Detect and Investigate Abnormal
User Behavior to Stop Attackers
in Their Tracks
Netwrix Auditor provides a consolidated view of all anomalous activity in your environment to
help you quickly spot malicious actors. And its rich security intelligence about user
behavior and security blind spots enables you to investigate incidents efficiently and confidently
determine the best response.
Launch In-Browser Demo
No need to deploy the product

Behavior Anomaly Discovery
Improve Detection of Threat Actors
to Protect
Your Critical Assets
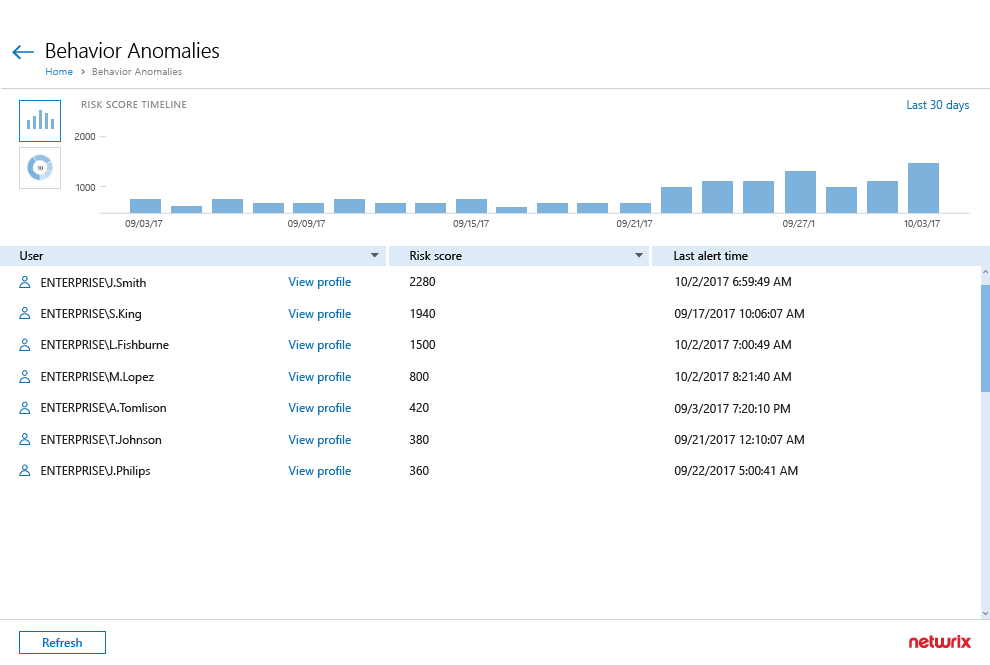
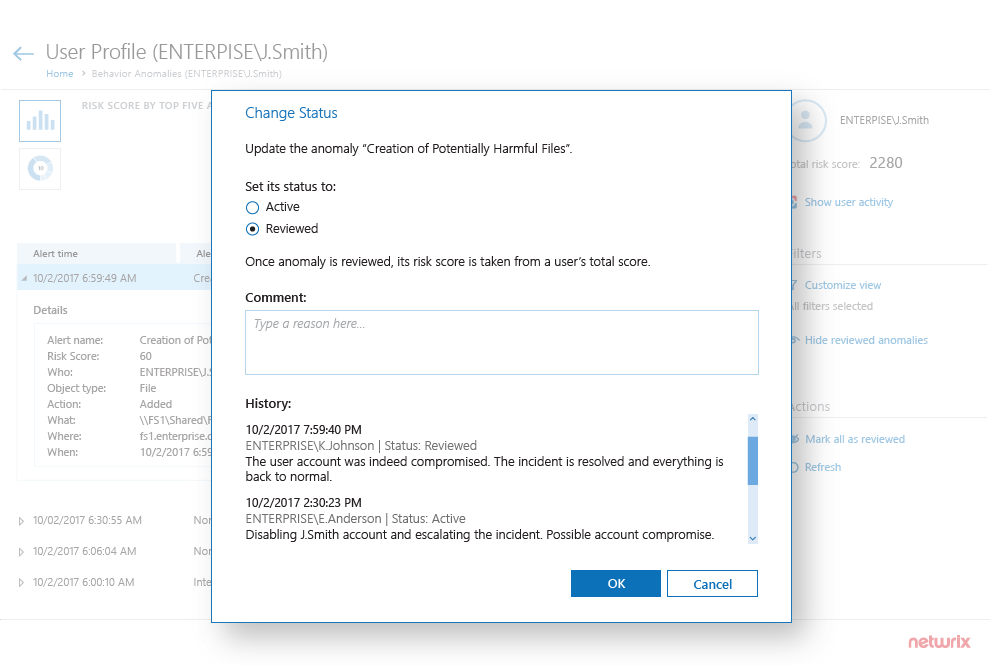
Identify high-risk user accounts on the prowl
Spot compromised accounts and malicious insiders by reviewing accumulated user risk scores.
