Address Privacy & Security Challenges with HIPAA Compliance Software
The Health Insurance Portability and Accountability Act (HIPAA) establishes U.S. national standards for protecting the security of individually identifiable electronic health information. The requirements apply to healthcare providers, health information organizations, and other covered entities and business associates that store, transmit or manage protected health information. HIPAA security software can help you address the law’s provisions concerning the privacy and security of electronic protected health information, such as the rights of individuals to access or amend their protected health information; HIPAA security rules covering administrative and technical safeguards; requirements for policies and procedures; and documentation requirements. HIPAA compliance software from Netwrix can help you establish and maintain data security controls aligned with the following HIPAA privacy requirements:
Part 164: Security and Privacy
Subpart C: Security Standards for the Protection of Electronic Protected Health Information
- § 164.308: Administrative safeguards
- § 164.312: Technical safeguards
- § 164.316: Policies and procedures and documentation requirements
Subpart D: Notification in the Case of Breach of Unsecured Protected Health Information
- § 164.404: Notification to individuals
- § 164.410: Notification by a business associate
Subpart E: Privacy of Individually Identifiable Health Information
- § 164.524: Access of individuals to protected health information
- § 164.526: Amendment of protected health information
- § 164.528: Accounting of disclosures of protected health information

Learn more about how
Netwrix can help you achieve
compliance with HIPAA requirements.
Netwrix can help you achieve
compliance with HIPAA requirements.
Depending on the configuration of your IT systems, your internal procedures, the nature of your business and other factors, Netwrix might also facilitate compliance with provisions of the HIPAA not listed above.
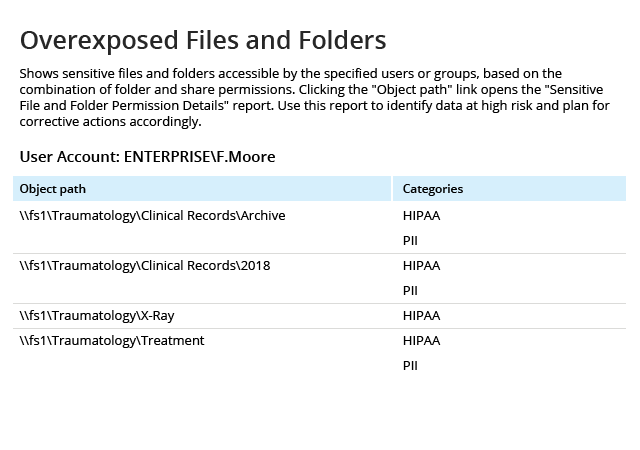
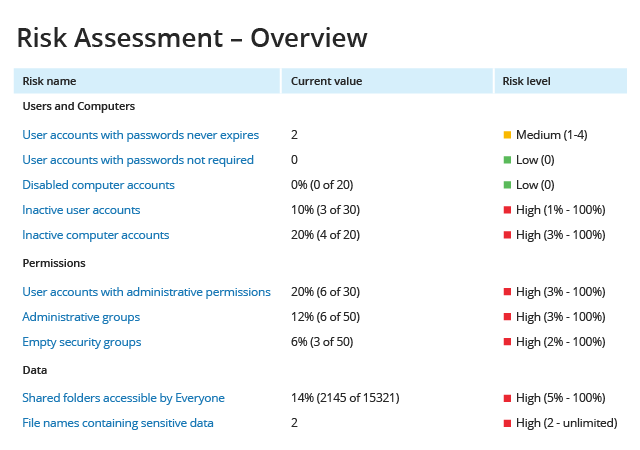
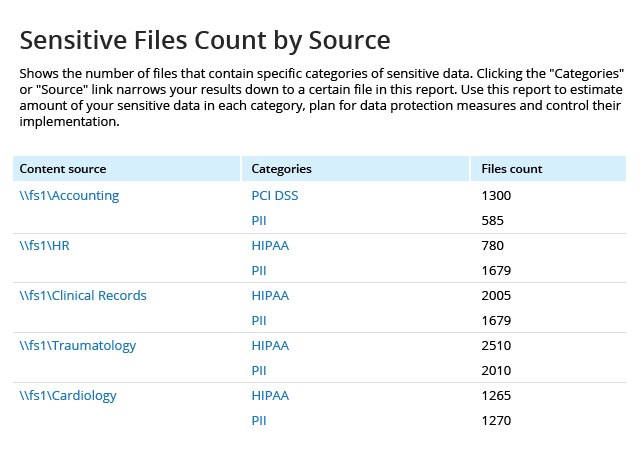
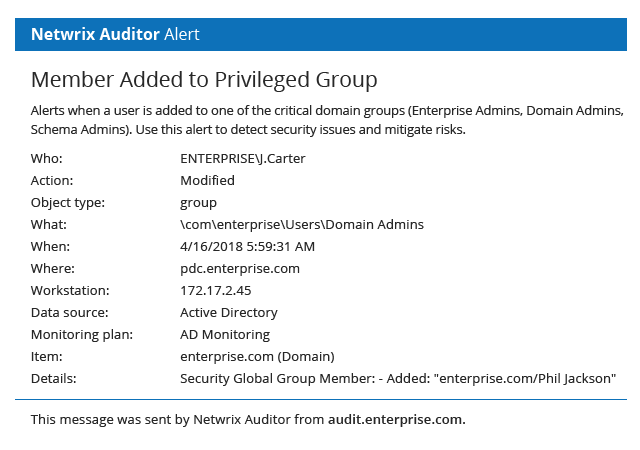
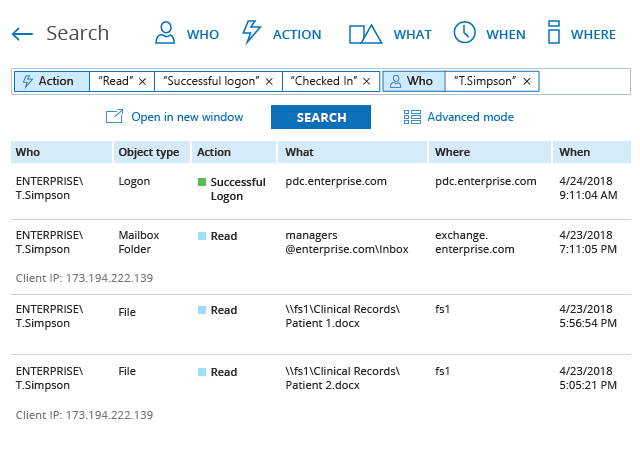
HIPAA Compliance Software Helps Satisfy Audit & Data Protection Standards
Netwrix solutions provide complete visibility into on-premises and cloud-based systems and applications to enable control over user actions and improve data security. This HIPAA compliance software delivers security features that empower you to conduct HIPAA risk assessments, detect anomalies in user behavior, and investigate threat patterns before they turn into security incidents or disrupt business services. Unlike many other HIPAA audit software solutions, Netwrix provides out-of-the-box compliance reports mapped to specific requirements of HIPAA and many other common regulations, reducing the time and effort required for the compliance preparation process.