Find out which FISMA and NIST cybersecurity provisions you can address with Netwrix
The Federal Information Security Management Act (FISMA) defines a framework for ensuring the effectiveness of security controls over information and information systems that support federal operations. To achieve FISMA compliance, all federal agencies and organizations working on behalf of U.S. federal government agencies must meet the minimum security requirements defined in the security standard called FIPS 200.
The National Institute of Standards and Technology (NIST) issues standards, guidelines and other publications to assist these federal agencies and other organizations in achieving and maintaining FISMA compliance. In particular, NIST SP 800-53 provides information security controls that fully support FIPS 200 and enable organizations to meet FISMA information security requirements. FISMA compliance software from Netwrix helps you implement and validate the following NIST SP 800-53 security controls:
The National Institute of Standards and Technology (NIST) issues standards, guidelines and other publications to assist these federal agencies and other organizations in achieving and maintaining FISMA compliance. In particular, NIST SP 800-53 provides information security controls that fully support FIPS 200 and enable organizations to meet FISMA information security requirements. FISMA compliance software from Netwrix helps you implement and validate the following NIST SP 800-53 security controls:
Family: Access Control (AC)
- AC-2; AC-3; AC-6; AC-7; AC-17; AC-18; AC-20
Family: Audit and Accountability (AU)
- AU-3; AU-4; AU-5; AU-6; AU-7; AU-8; AU-9; AU-11; AU-12; AU-14
Family: Configuration Management (CM)
- CM-2; CM-3; CM-5; CM-6; CM-11
Family: Identification and Authentication
- IA-2; IA-3; IA-4; IA-5
Family: Incident Response (IR)
- IR-4; IR-5; IR-9
Family: Personnel Security (PS)
- PS-4; PS-5
Family: Risk Assessment (RA)
- RA-2; RA-3
Family: System and Information Integrity (SI)
- SI-4; SI-12

Learn more about how Netwrix can help you implement NIST SP 800-53 security controls and achieve FISMA compliance.
Depending on the configuration of your IT systems, your internal procedures, the nature of your business and other factors, Netwrix might also facilitate implementation of NIST SP 800-53 controls not listed above.
See exactly how Netwrix solutions support requirements of FISMA compliance
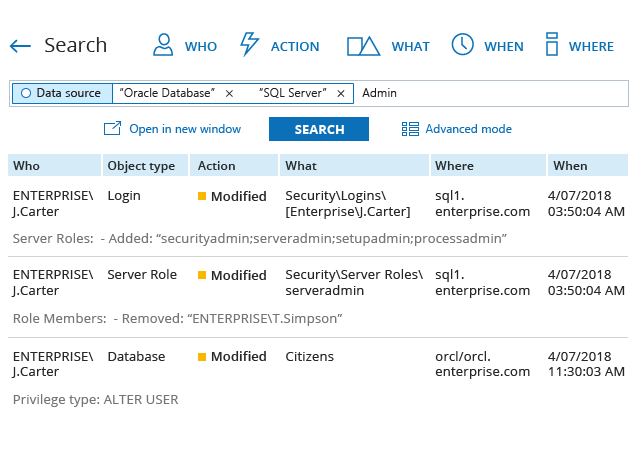
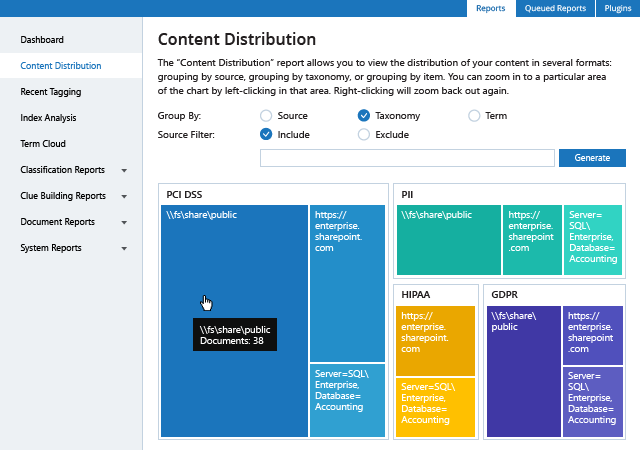
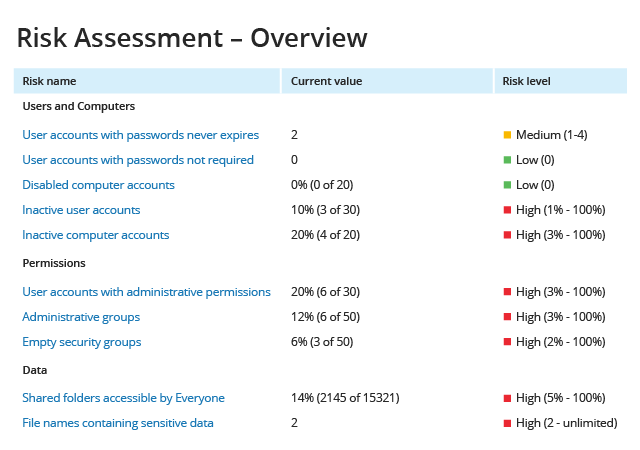
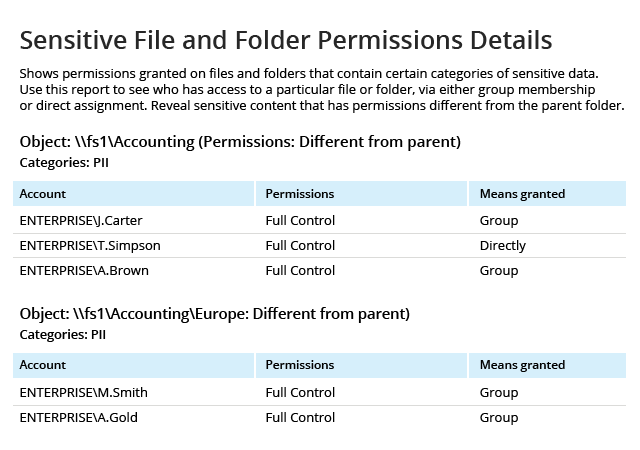
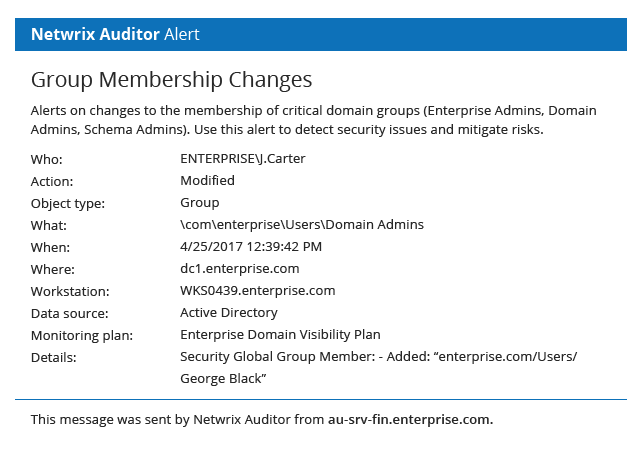
Netwrix delivers the enterprise-wide visibility into changes, configurations and access events in hybrid IT environments you need to enforce information security controls across your on-premises and cloud-based information systems. Unlike some other FISMA compliance solutions on the market, it provides security intelligence to help you identify security holes, detect anomalies in user behavior and investigate threat patterns before they turn into breaches, and also includes data discovery and classification functionality to further harden your data security management processes.