Introducing Netwrix Auditor 9.96
Level up your database and virtual security
See through the complex set of SQL Server permissions so you can
mitigate the risk of insider misuse and limit the damage a compromised
account can do.
Enforce the least-privilege model and respond to the most critical
security incidents first to increase the resilience of your virtual environment.
Harden the security posture of your entire virtual infrastructure
by quickly detecting and responding to suspicious activity in your Nutanix AHV.
Skip reading and play the game?
Play an interactive game that walks you through the main features of
Netwrix Auditor 9.96 and see how good you are at securing your IT environment.
Gain visibility into sql server permissions
Close security gaps across your databases
Securing databases is hard because the complicated server-level
and database-level permissions leave you unable to tell whether data is at risk
and who has excessive permissions to sensitive data, which could result in data
leaks and compliance nightmares. With Netwrix Auditor, you can find your way to
staying out of the security breach spotlight
Should all these users have access to the database that contains customer information?
Do Sophie’s job responsibilities require her to have access to the production database?
Do Sophie’s job responsibilities require her to have access to the production database?
As a helpdesk administrator, Sophie can connect to the database. However, only
a database administrator is supposed to have permissions to the entire SQL Server instance.
You should revoke these permissions from her account immediately.


Should all these users have access to the database that contains customer information?
Mike and Katie are from the Customer Support team, so they need at least
“View” permissions to do their job. It's not clear why Jessica, a web designer, is on this list.
You should contact her manager to help you figure it out.
Do Sophie’s job responsibilities require her to have access to the production database?
As a helpdesk administrator, Sophie can connect to the database. However, only
a database administrator is supposed to have permissions to the entire SQL Server instance.
You should revoke these permissions from her account immediately.


Should all these users have access to the database that contains customer information?
Mike and Katie are from the Customer Support team, so they need at least
“View” permissions to do their job. It's not clear why Jessica, a web designer, is on this list.
You should contact her manager to help you figure it out.


Do Sophie’s job responsibilities require her to have access to the production database?
As a helpdesk administrator, Sophie can connect to the database. However, only
a database administrator is supposed to have permissions to the entire SQL Server instance.
You should revoke these permissions from her account immediately.
Achieve more scrutiny over vmware
Don’t let attackers through your first line of defense
IT systems that run business-critical services or store valuable
information are often virtualized. Unfortunately, organizations often fail to pay
as much attention to the security of their virtualized environment as they do to
their physical servers. Malicious actors are eager to exploit loose permissions
or make critical changes in order to gain access to your virtualized systems and
steal your sensitive data.
Keep VMware access under control
Spot accounts that have access rights beyond what they need, such as QA or
DevOps team members who no longer use the virtual environment. Using this information, you
can enforce the least-privilege principle and close security gaps before an image of a critical
virtual machine gets stolen and your data breach nightmare becomes real.
Report the severity of a breach
Quickly see exactly which ESXi hosts or specific virtual machines a malicious
insider or a compromised account had access to. Use this information to determine whether you need
to report the incident and, if necessary, notify all affected parties or take other
appropriate steps.
Focus on high-risk incidents first
Keep an eye on the most important modifications, as detailed in vSphere’s own
Security Hardening Guide for vSphere,
such as changes to host profiles, the Managed Object Browser or account unlock time. This way,
you can easily prioritize investigation of critical security incidents.
Focus on high-risk incidents first
Keep an eye on the most important modifications, as detailed in vSphere’s own
Security Hardening Guide for vSphere,
such as changes to host profiles, the Managed Object Browser or account unlock time. This way,
you can easily prioritize investigation of critical security incidents.

Keep VMware access under control
Spot accounts that have access rights beyond what they need, such as QA or
DevOps team members who no longer use the virtual environment. Using this information, you
can enforce the least-privilege principle and close security gaps before an image of a critical
virtual machine gets stolen and your data breach nightmare becomes real.
Report the severity of a breach
Quickly see exactly which ESXi hosts or specific virtual machines a malicious
insider or a compromised account had access to. Use this information to determine whether you need
to report the incident and, if necessary, notify all affected parties or take other
appropriate steps.

Focus on high-risk incidents first
Keep an eye on the most important modifications, as detailed in vSphere’s own
Security Hardening Guide for vSphere,
such as changes to host profiles, the Managed Object Browser or account unlock time. This way,
you can easily prioritize investigation of critical security incidents.

Keep VMware access under control
Spot accounts that have access rights beyond what they need, such as QA or
DevOps team members who no longer use the virtual environment. Using this information, you
can enforce the least-privilege principle and close security gaps before an image of a critical
virtual machine gets stolen and your data breach nightmare becomes real.

Report the severity of a breach
Quickly see exactly which ESXi hosts or specific virtual machines a malicious
insider or a compromised account had access to. Use this information to determine whether you need
to report the incident and, if necessary, notify all affected parties or take other
appropriate steps.

