Data Security that Starts with Identity™
Management
Management
Management

Identity is the #1 attack vector
How are you securing identities, preventing privilege escalation and protecting your data?
Managing and securing ever-changing identity and data environments is critical in an era of AI-powered attacks.
Teams struggle with disparate tools that create complexity and visibility gaps.
Long implementation projects create security, compliance and financial risks.
At Netwrix, data security starts with identity, the #1 attack vector. We deliver comprehensive solutions that are quick to implement, cost effective and flexible to deploy.
Capabilities
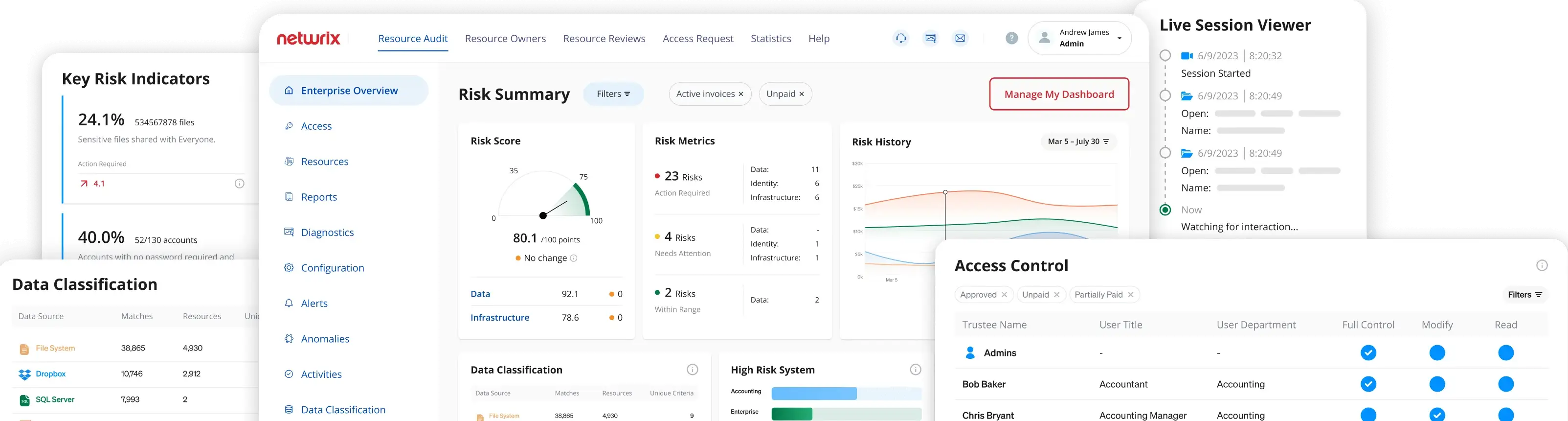
Risk Assessment
Discover and mitigate a wide variety of data and identity risks due to misconfigurations, vulnerabilities, and violations of policies, best practices, or desired states.
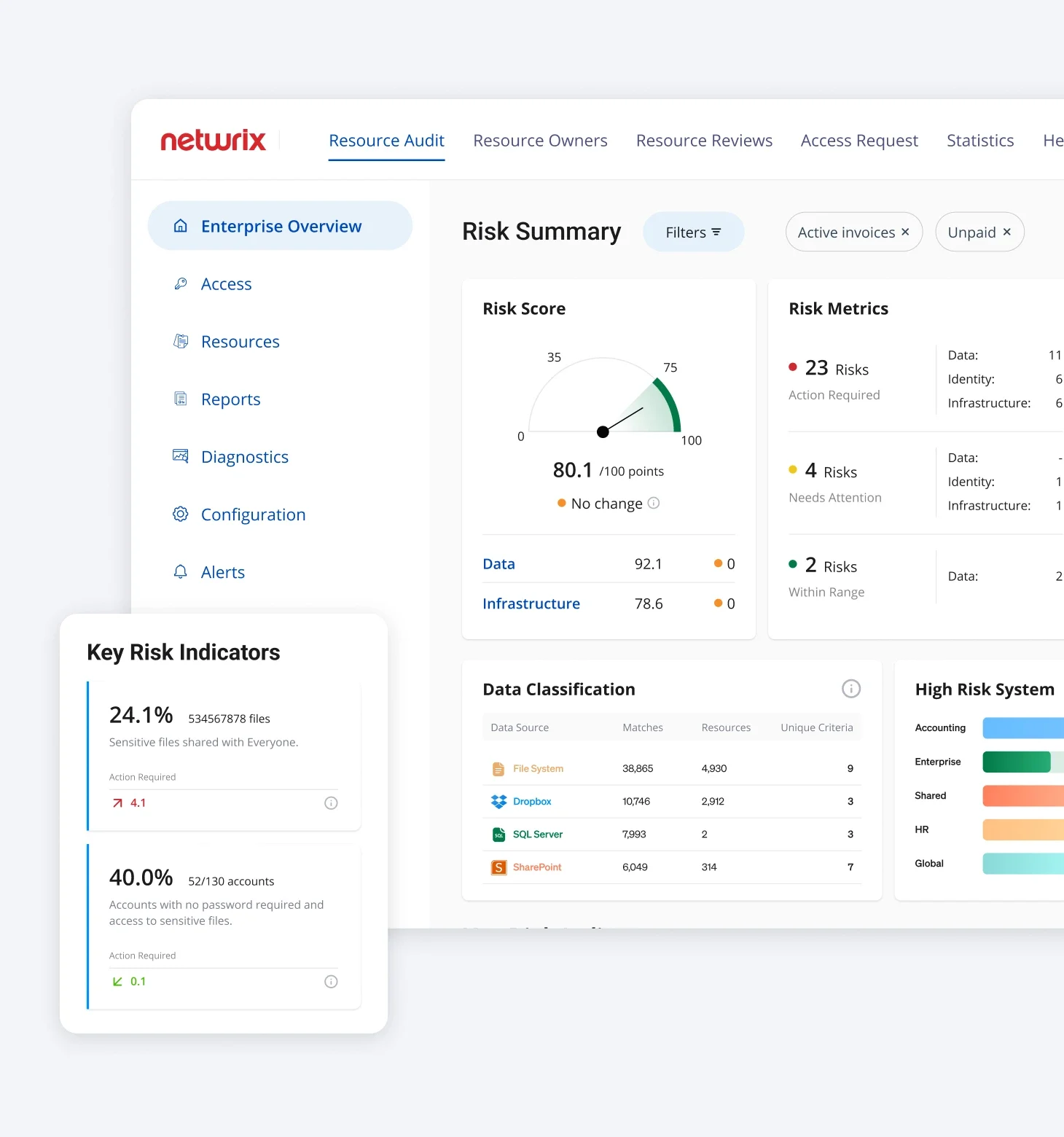
Threat Detection & Response
Monitor your IT environment for threats in real-time based on known frameworks, machine learning, and behavioral analytics. Flag real threats while reducing false positives.
Auto-remediate confirmed threats. Get a detailed report containing attack timelines, actions taken, vulnerabilities exploited, and more.
