DCSync Attacks Explained: Threat to Active Directory Security
DCSync attacks are a stealthy technique used by attackers to impersonate a domain controller and request sensitive account information from Active Directory.
Attribute | Details |
|---|---|
|
Attack Type |
DCSync Attack |
|
Impact Level |
Critical |
|
Target |
Government, Healthcare, Energy, Education, Technology and Cloud Service Providers, Financial Services |
|
Primary Attack Vector |
Network, Privileged Account Abuse |
|
Motivation |
Espionage, Financial Gain, Persistence |
|
Common Prevention Methods |
Least Privilege Enforcement, Auditing, Network Detection |
Risk Factor | Level |
|---|---|
|
Potential Damage |
Critical |
|
Ease of Execution |
Medium |
|
Likelihood |
High |
What is a DCSync Attack?
A DCSync attack is a technique used by threat actors to simulate the behavior of a domain controller (DC) in an Active Directory (AD) environment. The attack leverages legitimate features of the Directory Replication Service Remote Protocol (MS-DRSR) to extract sensitive data from the domain.
Instead of deploying malware or injecting code, the attacker uses tools (such as Mimikatz) to impersonate a DC and request replication of credential data — particularly password hashes for user accounts, including KRBTGT and domain admins.
A DCSync attack usually has the following intentions:
- Extract Password Hashes — Attackers retrieve NTLM password hashes of domain accounts, including those of privileged users. These hashes can be cracked offline or used directly in pass-the-hash or Golden Ticket attacks.
- Achieve Domain Dominance — By obtaining the KRBTGT account hash, attackers can forge Kerberos Ticket Granting Tickets (TGTs), enabling persistence and complete control over the domain. This allows long-term, stealthy access to the entire AD environment.
This attack is dangerous for several reasons.
- No Malware Required — DCSync does not rely on malicious binaries; it abuses legitimate functionality, making it harder for antivirus or EDR tools to detect.
- Mimics Legitimate Traffic — The attack mimics standard Active Directory replication requests, making it difficult to distinguish from normal operations.
- Used by APTs and Cybercriminal Gangs — Advanced persistent threat (APT) groups and ransomware gangs frequently employ DCSync attacks to escalate privileges and establish persistence.
How Does a DCSync Attack Work?
A DCSync attack unfolds in a series of stealthy steps that mimic legitimate Active Directory behavior. Here is a step-by-step breakdown of the attack.
1. Compromise an Account
The attacker first gains access to a privileged account that has replication rights. This usually means compromising:
- A Domain Admin account, or
- A system account with delegated replication permissions, or
- An account with "DS-Replication-Get-Changes" and "DS-Replication-Get-Changes-All" rights
These permissions allow the attacker to mimic a DC's replication requests.
2. Discover a DC
Next, the attacker locates an accessible domain controller within the network. Tools like nltest,nslookup, or built-in Windows commands can help identify DCs.
3. Impersonate a DC
Using tools such as the following, the attacker crafts requests as though they were a legitimate DC participating in Active Directory replication.
- Mimikatz (
lsadump::dcsync) - Impacket's secretsdump.py
4. Request Data
The attacker sends a replication request using the DRSUAPI interface, specifically the GetNCChanges function - the same API call used in legitimate DC-to-DC replication.
5. Extract Password Hashes
The DC responds with the requested data, including:
- NTLM hashes
- Kerberos keys
- KRBTGT account hash (critical for creating Golden Tickets)
This data enables password cracking, impersonation, or pass-the-hash attacks.
6. Launch Follow-on Attacks
With password hashes in hand, the attacker can:
- Forge Golden Tickets (unlimited, long-term access)
- Conduct Pass-the-Ticket or Pass-the-Hash attacks
- Escalate privileges or move laterally across the domain
Attack Flow Diagram
The DCSync attack flow demonstrates how a threat actor can abuse legitimate Active Directory replication protocols to extract password hashes and gain long-term, stealthy control over a domain.
Here is a visual concept of the attack.
