Netwrix Auditor: The Dell Monitoring Software
Monitor file activity and permission drift across Dell Data Storage platforms with smart Dell storage monitoring that protects your most critical data.
Read their Stories
Trusted by




































































In-depth Dell monitoring software that protects data from the source
Detect data security threats
Gain visibility into suspicious changes and data access, anomalous user behavior, excessive access rights, and more.
Pass audits with less effort
Run Dell audits and generate reports for PCI DSS, HIPAA, SOX, FISMA, GLBA, CJIS, GDPR, and other regulatory standards.
Boost IT productivity
Simplify report creation and automate report delivery to facilitate regular review. Detect, investigate, and remediate unwanted changes.
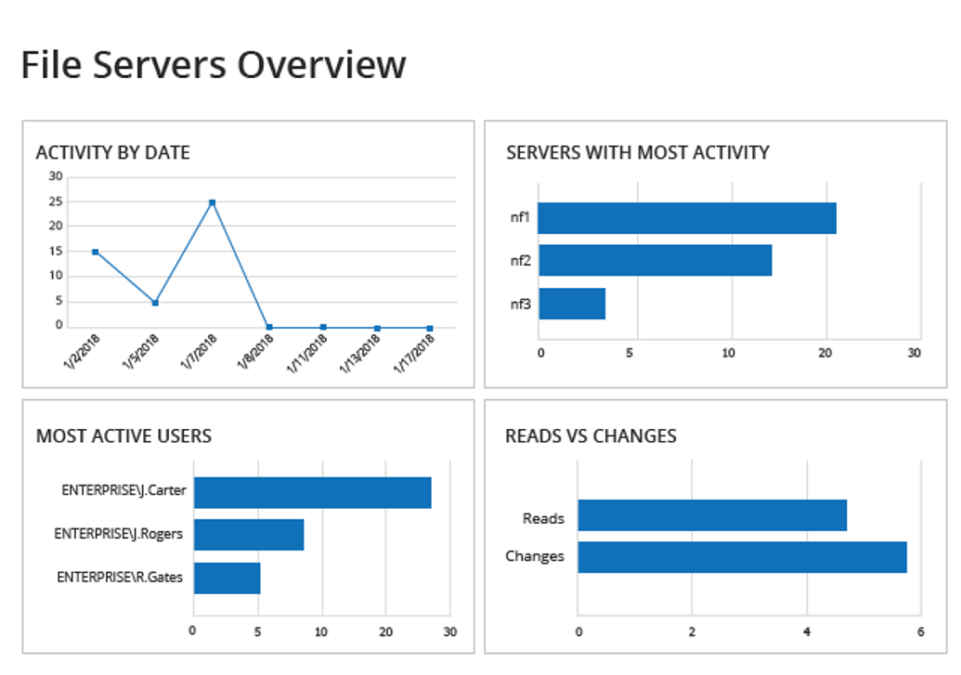
Get complete Dell Data Storage visibility
Get comprehensive visibility into Dell VNX, VNXe, Isilon, and Celerra storage with detailed tracking of every file and permission change.
Capabilities
An advanced Dell storage monitoring tool that makes sense of complex logs and empowers your team with proactive security
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.







