Listing SQL Server roles for a user
- Start Microsoft SQL Server Management Studio (MSSMS).
- On the File menu, click Connect Object Explorer.
- In the Connect to Server dialog box, specify the following settings:
- In the Server type list box, select Database Engine.
- In the Server name text box, type the name of the SQL cluster server.
- In the Authentication list box, choose your SQL Server Authenticationmethod and specify the credentials to use. If you do not want to re-type the password whenever you connect to the server, tick Remember password.
- Click Connect.
- Click Execute (or hit the F5 key).
- Upon connection, click New Query and paste the following script into the query field:
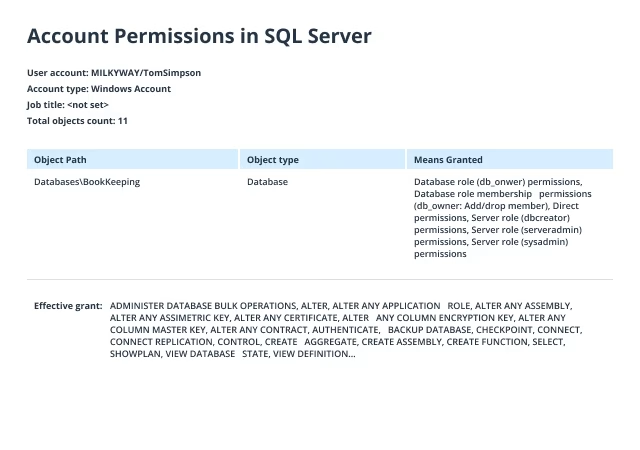
select r.name as Role, m.name as Principal
from
master.sys.server_role_members rm
inner join
master.sys.server_principals r on r.principal_id = rm.role_principal_id and r.type = 'R'
inner join
master.sys.server_principals m on m.principal_id = rm.member_principal_id
where m.name = 'MILKYWAY\TomSimpson'
- Review the list of server-level roles and principals (member names) in the query execution results:
Querying database roles in SQL Server for a user
- Start Microsoft SQL Server Management Studio (MSSMS).
- On the File menu, click Connect Object Explorer.
- In the Connect to Server dialog box, specify the following settings:
- In the Server type list box, selectDatabase Engine.
- In the Server name text box, type the name of the SQL cluster server.
- In the Authentication list box, choose your SQL Server Authentication method and specify the credentials to use. If you do not want to re-type the password whenever you connect to the server, tick Remember password.
- Click Connect.
- Click Execute (or hit the F5 key).
- Upon connection, select the Database you need to query for user roles.
- Click New Query and paste the following script into the query field:
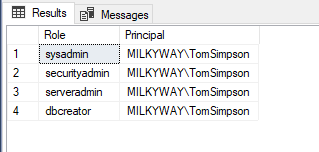
SELECT r.name role_principal_name, m.name AS member_principal_name
FROM sys.database_role_members rm
JOIN sys.database_principals r
ON rm.role_principal_id = r.principal_id
JOIN sys.database_principals m
ON rm.member_principal_id = m.principal_id
where m.name = 'MILKYWAY\TomSimpson'
- Review the list of server-level roles and principals (member names) in the query execution results:
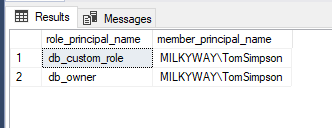
- Open Netwrix Auditor and navigate to Reports -> Predefined -> SQL Server - State-in-Time -> Account Permissions in SQL Server.
- Specify the following filters:
- In the User account filter, type the full user name (such as MILKYWAY/TomSimpson).
- In the Object type filter, choose Server Instance, Database.
- Click View to create a clear report on the effective permissions for the user.