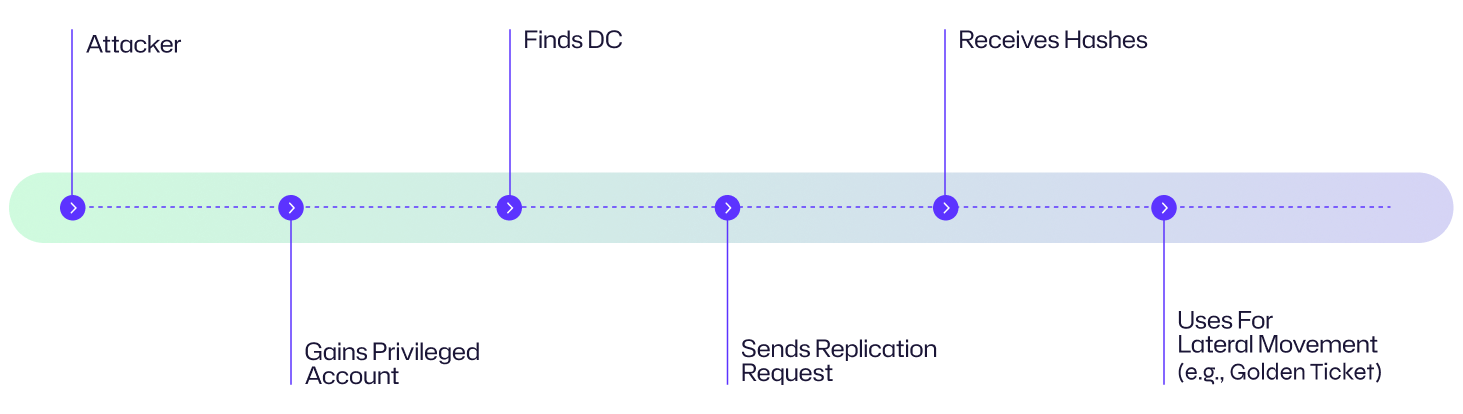
Let’s look at an example from an organization’s perspective.
In a mid-sized financial services firm, a phishing email leads to the compromise of a helpdesk technician's credentials. The attacker uses these credentials to elevate privileges via Kerberoasting and eventually gains access to a Domain Admin account. With this access, the attacker identifies a DC using internal DNS and leverages the Mimikatz DCSync function to request replication data. The DC, unaware of the malicious intent, responds with password hashes, including that of the KRBTGT account. The attacker then creates a Golden Ticket — granting unrestricted, long-term access to the organization’s network — and quietly exfiltrates sensitive client data over several weeks without triggering alarms.
Examples of DCSync Attacks
DCSync attacks are a powerful post-exploitation technique where an attacker mimics the behavior of a domain controller to extract sensitive credentials from Active Directory. Below are real-world examples that demonstrate the impact of DCSync attacks.
Case | Impact |
|---|---|
|
APT40 / Leviathan (2024) |
In 2024, APT40 (also known as Leviathan), a China-based state-sponsored cyber espionage group, employed DCSync attacks to steal credentials from targeted private and government networks. A joint advisory released on July 9, 2024, by cybersecurity agencies including the Australian Cyber Security Centre (ACSC) and the US Cybersecurity and Infrastructure Security Agency (CISA) highlighted that DCSync is part of APT40’s tradecraft. |
|
UNC5330 (2024) |
In 2024, the China-linked threat actor UNC5330 exploited vulnerabilities in Ivanti Connect Secure VPN appliances to perform DCSync attacks during lateral movement within compromised networks. The attack enabled the threat actor to gain deep and persistent access to targeted networks and potentially exfiltrate sensitive data from both government and private sector environments. The stealthy nature of the attack made detection challenging, increasing the dwell time and expanding the scope of compromise across affected organizations. |
|
Mustang Panda (2023) |
In 2023, the China-linked advanced persistent threat (APT) group Mustang Panda, also known as Stately Taurus, orchestrated a cyber-espionage campaign targeting the Philippine government. The attackers gained initial access through spear-phishing emails and deployed tools such as MimiKatz to perform DCSync attacks. The campaign had a significant impact, enabling Mustang Panda to maintain long-term access to the compromised government network. By harvesting credentials and establishing persistence, they were able to exfiltrate sensitive documents and other critical data over an extended period. |
|
LAPSUS$ (2022) |
In 2022, the LAPSUS$ cybercriminal group, also tracked as DEV-0537, employed DCSync attacks to escalate privileges within targeted organizations. After gaining initial access, they used tools like Mimikatz to perform DCSync operations, enabling them to harvest credentials, including those of domain administrators. This allowed for lateral movement and deeper infiltration into victim networks. LAPSUS$ compromised several high-profile organizations, including Microsoft, Okta, and T-Mobile. With domain administrator credentials, they gained extensive access to internal systems, enabling them to exfiltrate sensitive data such as source code and customer information. The group's tactics, which combined credential theft with public data leaks and extortion, disrupted operations and posed significant security challenges for the affected entities. |
Consequences of a DCSync Attack
DCSync attacks pose a serious threat to enterprise security. Once successful, these attacks can compromise the very foundation of identity and access management, leading to widespread and long-lasting consequences. The fallout may include costly incident response efforts, business disruption, damage to brand trust, and potential legal action or regulatory penalties for failing to protect sensitive information.
