Netwrix Auditor: The Active Directory Auditing Tool
Simplify Active Directory auditing with Netwrix. Detect and remediate risky permissions, suspicious user patterns, and policy tweaks.
Read their Stories
Trusted by





































































An Active Directory auditing tool that digs deeper
Detect insider threats
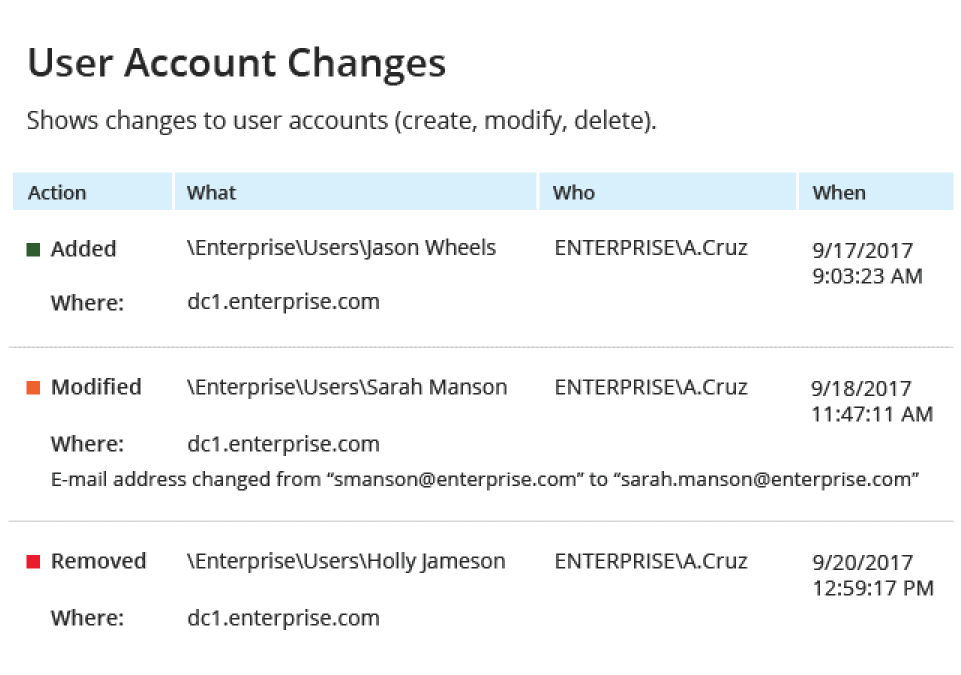
Gain visibility into all security and configuration changes in AD and Group Policy, such as privilege escalation or anomalous administrator activity.
Mitigate AD risks
Assess and remediate security gaps related to improper privilege assignment and management of accounts before they are exploited by attackers.
Pass audits with ease
Our AD audit software generates ready-made and customized reports for PCI DSS, HIPAA, SOX, GDPR, and other standards with zero manual formatting required.
Boost IT team productivity
Minimize service downtime by enabling administrators to quickly uncover the root causes of problems and roll back unwanted changes.
Capabilities
Secure your Active Directory and Group Policies with unified AD monitoring
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.