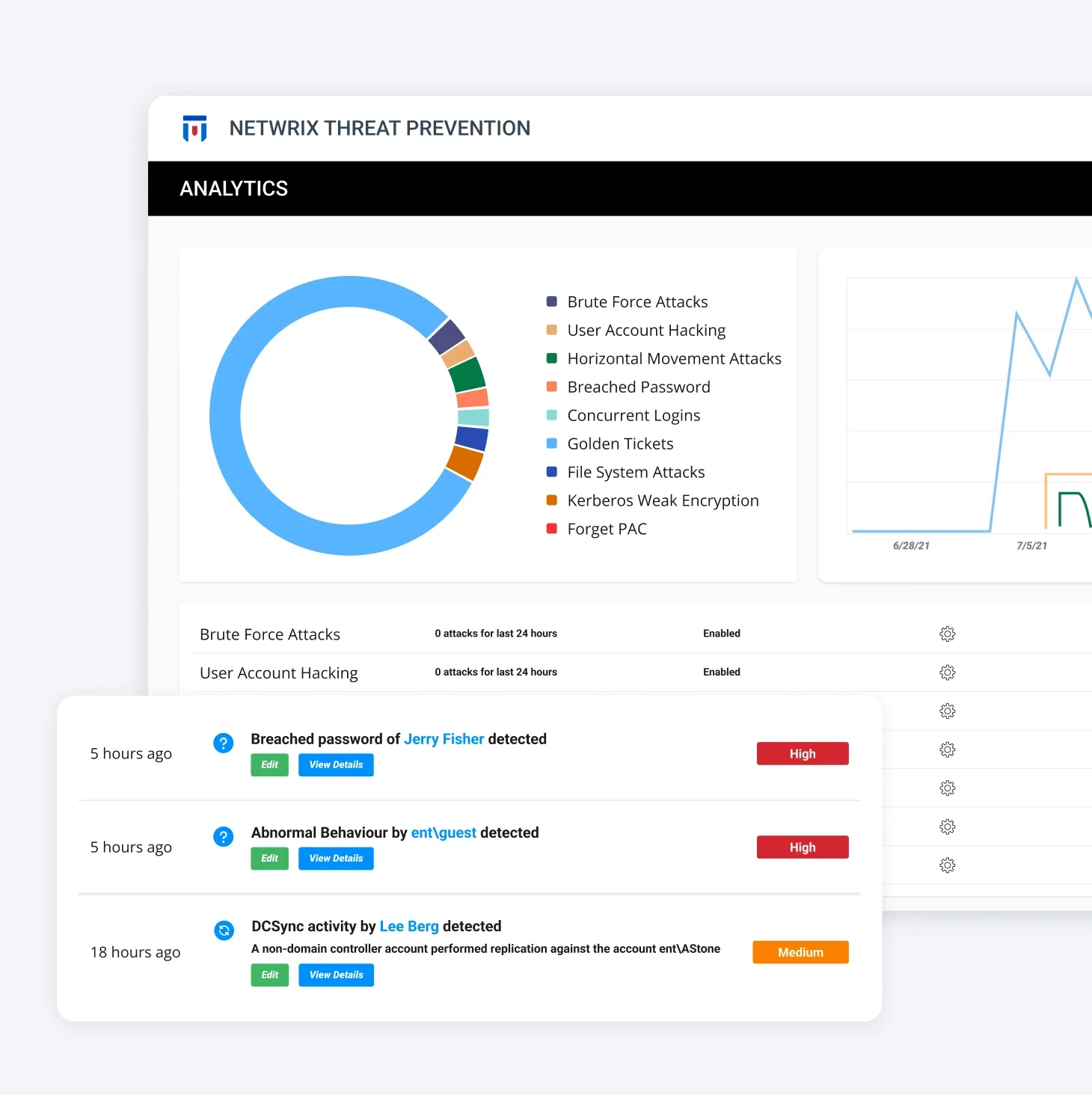
Policy Enforcement
Create & enforce security policies across ADs, endpoints, identity, network, etc. Manage user permissions, app settings, password rules, etc.
Automatically block risky behavior & remediate policy violations. Secure your environment without disrupting daily operations.
Rollback & Recovery
Manage access, policies, and identities to ensure the right users have access to the right resources at the right time. Reduce IT workload with automated workflows and self-service.