Impact Area | Description |
|---|---|
|
Financial |
By exploiting Active Directory replication features, attackers can extract credentials, including those of domain administrators, facilitating unauthorized access to sensitive systems. This breach can lead to significant financial losses due to business disruption, incident response costs, and potential ransom payments. For instance, the average cost of a data breach reached $4.88 million in 2024, with companies like MGM Resorts International reporting a $100 million hit to their quarterly results following a cyberattack. |
|
Operational |
DCSync attacks compromise the core of an organization's IT infrastructure — Active Directory — resulting in loss of control over authentication and authorization processes. This can cause widespread operational disruptions, including unauthorized access to systems, data exfiltration, and potential downtime, severely affecting business continuity. |
|
Reputational |
The exposure of sensitive data and prolonged unauthorized access can erode trust among customers, partners, and stakeholders. In government and regulated industries such as healthcare, where data confidentiality is paramount, such breaches can lead to a loss of public confidence and long-term reputational damage. |
|
Legal/Regulatory |
Organizations may face legal actions and regulatory penalties for failing to protect sensitive information adequately. Non-compliance with data protection regulations like GDPR or HIPAA can result in substantial fines and mandatory corrective measures. |
Common Targets of a DCSync Attack: Who is at risk?
To execute a DCSync attack, adversaries target specific accounts and permissions within the network. Below is an overview of common targets susceptible to such attacks.
High-Privilege Accounts
|
KRBTGT Account |
The KRBTGT account is integral to Kerberos authentication, encrypting and signing all Kerberos tickets within the domain. Compromising this account enables attackers to forge Golden Tickets, granting them unrestricted access across the domain. |
|
Administrator Accounts |
Accounts belonging to groups such as Domain Admins, Enterprise Admins, and Administrators possess elevated privileges by default. If compromised, these accounts can be used to perform DCSync attacks, facilitating lateral movement and further exploitation. |
|
Service Accounts with Replication Rights |
Certain service accounts, like those used by Microsoft Entra Connect (e.g., MSOL_ accounts), require replication permissions for legitimate operations. However, if these accounts are compromised, attackers can leverage their permissions to execute DCSync attacks. |
Domain Controller Machine Accounts
|
DC Computer Accounts |
Domain Controller (DC) machine accounts inherently possess replication rights. While essential for domain operations, if an attacker gains control over a DC or its credentials, they can initiate DCSync attacks to extract credential data from other DCs. |
Non-default or Misconfigured Accounts
|
Accounts with Delegated Replication Permissions |
Accounts not originally intended for replication tasks may inadvertently receive Replicating Directory Changes permissions due to misconfigurations. Such non-default accounts become prime targets, as attackers can exploit these permissions to perform DCSync attacks without needing full administrative rights. |
Risk Assessment
Understanding the risk associated with DCSync attacks involves evaluating their likelihood, potential severity, the sophistication of the techniques employed, detection difficulty, and potential impact.
|
Likelihood: High |
DCSync attacks are highly probable, especially in environments where non-default accounts have been inadvertently granted replication permissions. Such misconfigurations can occur due to improper delegation or oversight and are often overlooked, providing attackers with the necessary access to perform DCSync operations. Tools like Mimikatz further increases their likelihood. |
|
Severity: High |
DCSync attacks often employ "living-off-the-land" techniques, utilizing legitimate system tools and processes. This approach allows attackers to operate stealthily, evading traditional security measures and prolonging their presence within the network. |
|
Attack Sophistication: Critical |
By obtaining the KRBTGT account's password hash through DCSync, attackers can forge Golden Tickets. This grants them unrestricted access across the domain, enabling persistent and covert operations that are challenging to detect and mitigate. |
|
Detection Difficulty: High |
Detecting DCSync attacks is challenging because they exploit legitimate replication protocols. Attackers can use tools like Mimikatz to perform these attacks without deploying malware, making traditional detection methods less effective. |
|
Potential Impact: Critical |
The consequences of a DCSync attack are critical. Attackers can gain access to sensitive data, disrupt operations, and cause reputational damage. In regulated industries, such as healthcare and finance, this can also lead to legal and regulatory penalties. |
How to Prevent DCSync Attacks
Preventing DCSync attacks requires a multifaceted approach that combines strict access control, continuous monitoring, and strategic segmentation of your Active Directory (AD) environment. Below are key strategies to mitigate the risk of such attacks.