Focus on high-risk incidents first
Keep an eye on the most important modifications, as detailed in vSphere’s own
Security Hardening Guide for vSphere,
such as changes to host profiles, the Managed Object Browser or account unlock time. This way,
you can easily prioritize investigation of critical security incidents.
Expand netwrix auditor to nutanix ahv
Increase the resilience of your virtual environment
It’s important to stay on top of any suspicious activity in your
virtual environment, regardless of which virtualization vendors you rely on. With
Netwrix Auditor Add-on for Nutanix AHV, you can take advantage of one of the most
modern virtual infrastructures while keeping your IT auditing
top notch.
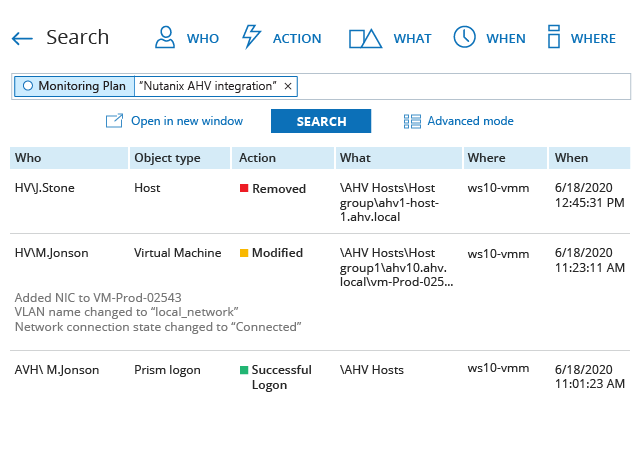
Watch privileged users closely
Ensure that privileged users are following internal policies and don’t misuse their
elevated permissions by auditing each action across your Nutanix AHV environment.
Detect security incidents faster
Promptly detect suspicious logons to Prism and other actions that could undermine
security, such as changes to user roles and hardware configurations, and investigate quickly so you
can respond before a critical virtual machine gets stolen and you suffer a data breach.
Detect security incidents faster
Promptly detect suspicious logons to Prism and other actions that could undermine
security, such as changes to user roles and hardware configurations, and investigate quickly so you
can respond before a critical virtual machine gets stolen and you suffer a data breach.

Watch privileged users closely
Ensure that privileged users are following internal policies and don’t misuse their
elevated permissions by auditing each action across your Nutanix AHV environment.
Detect security incidents faster
Promptly detect suspicious logons to Prism and other actions that could undermine
security, such as changes to user roles and hardware configurations, and investigate quickly so you
can respond before a critical virtual machine gets stolen and you suffer a data breach.

Watch privileged users closely
Ensure that privileged users are following internal policies and don’t misuse their
elevated permissions by auditing each action across your Nutanix AHV environment.

Detect security incidents faster
Promptly detect suspicious logons to Prism and other actions that could undermine
security, such as changes to user roles and hardware configurations, and investigate quickly so you
can respond before a critical virtual machine gets stolen and you suffer a data breach.
Let’s play the game
Don’t let attacker breach your company
Choose the action you’d take to stop an attacker
You
Attacker
Round 1
You’ve successfully mitigated the risk of a data breach!
Now make it happen in real life with Netwrix Auditor 9.96
1
Regularly ensure that no one except the HR and management teams has
access to the database containing employees’ personal records
Exactly! It’s important to systematically ensure that employees have
access to only what they need. This way, you can limit the damage a malicious
insider or compromised account can do.
2
Verify that the QA team’s access is limited to specific database tables
and does not extend to the entire production database
Nice move! You don’t want one of your users to deliberately or accidentally
expose your critical database information.
1
Revoke the permissions of all DevOps engineers who no longer use the
virtual machine for testing
That’s right! Unfortunately, one engineer still had elevated privileges
to VMware vCenter and therefore had access to the corporate data stored on your
virtualized file server, which put your corporate data at risk!
2
Systematically validate that the access rights of VMware administrators
are in line with their job responsibilities
Impressive! You need to constantly review the permissions of privileged
users and ensure they are aligned with the least-privilege principle. But don’t
count on this best practice alone – one of your administrator accounts just
got hacked!
1
Check what information Attacker had access to in your
critical databases
Good job! Unfortunately, Attacker found his way to your sensitive data by
exploiting the loose permissions on the virtual machine that runs your database.
2
See whether Attacker had permissions to the virtual machine your database
runs on
Great idea! Even though the database permissions are correct, VM access
rights may have blind spots that Attacker could use to gain access to your
sensitive data.
1
Monitor changes to the Account Unlock Time setting in
VMware vCenter
Good call! VMware recommends unlocking accounts automatically in 15
minutes. Changes that will unlock them sooner increase the risk of a successful
brute-force attack.
2
Receive notifications whenever the Managed Object Browser
(MOB) is enabled
Well done! The MOB should be disabled by default and used only for debugging
when a corresponding ticket has been opened. Otherwise, attackers can use this weak
spot to perform malicious configuration actions and get access to critical systems
that store your sensitive data.
1
Keep an eye on what a departing administrator is doing in the Nutanix
AHV environment
Smooth! Monitoring the activity of privileged users can help you ensure they
are following internal policies and don’t misuse their elevated permissions.
2
Set up alerts on critical Nutanix AHV activity, like hardware configuration
changes and logons to Prism outside of business hours
Correct! By quickly detecting suspicious activity, you can respond to security
incidents before a critical virtual machine gets compromised.
Done. Move to the next round
Learn about additional enhancements
in Netwrix Auditor 9.96 that improve usability, performance and stability.
What’s New in Netwrix Auditor 9.96
Join Our Live Webinar
September 16
10 AM PT / 1 PM ET
Meet the new Netwrix Auditor! In this webinar, our expert demonstrates how
the new capabilities in Netwrix Auditor 9.96 can help you strengthen the security of your databases,
virtual environments and more.

Attend for a Chance to Win GoPro HERO7 Black
Ready to get started?
Next Steps