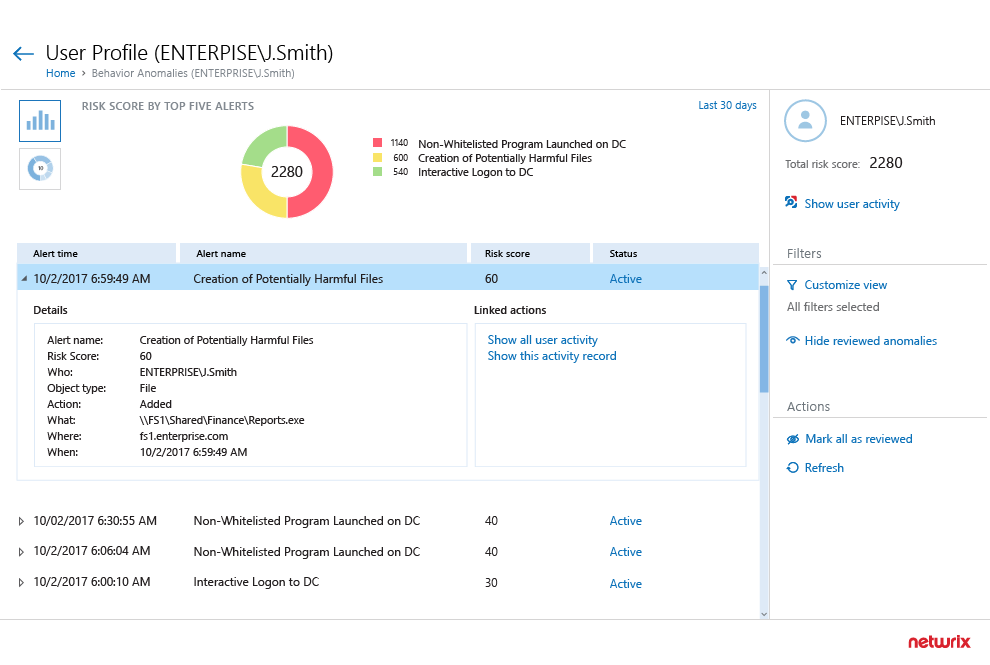
Triage all alerts triggered by a high-risk threat actor
Home in on a potentially malicious actor by examining all alerts triggered by a particular user.