Enforce Least Privilege
Limit replication rights strictly to accounts that require them. Regularly audit and remove unnecessary permissions, especially the following extended rights:
- Replicating Directory Changes
- Replicating Directory Changes All
- Replicating Directory Changes in Filtered Set
These permissions are often exploited in DCSync attacks.
Audit and Monitor
Implement continuous monitoring to detect unauthorized replication requests. Utilize tools such as Netwrix PingCastle and Netwrix Threat Manager to scan for non-default accounts with replication permissions and other risky configurations. Regular audits can uncover misconfigurations that may otherwise go unnoticed.
Control ACEs
Review and manage Access Control Entries (ACEs) to prevent unintended permissions. For instance, the Enterprise Key Admins group may inadvertently have full control over the Domain Naming Context, posing a security risk. Ensure that only necessary permissions are granted to each security principal.
Segment AD Tiers
Adopt a tiered administrative model to separate high-privilege accounts from being used in standard user environments. This segmentation minimizes the risk of credential exposure on less secure workstations and helps contain potential breaches.
Implement Advanced Detection Mechanisms
Deploy Security Information and Event Management (SIEM) solutions to monitor for specific events indicative of DCSync attacks, such as unusual Event ID 4662 entries. Focus on detecting replication requests from non-domain controller accounts, which can signify malicious activity.
Netwrix Support
Netwrix offers robust solutions for DCSync attack detection and mitigation. Netwrix Threat Manager and Threat Prevention enhance your organization's ability to detect and prevent DCSync attacks, thereby strengthening the overall security posture of your Active Directory environment.
Netwrix Threat Manager: Detecting DCSync Behavior
Netwrix Threat Manager continuously monitors AD replication activities to identify patterns indicative of DCSync attacks. It detects unusual replication requests, especially those originating from non-domain controller machines, and provides detailed insights into the suspicious activity, including the source, targeted accounts, and the nature of the replication request. This real-time detection enables security teams to respond promptly to potential threats.
Netwrix Threat Prevention: Blocking Unauthorized Replication
Netwrix Threat Prevention proactively safeguards your AD environment by enforcing policies that prevent unauthorized replication activities. When a DCSync-like behavior is detected, it can automatically block the offending account or workstation from performing further replication actions. This immediate response mechanism helps contain the threat, buying valuable time for incident response teams to investigate and remediate the issue.
Detection, Mitigation and Response Strategies
A suspected DCSync attack involves an adversary impersonating a domain controller to extract credentials from Active Directory using replication rights. Swift detection and response are critical to contain the threat.
Early Warning Signs
Here are key signs to monitor for an early detection of a DCSync attack.
Unexpected Replication Requests
|
Symptoms |
Non-DC machines issuing replication requests to the domain controller. |
|
How to Detect |
|
Security Event ID 4662
|
Symptoms |
Surge in |
|
Details |
|
Event ID 4670 / 4624 / 4742 Patterns
|
Additional Useful Events |
|
Immediate Response
When a DCSync attack is suspected or detected, rapid containment is critical.
Isolate the Compromised System
- Immediately disconnect affected systems from the network.
- Suspend any unusual accounts with replication rights (like
DS-Replication-Get-Changes-All).
Revoke Elevated Privileges
Remove users or services from:
- Built-in security groups in Active Directory, such as Administrators, Domain Admins, and Enterprise Admins.
- Accounts with
Replicating Directory Changesrights.
Audit & Investigate Logs
Review logs on domain controllers, especially:
- Security Event Logs: Focus on replication-related entries
- Directory Service Logs
- Sysmon Logs: Process creation and network connections
Long-term Mitigation Strategies
Proactive defense significantly reduces DCSync risks.
Audit AD Replication Rights
- Regularly review permissions using tools like BloodHound and PowerView.
