are essential to stop lateral movement and restore a secure state.
- Quarantine compromised endpoints: Immediately isolate affected machines from the network either manually or via automated response tools to stop lateral movement.
- Reset passwords of affected users and admin accounts: Change passwords for all accounts that may have had Kerberos tickets stolen, including service and administrative accounts. This instantly invalidates any tickets derived from their old credentials.
- Review access patterns and logs: Examine Kerberos event logs, authentication attempts, and ticket activity to trace the attacker’s path and identify how the attack spread.
- Revoke Active Sessions and Expire Tickets: Revoke access through session invalidation or forced ticket expiration. This will force logoffs, invalidate Kerberos sessions, and shorten ticket lifetimes, ensuring that any stolen or replayed tickets can no longer be used.
Industry-Specific Impact
Pass-the-Ticket (PtT) attacks can affect every sector, but the consequences vary depending on the type of data and systems an organization manages.
Industry | Impact |
|---|---|
|
Finance |
Financial institutions handle high-value transactions and store vast amounts of personal and corporate data. A successful PtT attack could let an intruder access customer banking details, initiate unauthorized fund transfers, and manipulate payment systems. Such breaches may lead to direct monetary loss, regulatory penalties, and severe reputational damage. |
|
Healthcare |
Hospitals and healthcare providers rely on electronic health records (EHR) and other health information technology (HIT) systems that are interconnected across facilities. By reusing stolen Kerberos tickets, attackers can extract patient records, disrupt critical medical operations, or deploy ransomware that locks HIT systems. The result can be compromised patient privacy, delayed care, and costly downtime. |
|
Government |
Government networks are prime targets for espionage. A PtT attack can grant unauthorized access to sensitive or classified data, enable persistent surveillance of internal communications, and even create backdoors in supply chains or critical infrastructure. Such compromises threaten national security, expose state secrets, and erode public confidence in government systems. |
Attack Evolution & Future Trends
With time and technology, PtT attacks have evolved into faster, more automated techniques. Here are some trends that highlight how PtT is becoming more sophisticated and harder to detect.
Automation through Scripting and Red-Team Tools
Attackers now rely on tools such as Mimikatz pass the ticket, Rubeus, and Impacket to script every stage of a PtT attack, from ticket extraction to injection. This reduces manual effort and facilitates faster, large-scale compromises. These tools are customizable (for example, commands can be modified and plugins added) and they integrate easily into automated penetration-testing or red-team workflows. As a result, attackers can carry out multiple actions, such as ticket extraction, privilege escalation, and lateral movement into a single automated sequence. Overall, this signifies that even less experienced adversaries can launch a PtT attack.
Chaining PtT with Other Kerberos Exploits
Recent reports on multi-stage breaches show that intrusions rarely involve PtT alone. Threat actors combine it with other Kerberos abuses, such as Kerberoasting, Pass-the-Hash (PtH), and Silver or Golden Ticket techniques to launch a coordinated attack that enables them to pivot across systems, evade detection, escalate privileges, and build long-term access within enterprise networks.
Token Bridging: Extending PtT Attacks into the Cloud
As organizations adopt hybrid identity solutions, attackers are exploring ways to leverage on-premises Kerberos tickets to obtain cloud authentication tokens. In “token bridging” scenarios, a stolen Kerberos ticket can be exchanged for SAML or OIDC tokens. This grants the attacker unauthorized access to SaaS applications and cloud workloads, effectively extending a PtT attack into the cloud - where traditional on-prem monitoring may not detect the intrusion.
Use of LOLBins Alongside PtT for Stealth
Attackers are turning everyday Windows utilities, known as living-off-the-land binaries (LOLBins), into stealthy weapons. Tools like klist, runas, and common PowerShell commands come pre-installed and are signed by Microsoft, so they look perfectly legitimate. When threat actors use them to carry out Pass-the-Ticket attacks, their activity blends in with normal admin work, making it harder for defenders to distinguish malicious behavior from routine system management.
Key Statistics & Infographics
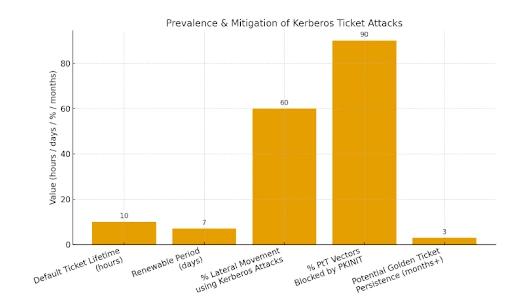
Kerberos ticket theft remains one of the most effective ways attackers move laterally and stay hidden.These quick facts highlight why Pass-the-Ticket defense needs constant attention:
- By default, a stolen Ticket-Granting Ticket (TGT) can be reused for up to 10 hours and renewed for an entire week, unless administrators define policies that shorten the lifetime.
- Stolen TGTs can bypass MFA, password policies, and lockout protections.
- More than 60% of lateral movement campaigns use some form of Kerberos ticket attack.
- Smartcard (PKINIT) authentication can block over 90% of PtT vectors.
- Golden Ticket misuse can persist for months if KRBTGT rotation is not enforced.
The following bar graph highlights critical Kerberos-related risk and mitigation data.
Final Thoughts
Kerberos tickets are the keys to your kingdom, and must be protected like crown jewels. Organizations should harden endpoints, shorten ticket lifetimes, and monitor relentlessly, because attackers move fast - they scan the network automatically, grab Kerberos tickets in just seconds, and pivot across systems before most teams even notice. Defense demands equal urgency - continuous Kerberos monitoring and and quickly shutting down any suspicious sessions. Fortify your authentication systems now or risk watching intruders use your own credentials to walk straight through the gates.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
DCSync Attacks Explained: Threat to Active Directory Security
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Kerberoasting Attack – How It Works and Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