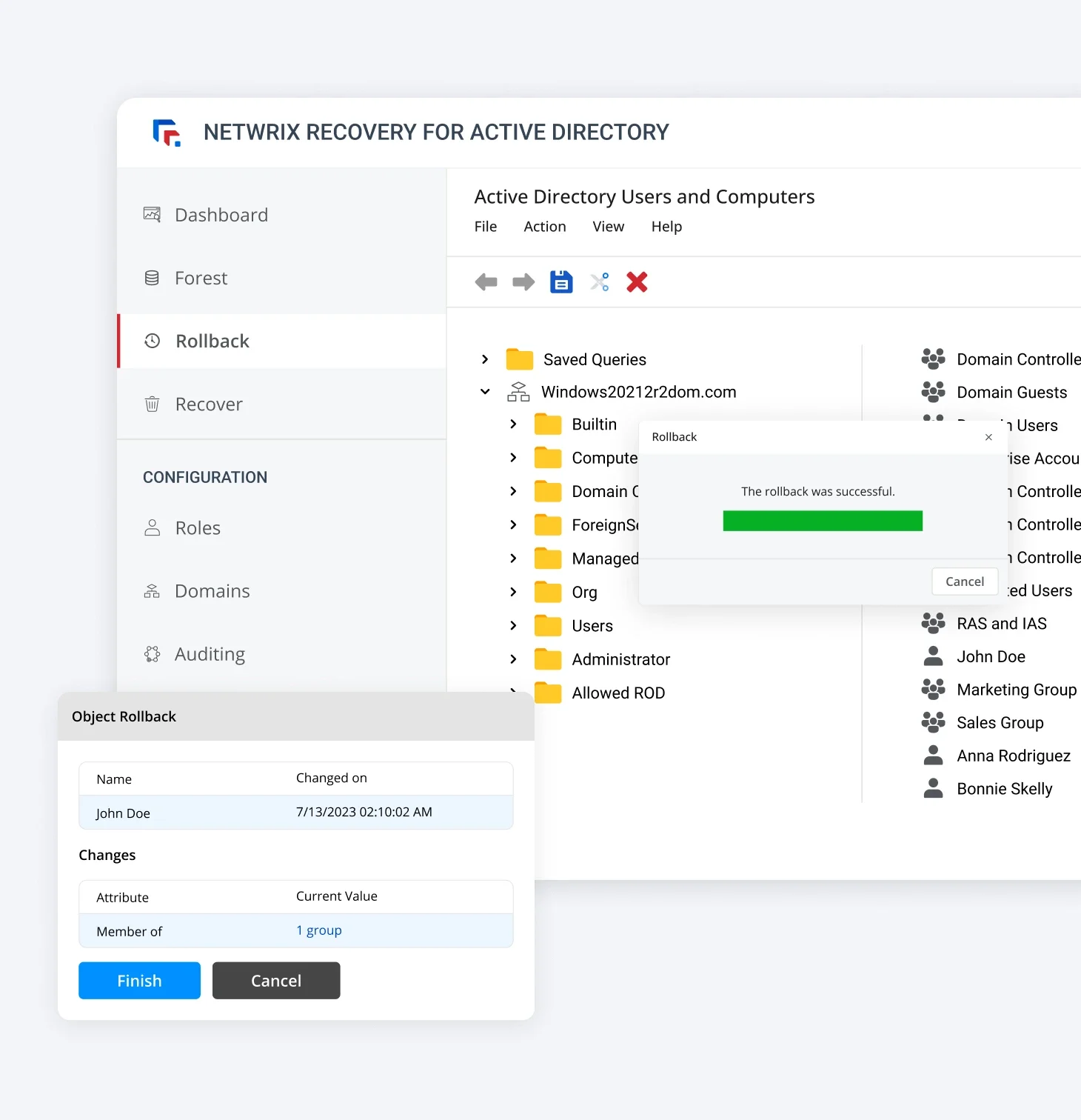
Management
Instantly roll back individual changes or restore your system to a previous state. Fix misconfigured permissions, group policies, and application settings.
View a full timeline of changes for quick troubleshooting. Automate backup creation to ensure reliable recovery points.
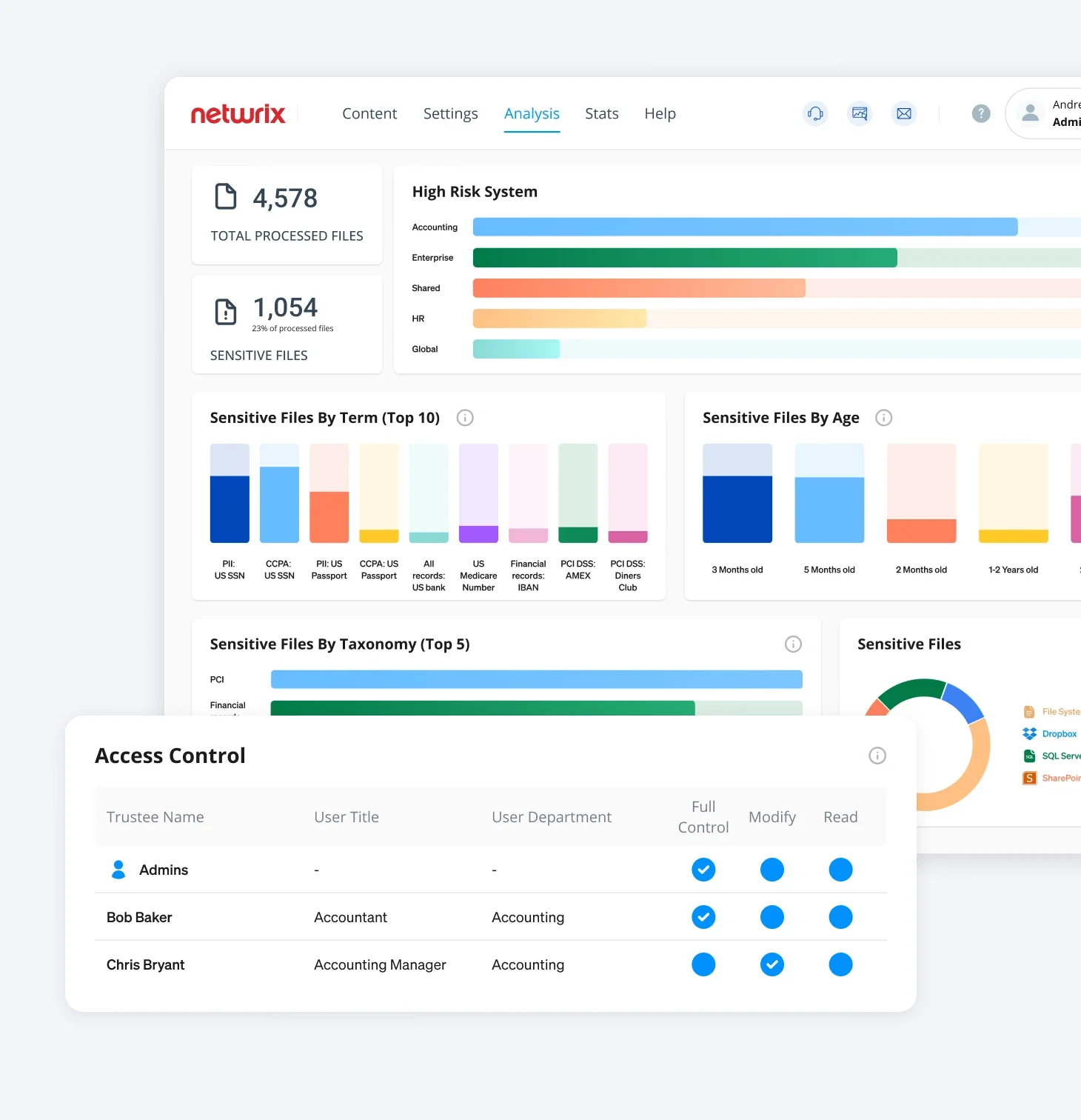
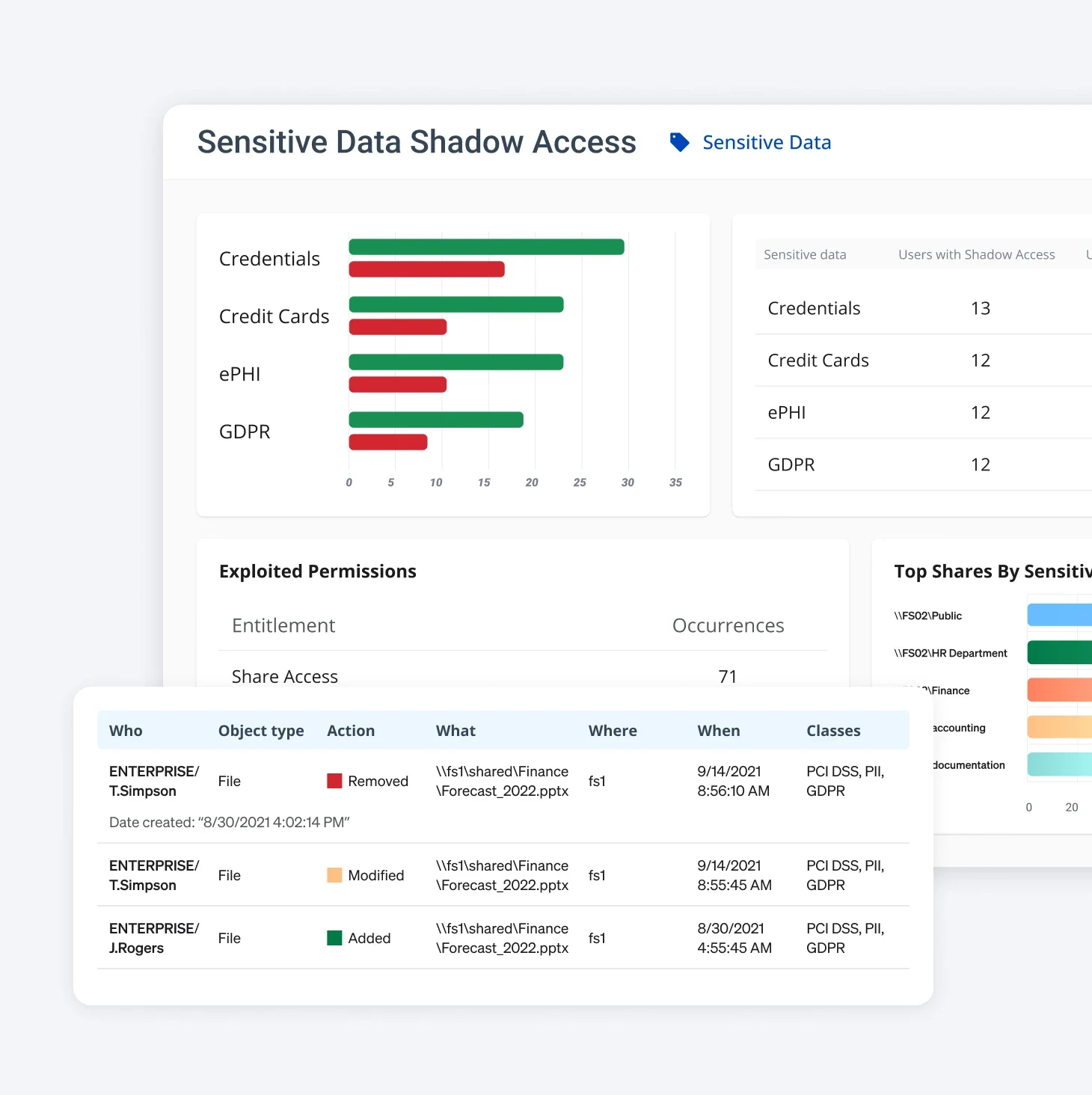
Governance & Compliance
Streamline compliance with automated monitoring and audit reporting.
Log access rights & data protection actions in real-time. Generate comprehensive audit reports in a few clicks. Prove compliance with industry regulations, including HIPAA, GDPR, ISO, NIST, etc.
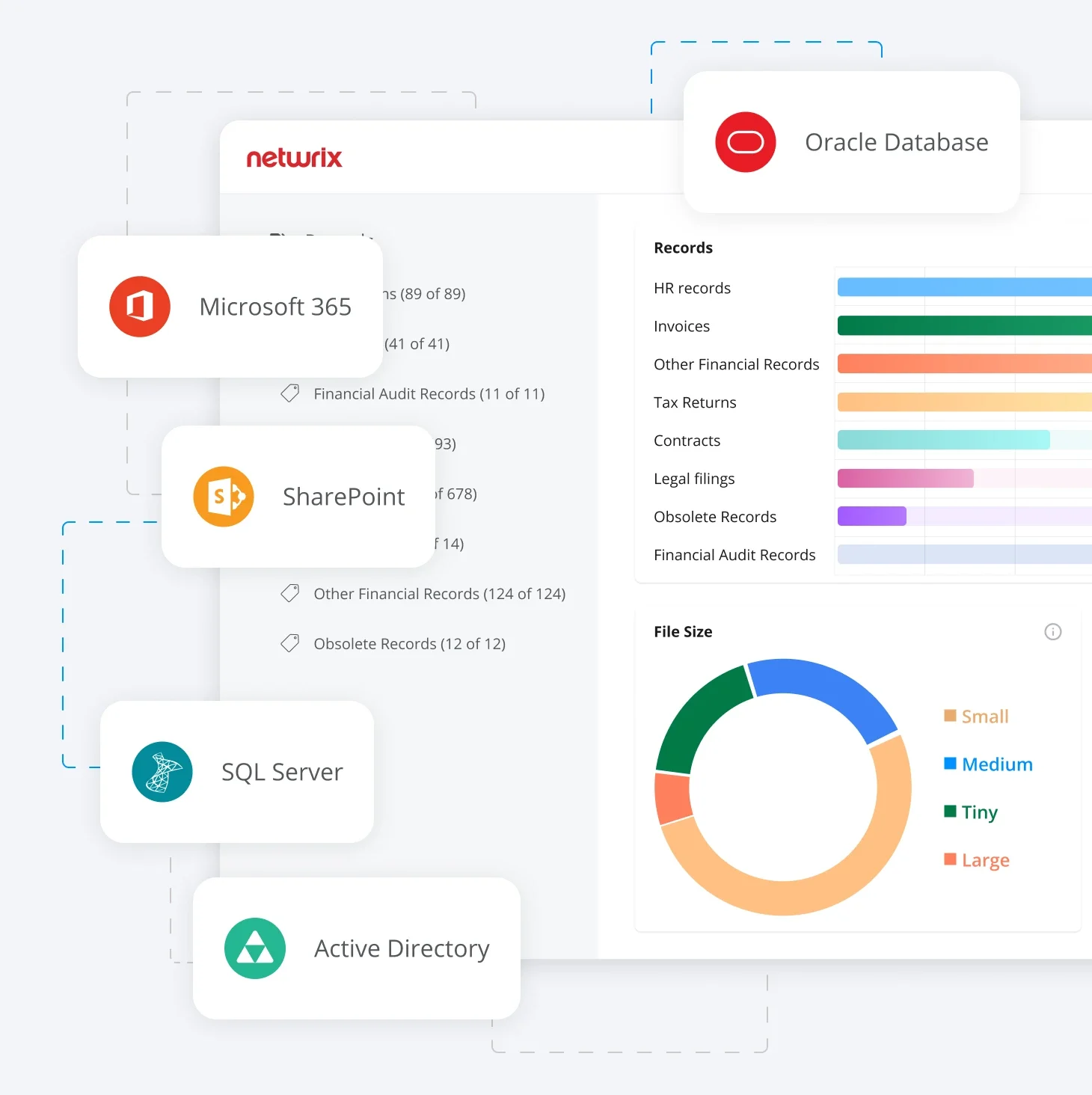
Integrations