- Audit for unexpected members in privileged AD groups.
Deploy Deception Mechanisms
- Employ deception techniques like placing honeypot accounts or decoy DC objects.
- Use tools like Canarytokens or ADDecoy to detect unauthorized access.
Implement Tiered Administrative Model
Separate duties by privilege levels (Tier 0, 1, 2).
- Tier 0: Direct access to domain controllers
- Tier 1: Server administration
- Tier 2: Workstation support
Enable Enhanced Auditing
- Turn on Advanced Audit Policy Configuration.
- Track directory service access, privilege use, and object modifications.
Secure Replication Protocols
- Block outbound RPC traffic from non-DC devices where feasible.
- Use firewall rules to restrict replication communication only between known DCs.
Industry-Specific Impact
The impact of a DCSync attack can vary widely across industries due to differences in regulatory requirements, data sensitivity, and infrastructure complexity. Whether in finance, healthcare, government, or tech, a successful DCSync attack can lead to credential theft, data breaches, compliance violations, and operational disruption.
Industry | Impact |
|---|---|
|
Healthcare |
In the healthcare sector, a DCSync attack can have severe consequences, including:
|
|
Finance |
In the financial sector, a DCSync attack poses a high-risk threat due to the sensitive nature of systems and data.
|
|
Retail |
In the retail industry, a DCSync attack can disrupt operations and undermine customer trust.
|
Attack Evolution & Future Trends
The DCSync attack technique has evolved into a critical component of modern adversarial toolkits. As defensive measures improve, DCSync tactics continue to adapt, integrating deeper into native system capabilities and leveraging emerging vulnerabilities for maximum impact.
Living-off-the-Land (LotL)
Attackers increasingly rely on native Windows tools and built-in Active Directory functionality to execute DCSync attacks without deploying external binaries. By exploiting replication privileges with standard protocols like DRSR, threat actors blend into normal network behavior. This Living-off-the-Land (LotL) approach reduces the forensic footprint and makes it harder for traditional signature-based detection mechanisms to flag malicious activity.
Toolset Expansion
While Mimikatz remains the most well-known tool for executing DCSync, alternatives like secretsdump.py from Impacket and emerging red team frameworks have expanded the attacker’s arsenal. These tools are often modular, open-source, and frequently updated; hence, they are more difficult to detect and block. Variants now include obfuscation and scripting capabilities that bypass traditional EDR solutions and adapt to updated security controls.
Advanced Detection Evasion
Sophisticated attackers have moved beyond simply exploiting DCSync — they now implement advanced tactics to cover their tracks. This includes disabling or tampering with Windows Event Logging, using encrypted or tunneled communication channels, and chaining DCSync with other stealth techniques. Some adversaries even execute DCSync-like functionality directly from memory to avoid disk writes and evade endpoint monitoring tools.
Trend Watch
DCSync's power is further amplified when combined with privilege escalation vulnerabilities. Exploits such as Zerologon (CVE-2020-1472) and PrintNightmare (CVE-2021-34527) allow attackers to rapidly elevate access to domain-level privileges, enabling the prerequisites for DCSync without needing long-term lateral movement. Future exploitation chains may rely on zero-day AD misconfigurations or supply chain flaws to trigger DCSync more quickly and covertly.
Key Statistics & Infographics
In 2024, more than a dozen advanced threat actors were linked to DCSync techniques in public reporting.
For instance, in December 2024, Arctic Wolf Labs identified a sophisticated cyberattack campaign targeting Fortinet FortiGate firewall devices. Threat actors exploited a suspected zero-day vulnerability to gain unauthorized access to the devices’ management interfaces, allowing them to alter firewall configurations and extract credentials using DCSync.
Industries most affected by DCSync-related incidents
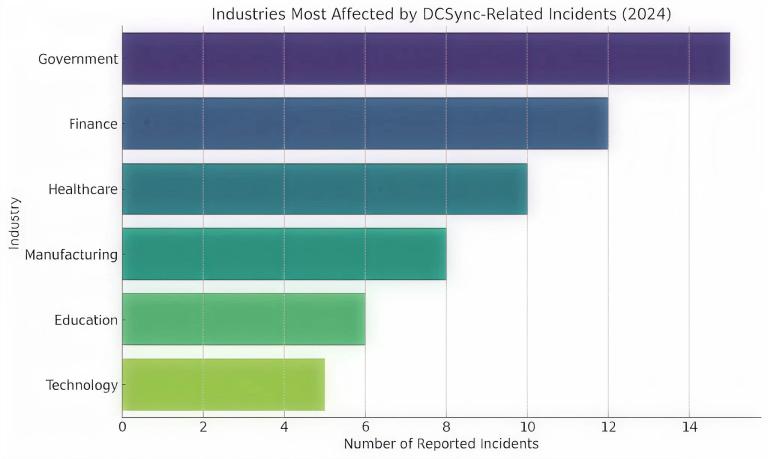
The bar chart above highlights the most impacted industries:
- Government and Finance top the list, reflecting their high-value data and commonly complex AD environments.
