Identity Governance and Administration (IGA) Solution
that Works for You
Ensure the right users have access to the right things at the right time.
Enhance security and accountability by ensuring only the right people or machines have access to the appropriate resources at the correct time and for the intended reasons.
Minimize security risks by limiting access to sensitive data
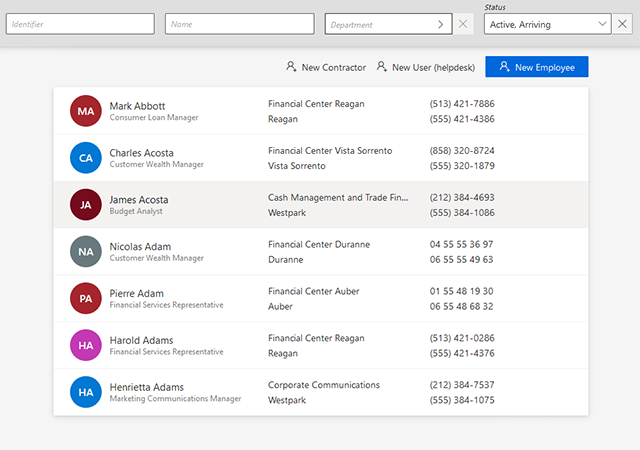
Access management often prioritizes technical user accounts over identities, sidelining valuable input from business users and burdening support. Empower business users to contribute to access management and governance, alleviating the workload of IT teams.
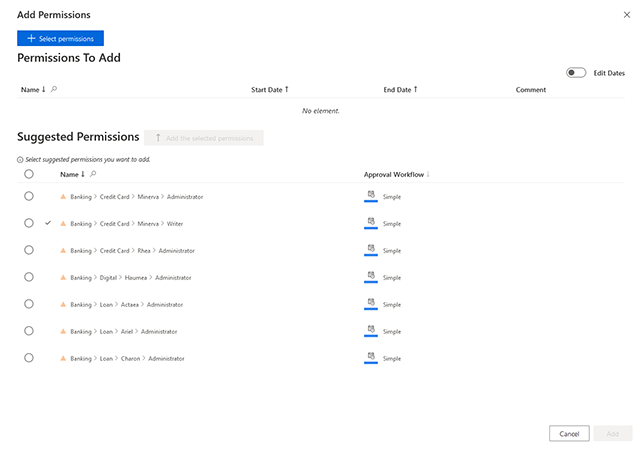
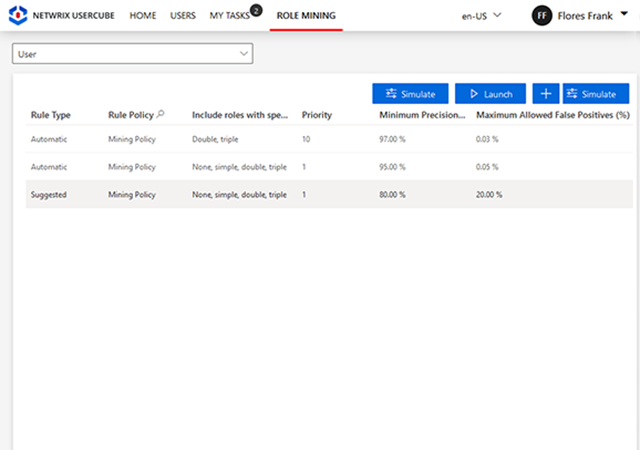
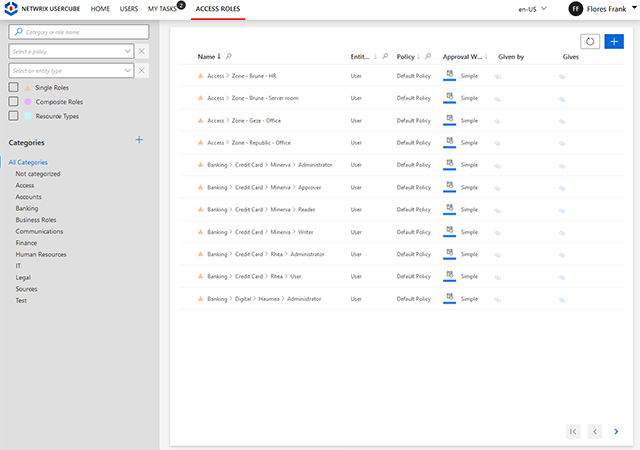
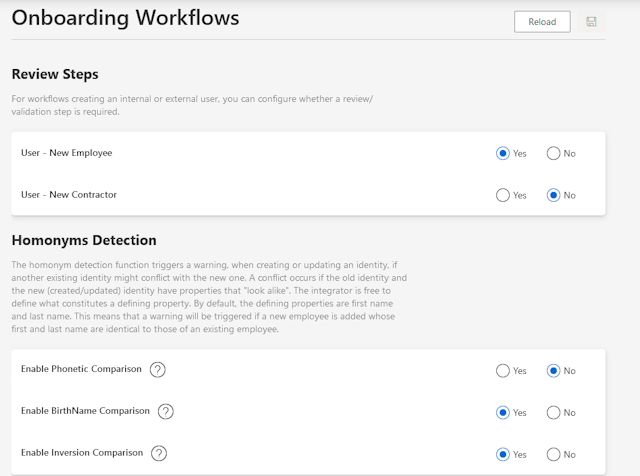
Enable granular policy implementation across diverse systems with customizable roles.
