Netwrix Auditor: The Windows File Server Auditing Tool
Your file servers hold your most critical data. Run Windows File auditing to monitor every access attempt and modification, review permissions, and defend against break-ins.
Read their Stories
Trusted by




































































An in-depth Windows File server auditing tool that stops threats before they spread
Minimize risks to sensitive data
Know the sensitive data stored on your file servers, where that data is located, who has access rights to it, and how it’s being used.
Enhance IT team efficiency and simplify compliance
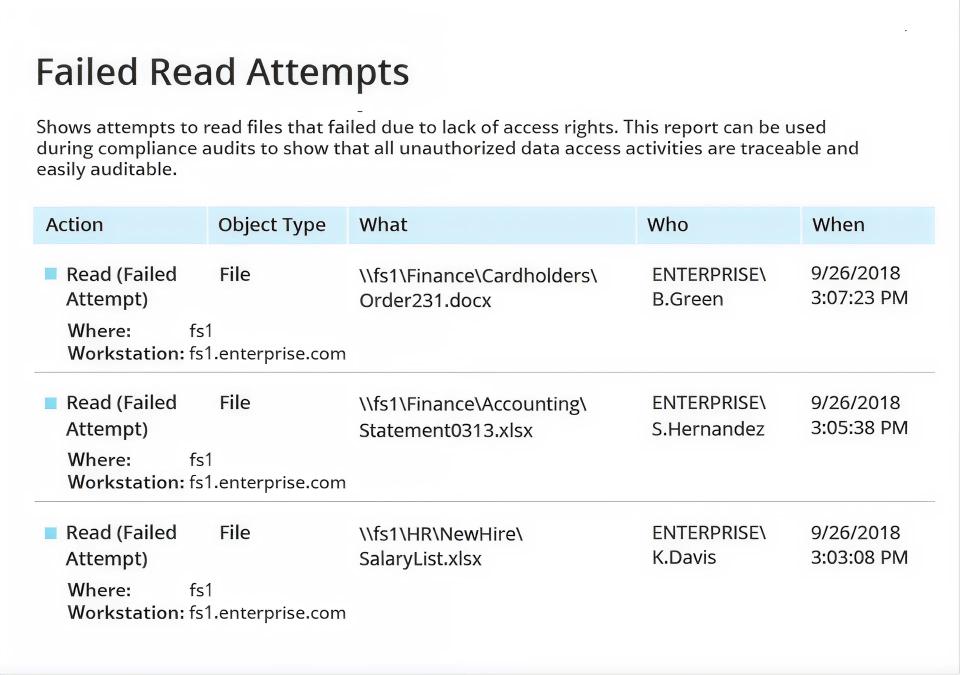
Streamline audit preparation with built-in reports mapped to many common mandates, and quickly answer ad-hoc questions from auditors.
Allow data owner-driven permission reviews
Let data owners conduct access reviews and approve permissions, ensuring accurate decisions while reducing IT burden.
Enable early ransomware detection
Catch mass file encryption attempts and suspicious bulk modifications before ransomware devastates your infrastructure.
Capabilities
Windows file server auditing software with the intelligence you need to defend against sophisticated file-based attacks
Ready to get started?
Solutions
Go beyond single-product protection. Secure every angle with Netwrix solutions.







