Privileged Access Management (PAM)
Shrink your attack surface with Zero Standing Privilege. Our PAM solution provides just-in-time access, session monitoring, and post-session cleanup.
Read their Stories
Trusted by




































































Attackers are logging in, not just breaking in. Without visibility and control, blind spots become breaches.
Too many unmanaged accounts
Permanent admin rights give attackers easy targets to exploit.
Service accounts create hidden risk
Unmanaged service and task accounts hold powerful credentials attackers can exploit.
No visibility into privileged activity
Without monitoring, risky behavior and policy violations go unnoticed.
Remote access remains risky
VPNs and ad hoc connections are hard to secure or audit.
Use cases
Go beyond privilege with PAM solutions
Zero Standing Privilege
Replace standing admin accounts with just-in-time access that ends automatically.
Continuous discovery and cleanup
Find hidden accounts, remove excess rights, and reduce your attack surface with always-on PAM solutions.
Session monitoring and audit readiness
Record every privileged action and generate clear audit trails for compliance.
Third-party vendor access
Grant temporary privileged access to contractors and vendors with time-limited permissions. Monitor external user sessions and automatically revoke access.
Break-glass emergency access
Enable emergency privileged access during critical incidents with full audit trails. Provide immediate system access while maintaining security accountability.
Shared account elimination
Replace shared administrative accounts with individual privileged access credentials. Track all activities back to specific users for complete accountability.
The Netwrix approach
Privileged access management made practical
Get in touch
Let’s talk security
Netwrix PAM solutions put you in control of privileged access
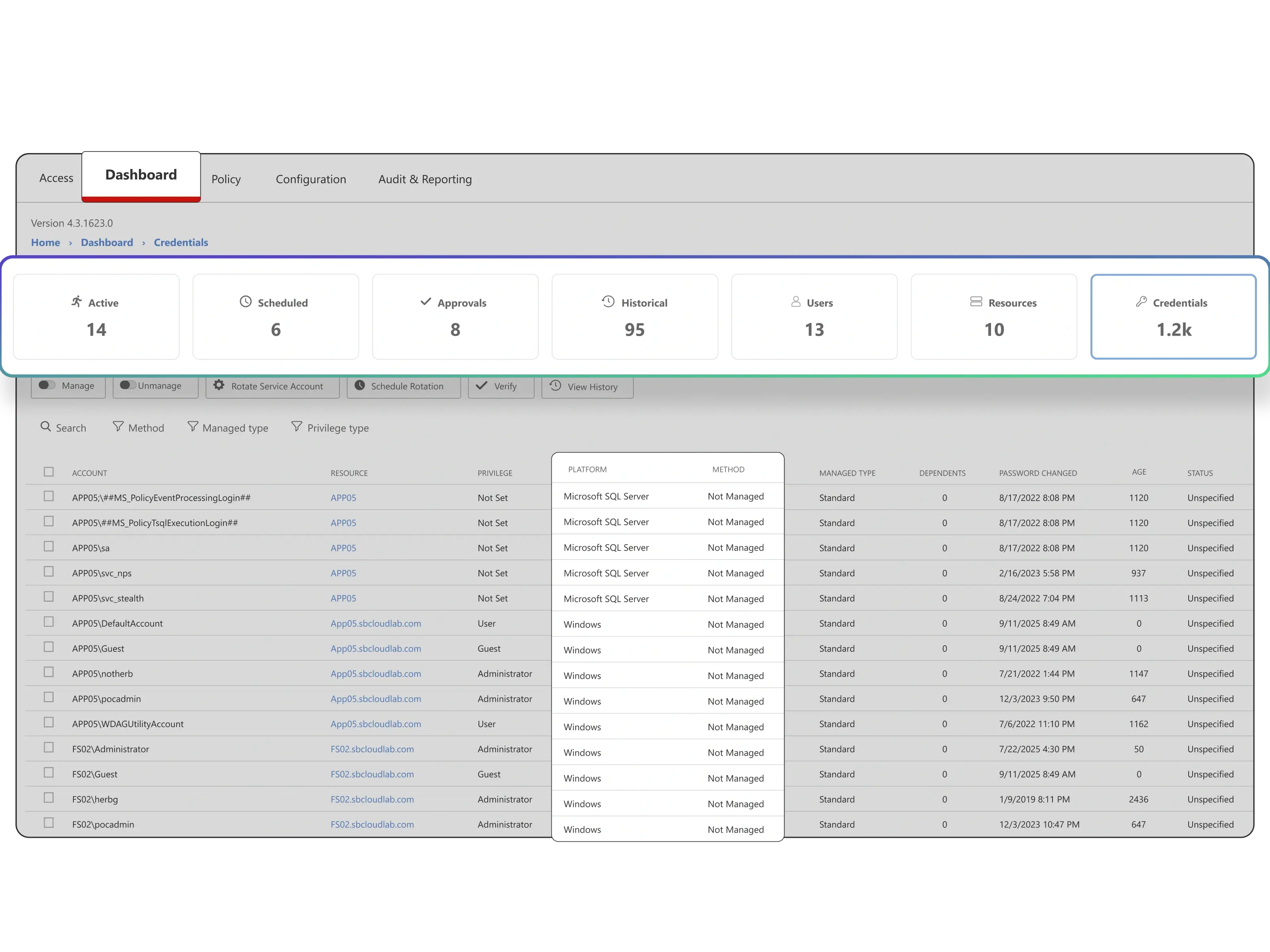
Privilege sprawl creates hidden risks and takes too much time to manage manually. The Netwrix Privileged Access Management solution addresses these challenges with Zero Standing Privilege by design, continuous discovery, automated least privilege enforcement, and full session monitoring. The result is less risk, easier audits, and stronger compliance without added complexity.

Zero Standing Privileges
Replace standing admin rights with just-in-time access that is removed when the session ends.
Session monitoring and control
See privileged activity as it happens, record every session, and stop suspicious behavior immediately.
Continuous discovery of privileged accounts
Automatically identify and remove hidden or unnecessary accounts before they can be exploited.
Secure remote access without VPNs
Enable safe, auditable access to critical systems from anywhere with MFA and full session logging.
Privileged Access Management (PAM) FAQs
Have questions? We’ve got answers.
See PAM in action