- Healthcare and Manufacturing also face notable exposure, likely due to legacy systems and limited segmentation.
- Education and Technology are increasingly targeted, often due to open networks and research IP value.
Timeline of DCSync-Related APT Incidents (2024)
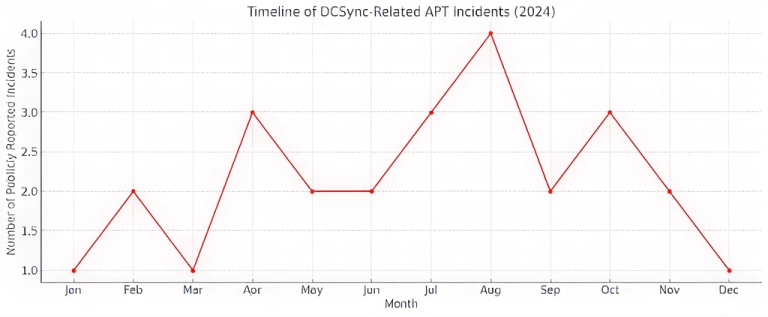
The line graph illustrates incident frequency throughout the year:
- Incident volumes rose notably in Q2 and Q3, with August (4 incidents) being the peak.
- Spikes in April, July, and October align with periods of known APT campaigns involving privilege escalation exploits (for example, legacy vulnerabilities like Zerologon).
- This seasonal pattern suggests strategic targeting during budget cycles or geopolitical events.
Final Thoughts
DCSync attacks remain a formidable threat to Active Directory environments. Adversaries impersonate domain controllers and extract sensitive credentials without deploying malware or accessing domain controllers directly. By exploiting legitimate replication protocols, attackers can stealthily harvest password hashes, facilitating lateral movement, privilege escalation, and persistent access. To mitigate these risks, organizations must rigorously audit replication permissions, enforce the principle of least privilege, and implement continuous monitoring for anomalous replication activities.
FAQs
Share on
View related cybersecurity attacks
Abusing Entra ID Application Permissions – How It Works and Defense Strategies
AdminSDHolder Modification – How It Works and Defense Strategies
AS-REP Roasting Attack - How It Works and Defense Strategies
Hafnium Attack - How It Works and Defense Strategies
Kerberoasting Attack – How It Works and Defense Strategies
Golden SAML Attack
Understanding Golden Ticket Attacks
Group Managed Service Accounts Attack
DCShadow Attack – How It Works, Real-World Examples & Defense Strategies
ChatGPT Prompt Injection: Understanding Risks, Examples & Prevention
NTDS.dit Password Extraction Attack
Pass the Hash Attack
Pass-the-Ticket Attack Explained: Risks, Examples & Defense Strategies
Password Spraying Attack
Plaintext Password Extraction Attack
Zerologon Vulnerability Explained: Risks, Exploits and Mitigation
Active Directory Ransomware Attacks
Unlocking Active Directory with the Skeleton Key Attack
Lateral Movement: What Is It, How It Works And Preventions
Man-in-the-Middle (MITM) Attacks: What They Are & How to Prevent Them
Why Is PowerShell So Popular for Attackers?
4 Service Account Attacks and How to Protect Against Them
How to Prevent Malware Attacks from Impacting Your Business
What is Credential Stuffing?
Compromising SQL Server with PowerUpSQL
What Are Mousejacking Attacks, and How to Defend Against Them
Stealing Credentials with a Security Support Provider (SSP)
Rainbow Table Attacks: How They Work and How to Defend Against Them
A Comprehensive Look into Password Attacks and How to Stop Them
LDAP Reconnaissance
Bypassing MFA with the Pass-the-Cookie Attack
Silver Ticket Attack