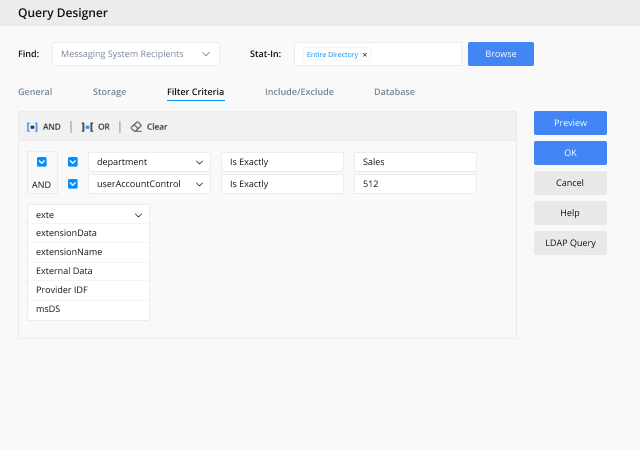
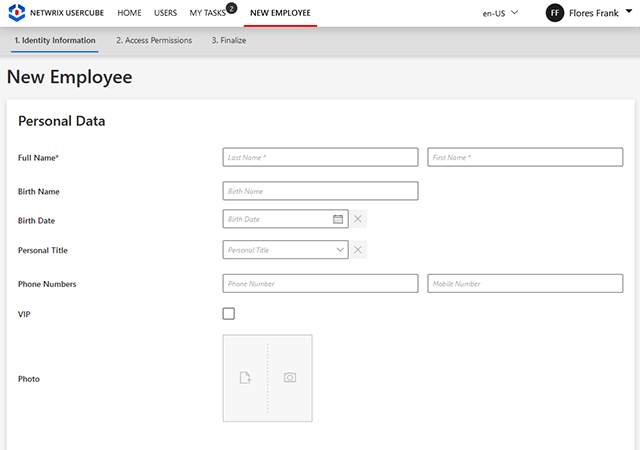
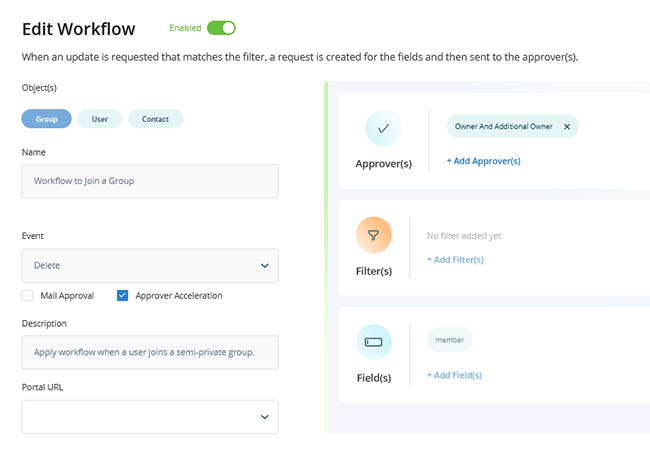
Implement robust policies with customizable roles in your identity management system. These roles, whether business or technical, offer granular control over capabilities and policy enforcement, while also enabling delegated control over objects from various systems.
