Identity Governance and Administration (IGA)
Automate provisioning, enforce least privilege, and maintain continuous audit readiness.
Read their Stories
Trusted by




































































Managing human and non-human identities across hybrid environments strains IT, creates governance gaps, and complicates compliance
Manual provisioning
Manual account creation and removal cause delays, errors, and security gaps during onboarding and offboarding.
Excessive privileges
Over-provisioned accounts and unchecked admin rights create risk and compliance challenges.
Orphaned accounts
Dormant and orphaned accounts remain active unnoticed, creating hidden entry points for attackers.
Fragmented systems
Disconnected identity systems reduce visibility and make it hard to enforce consistent access policies.
Use cases
Secure identities across your entire enterprise with a leading identity management tool
Automated lifecycle workflows
Automate identity processes from onboarding to offboarding with policy-based workflows. Reduce errors, cut delays, and ensure the right access at the right time.
Group lifecycle management
Automate group creation, updates, and access control to reduce manual work, prevent unnecessary access buildup, and keep directories organized.
Entitlement management
Control access entitlements across the organization so permissions align with roles and responsibilities, reducing unauthorized access and compliance risk.
Access request delegation
Automate and delegate access requests with self-service and approval workflows to reduce IT workload, lower errors, and speed up access delivery.
Access rights certification
Regularly review and certify user access rights to eliminate excessive permissions, reduce risk, and simplify audit preparation.
Risk detection and analysis
Continuously detect risks like conflicting entitlements, SoD violations, and dormant accounts. Apply policy-based controls to prevent escalation.
The Netwrix approach
Comprehensive identity management software built for today’s challenges
Get in touch
Let’s talk security
Secure the full identity lifecycle, from start to finish
The Netwrix Identity Management solution automates and secures every stage of the identity lifecycle across hybrid environments. Simplify onboarding and offboarding with policy-based workflows, manage groups and entitlements with RBAC and machine learning–based role mining, enforce strong password policies, and govern non-human identities (NHIs) alongside human accounts. Detect risks such as excessive permissions, SoD conflicts, and dormant accounts, while streamlining certifications and compliance reporting. The result: least privilege by default, reduced IT workload, and continuous audit readiness.

Faster deployment and lower TCO
Out-of-the-box automation and governance reduce implementation effort, speed time-to-value, and lower operating costs.
Flexible deployment options
Built for hybrid environments with broad integrations, so you can adopt at your own pace across on-premises and cloud systems.
Governance without complexity
Simplify compliance with built-in controls, certifications, password policy enforcement, and reporting that aligns with how your organization operates.
Continuous risk detection
Continuously detect excessive permissions, segregation of duties violations, and dormant accounts to stop risks before they escalate.
Identity Management FAQs
Have questions? We’ve got answers.
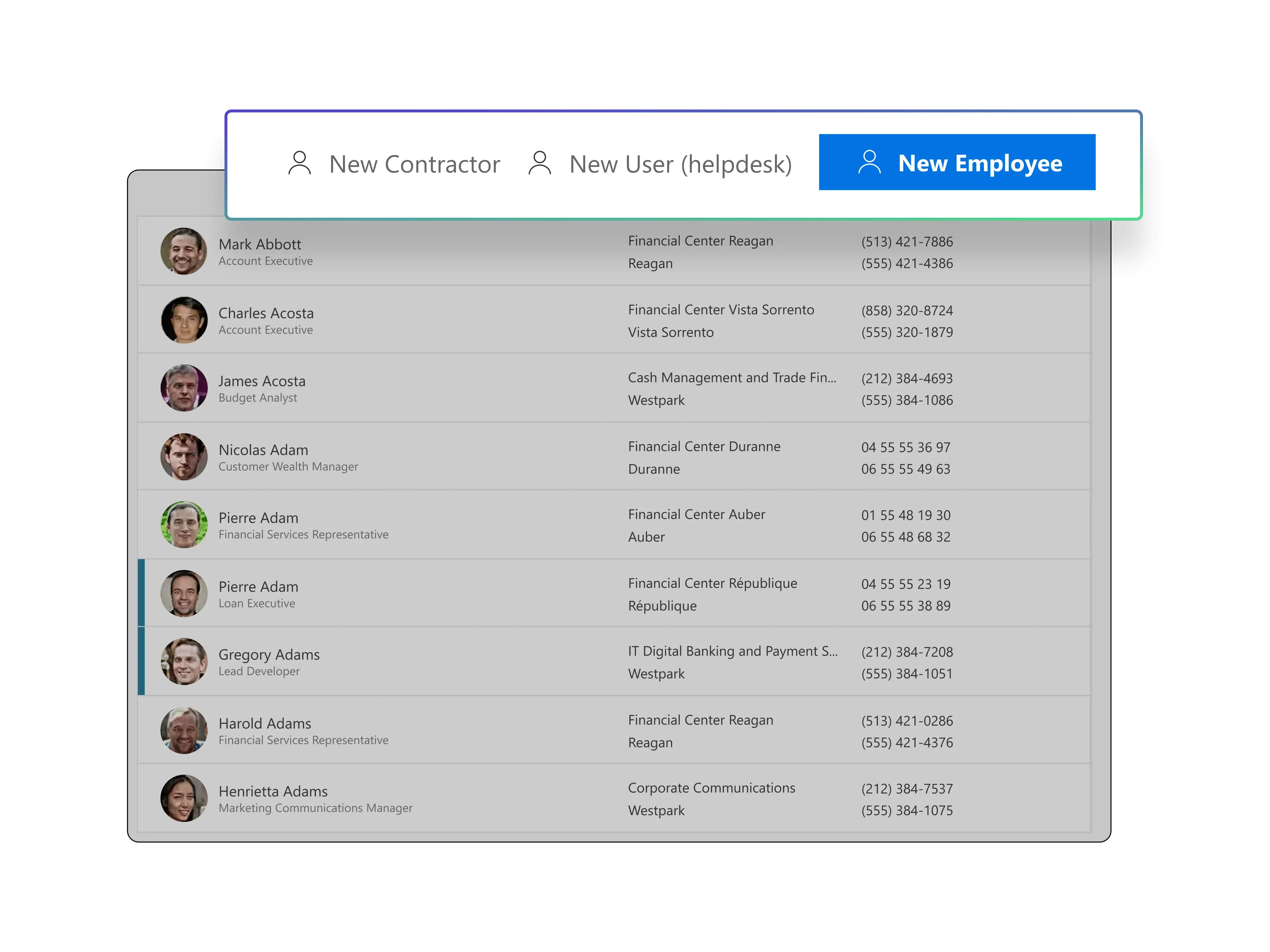
See Identity Management in action