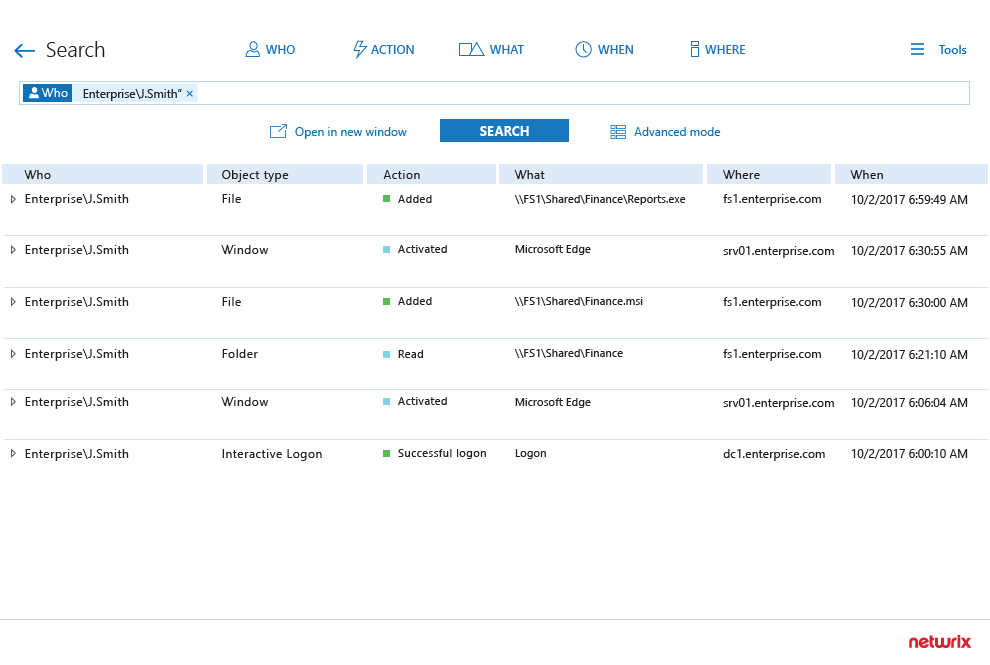
Initiate an in-depth investigation immediately
Dive into the context of the attack and analyze the complete history of the user’s actions.
Make more informed remediation decisions
Collaborate with other security specialists and determine the best response to each incident.
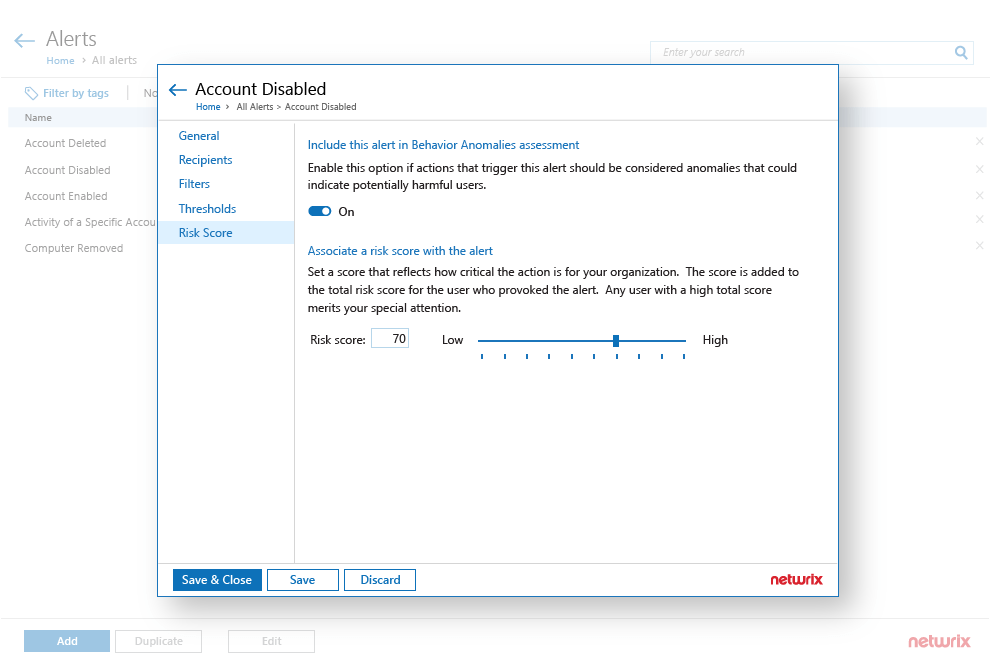
Focus on user activity that presents a real threat
Easily adjust your alerting and scoring settings to accommodate any legitimate behavior typical for your environment.