Integrate with Microsoft Office 365, NetApp, Oracle, VMWare, SharePoint, and other enterprise platforms.
Connect with SIEM, ITSM, and identity management tools for automated workflows. Or build custom integrations with our API.
A successful journey depends on a good roadmap. Build a solid process to guide and measure your progress.
To achieve your security goals, you need a clear and effective strategy. Netwrix can help you with every phase of your security journey, and choosing integrated solutions will simplify the work while eliminating blind spots. The Netwrix portfolio addresses a complete range of cybersecurity functions:
IDENTIFY
Which data is sensitive?
Which accounts pose risk and why?
What gaps leave us vulnerable to threats?
protect
How can we enforce least privilege?
How can we minimize the risk posed
by admin accounts?
How can we prevent dangerous changes?
detect
Who is accessing sensitive data?
Is there any improper user activity?
Were all configuration changes approved?
respond
Do I have to report a data breach?
How can we respond to threats faster?
How did an incident occur?
recover
What data needs to be recovered?
How can we revert improper AD changes?
How could an incident have been blocked sooner or prevented altogether?
govern
What is the risk level of my data and how has it changed?
Can we demonstrate sensitive data security and privacy compliance?
Can we ensure business continuity and comply with regulations and policies?
COVER EVERY ELEMENT OF YOUR ENVIRONMENT
Get the comprehensive protection
you need
Today’s IT ecosystems are complex, but every element of the environment still needs to be secured and continuously monitored. That includes all the different types of data you store and process, the applications you use, and all your workstations, servers and network devices. Netwrix provides an integrated solution set that covers it all.
See why over 13,000 organizations
worldwide
rely on Netwrix
Day Pitney secures proprietary and customer data and reduces its risk exposure
Horizon Leisure Centres ensures GDPR compliance while saving £80,000 annually.
Vodafone complies with PCI DSS and protects customer PII, saving countless hours annually.
Eastern Carver County Schools maintains least privilege principle to secure data of 9,300 students.