Netwrix Threat Manager: Threat Detection Software
Stop sophisticated breaches and hidden attackers with intelligent threat detection software powered by machine learning.
Read their Stories
Trusted by




































































Threat detection software that defends in real-time
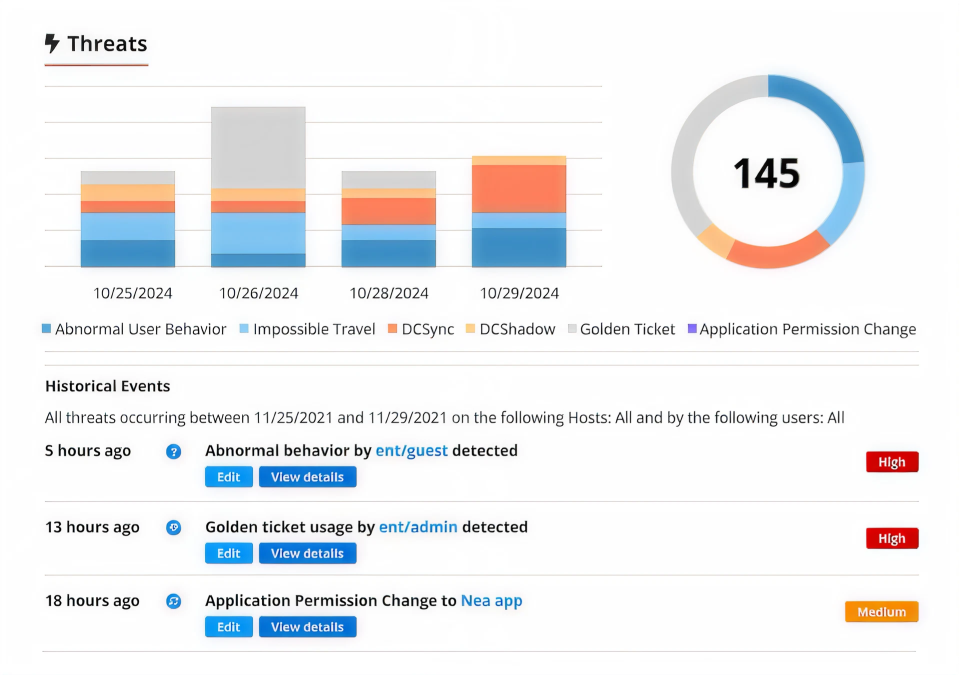
Detect attackers across platforms
Use real-time threat detection across AD, Entra ID, and file systems to stop ransomware, identity attacks, and insider threats before they escalate.
Investigate faster
Our advanced threat detection tool correlates events into clear attack chains to accelerate incident investigations and shorten response time.
Respond automatically
Our threat detection solution proactively blocks threats and can automatically trigger response actions to contain malicious activity on the fly.
Outsmart insider threats
Insider threat detection software uses behavior analytics to flag anomalies and detect compromised or malicious users that traditional tools often miss.
Capabilities
Detect and respond to attacks across AD, Entra ID and file systems with our complete threat detection tool
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.
Trusted by professionals
Don’t just take our word for it