Identify high-risk user accounts on the prowl
Spot compromised accounts and malicious insiders by reviewing accumulated user risk scores.
Triage all alerts triggered by a high-risk threat actor
Home in on a potentially malicious actor by examining all alerts triggered by a particular user.
Initiate an in-depth investigation immediately
Dive into the context of the attack and analyze the complete history of the user’s actions.
Make more informed remediation decisions
Collaborate with other security specialists and determine the best response to each incident.
Focus on user activity that presents a real threat
Easily adjust your alerting and scoring settings to accommodate any legitimate behavior typical for your environment.
Focus on user activity that presents a real threat
Easily adjust your alerting and scoring settings to accommodate any legitimate behavior typical for your environment.
Identify high-risk user accounts on the prowl
Spot compromised accounts and malicious insiders by reviewing accumulated user risk scores.
Triage all alerts triggered by a high-risk threat actor
Home in on a potentially malicious actor by examining all alerts triggered by a particular user.
Initiate an in-depth investigation immediately
Dive into the context of the attack and analyze the complete history of the user’s actions.
Make more informed remediation decisions
Collaborate with other security specialists and determine the best response to each incident.
Focus on user activity that presents a real threat
Easily adjust your alerting and scoring settings to accommodate any legitimate behavior typical for your environment.

Identify high-risk user accounts on the prowl
Spot compromised accounts and malicious insiders by reviewing accumulated user risk scores.

User Behavior and Blind Spot Analysis Reports
Stay on the Lookout for Subtle Indicators
of Compromise
and Security Blind Spots
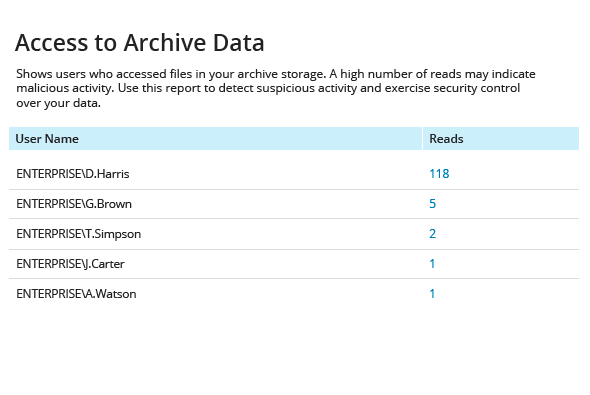
Has anyone been suspiciously active with stale data?
Keep an eye on activity around your stale data, because any access to it can indicate an attacker crawling through all the data you have looking for sensitive information.
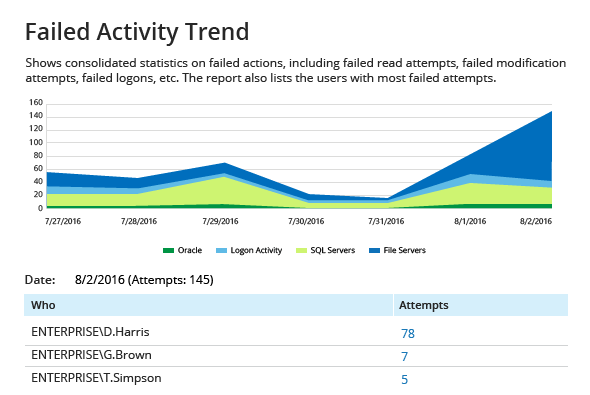
Have there been any abnormal surges in failed activity?
Get full visibility into failed activity across all critical IT systems for timely discovery of illicit attempts to access or modify your critical systems and data.