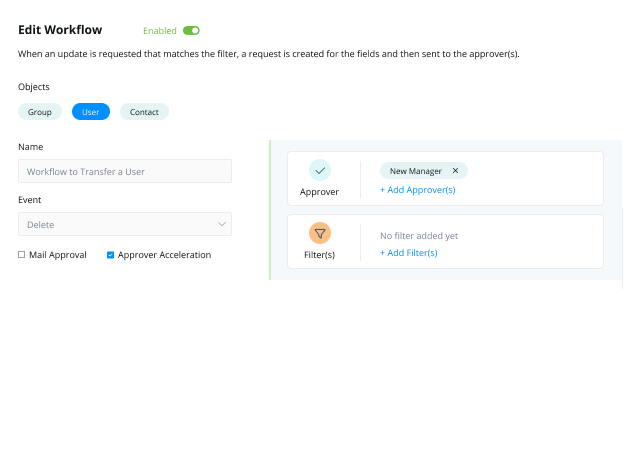
Build workflows that incorporate automated, human, and auditable processes.
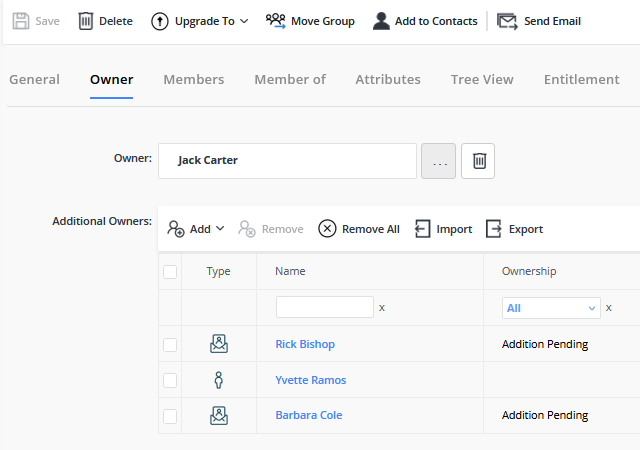
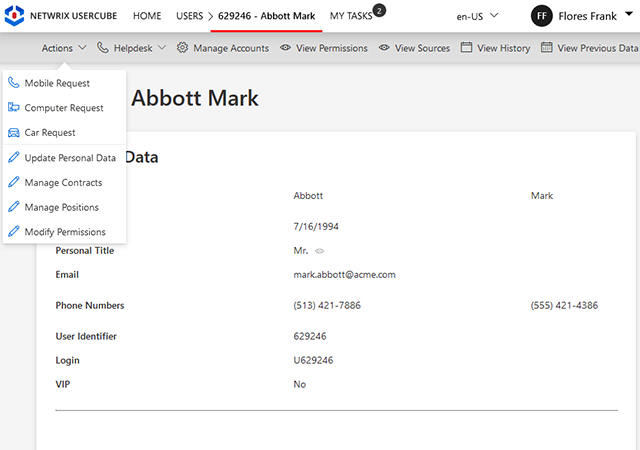
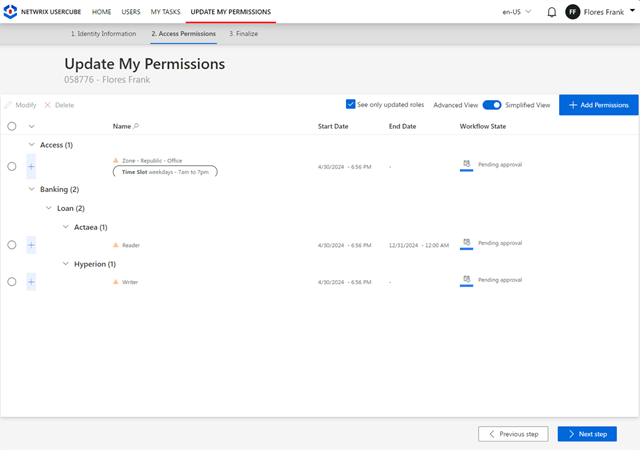
Empower users and their managers to request access through a self-service interface, sending requests for approval to relevant application owners or security officers. Streamline group management by allowing users to join or leave groups based on their roles, with oversight from business stakeholders.
