How to Get VMware® Account Permissions
Native Solution
- Download the latest VMware® vSphere® PowerCLI™ installer from the Download page of the VMware® web site and install the PowerCLI software.
- Open the PowerShell ISE and create a new file with the following PowerShell script, specifying your own connection information, the report output path and the user name to collect report for:
#Connection info
$VIuser = 'DOMAIN\UserName'
$VIpass = 'Password'
$VIserver = '40.113.200.201'
$VIport = '443'
#Output path
$out = 'C:\VM_Permissions.csv'
#User to get report for
$user = 'DOMAIN\UserName'
#Connecting to vSphere
Connect-VIServer -Server $VIserver -Port $VIport -User $VIuser -Password $VIpass
#Collecting information
$rep = foreach($vm in Get-Inventory){
Get-VIPermission -Entity $vm|Where-Object {$_.Principal -eq $user}|
Select Principal,Role, Propagate,IsGroup,
@{N='Object_ID';E={$vm.Id}},
@{N='Object_Name';E={$vm.Name}},
@{N='Uid';E={$vm.Uid}}
}
$rep |Export-Csv -Path $out -NoTypeInformation
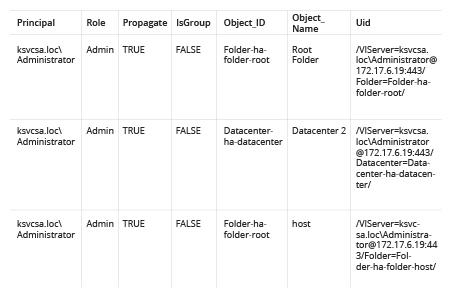
- Open and review the resulting CSV report:
Netwrix Auditor for VMware
- Run Netwrix Auditor and navigate to Reports → Predefined → VMware → VMware -State-in-Time → Account Permissions in vCenter.
- Click View.
- Type the desired user name into the User (domain\account) filter and click View Report.
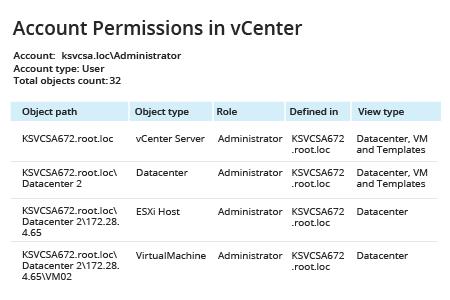
- Clicking the Object path link opens a report that shows who has permissions to that object.
- The Role link opens a detailed report on privileges for that role.
- Clicking the Defined in link will show you accounts with explicit or inherited permissions on that object.
Share on