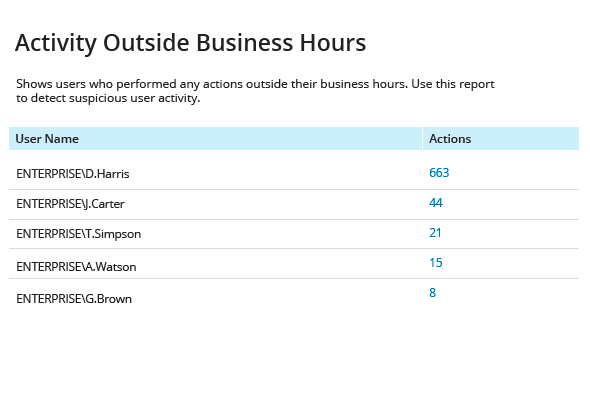
Has anyone been active when everyone else is off?
Chase down any user’s activity during non-business hours to detect an insider or attacker who’s crawling your network.
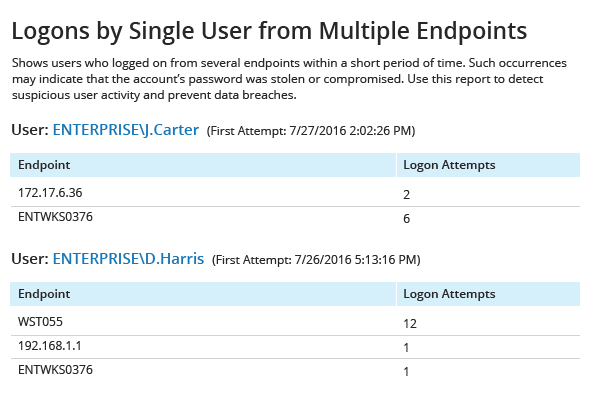
Have there been any suspicious logon attempts?
Stay ahead of possible identify theft by spotting any user attempting to log from multiple endpoints at the same time, or different users trying to log on from the same endpoint at the same time.
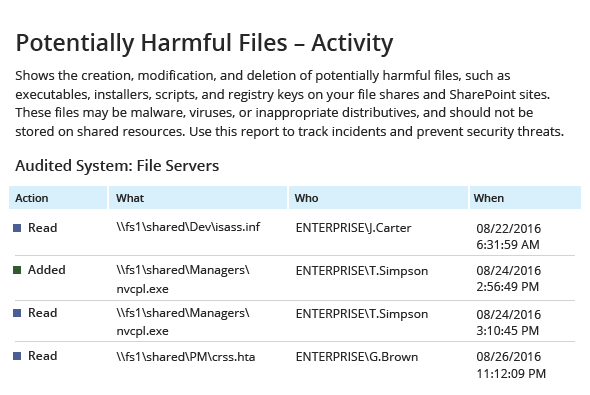
Has anyone placed any harmful files on your file shares?
Watch out for potentially harmful files on your file servers and SharePoint sites. If you detect any, quickly find out who added them and who has used them to pinpoint a potential attacker.
Has anyone been suspiciously active with stale data?
Keep an eye on activity around your stale data, because any access to it can indicate an attacker crawling through all the data you have looking for sensitive information.

Have there been any abnormal surges in failed activity?
Get full visibility into failed activity across all critical IT systems for timely discovery of illicit attempts to access or modify your critical systems and data.

Have there been any abnormal surges in failed activity?
Get full visibility into failed activity across all critical IT systems for timely discovery of illicit attempts to access or modify your critical systems and data.
Has anyone been active when everyone else is off?
Chase down any user’s activity during non-business hours to detect an insider or attacker who’s crawling your network.
Have there been any suspicious logon attempts?
Stay ahead of possible identify theft by spotting any user attempting to log from multiple endpoints at the same time, or different users trying to log on from the same endpoint at the same time.
Has anyone placed any harmful files on your file shares?
Watch out for potentially harmful files on your file servers and SharePoint sites. If you detect any, quickly find out who added them and who has used them to pinpoint a potential attacker.
Has anyone been suspiciously active with stale data?
Keep an eye on activity around your stale data, because any access to it can indicate an attacker crawling through all the data you have looking for sensitive information.