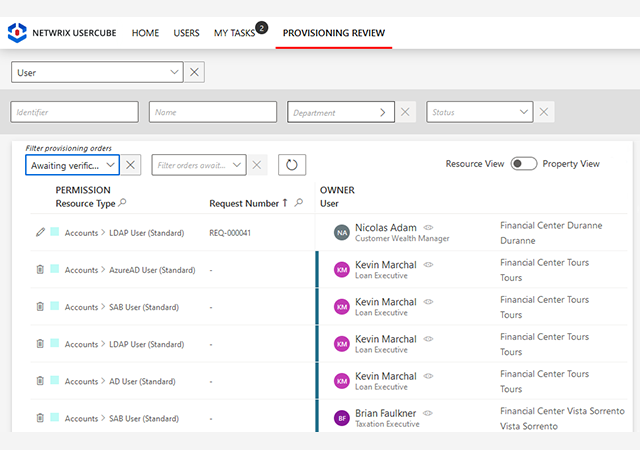
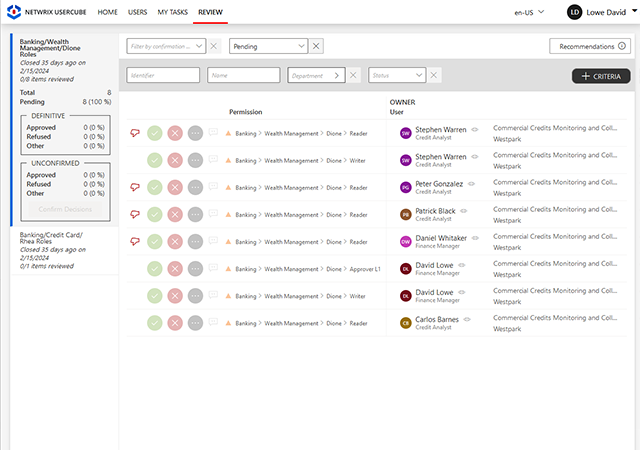
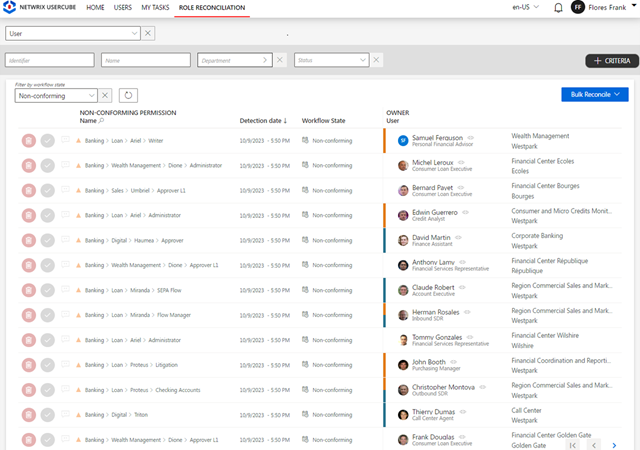
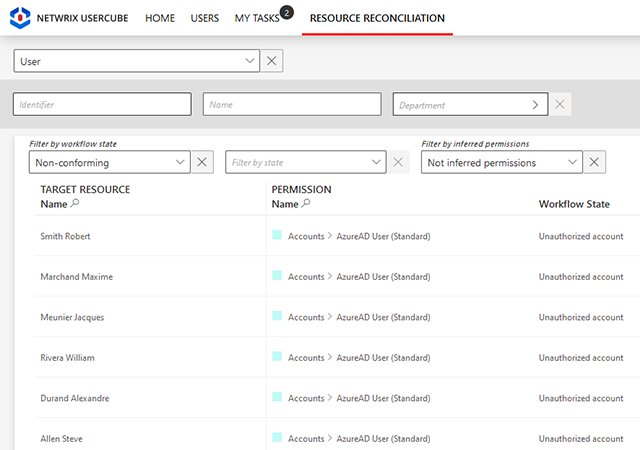
Thrill your auditors with automated attestation campaigns and compliance reports.
Maintain oversight of your identity governance and easily get the supporting data you need to prove compliance with an extensive set of customizable reports and an interactive requester to answer any question from an auditor.


_2.png)
_edit.png)