Find out which specific PCI DSS requirements you can address with Netwrix
PCI DSS security standard is designed to protect cardholder data by requiring organizations to have an appropriate combination of policies, procedures, technical measures, administrative efforts and physical security. Netwrix solutions help you achieve and maintain compliance with PCI DSS requirements by delivering enterprise-wide visibility into your on-premises and cloud-based applications and systems, as well as deep insight into your sensitive data. In addition to helping you establish the security controls required to protect cardholder data, this PCI DSS compliance software enables you to provide evidence that those security controls are aligned with the following requirements:
Requirement 3: Protect stored cardholder data
- 3.1; 3.2; 3.3
Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs
- 5.1
Requirement 6: Develop and maintain secure systems and applications
- 6.3.1; 6.4.2
Requirement 7: Restrict access to cardholder data by business need to know
- 7.1; 7.1.2; 7.2; 7.2.2
Requirement 8: Identify and authenticate access to system components
- 8.1.1; 8.1.2; 8.1.3; 8.1.4; 8.1.6; 8.2.2; 8.2.3; 8.2.4; 8.2.5; 8.2.6; 8.5
Requirement 10: Track and monitor all access to network resources and cardholder data
- 10.1; 10.2.1; 10.2.2; 10.2.4; 10.2.5; 10.3; 10.5; 10.6.1; 10.6.2; 10.7; 10.8
Requirement 11: Regularly test security systems and processes
- 11.5

Learn more about how
Netwrix can help you pass
PCI DSS compliance audits.
Netwrix can help you pass
PCI DSS compliance audits.
Depending on the configuration of your IT systems, your internal procedures, the nature of your business and other factors, Netwrix Auditor might also facilitate compliance with provisions of the PCI DSS not listed above.
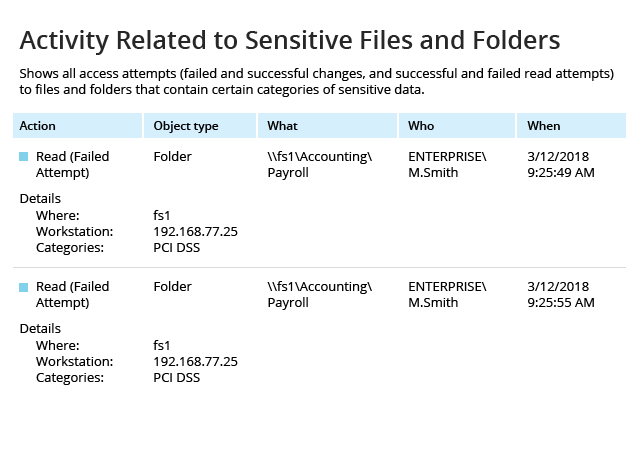
See exactly how Netwrix solutions help ensure PCI DSS compliance
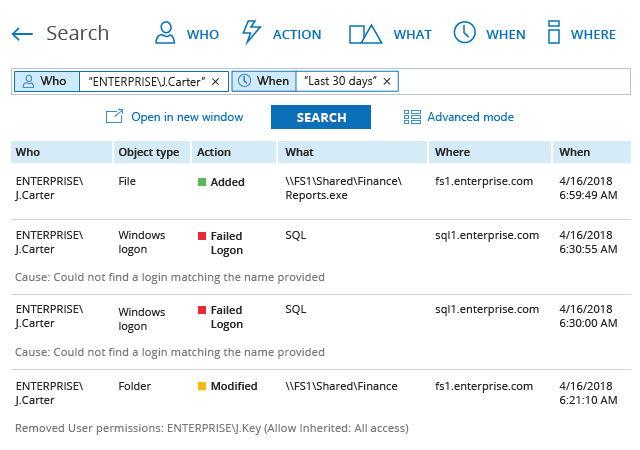
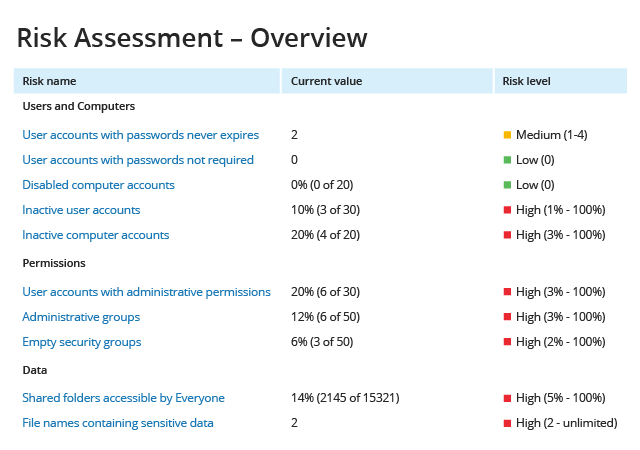
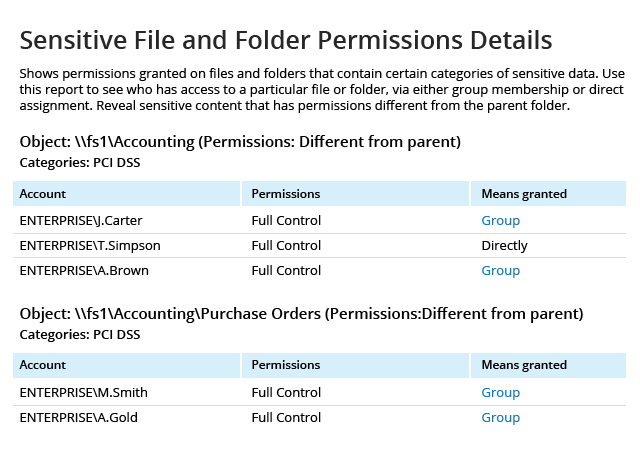
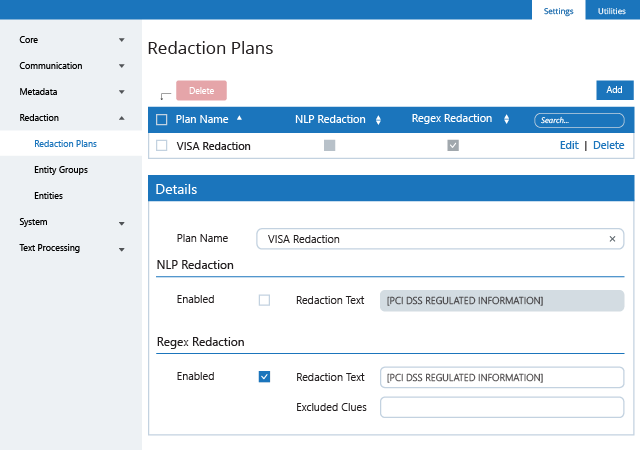
Unlike many fragmented PCI DSS compliance tools on the market, Netwrix provides visibility into hybrid IT environments that organizations need to meet the requirements of the PCI DSS compliance standard, as well as maintain a policy that addresses information security issues, including both insider threats and external attacks. This PCI DSS compliance software enables control over critical changes, configurations and access events. It also provides security intelligence that helps you identify security holes, detect anomalies in user behavior and investigate threat patterns in time to prevent real damage. Finally, it includes out-of-the box compliance reports already mapped to specific requirements of many common compliance standards, including PCI DSS.