How to Check User Permissions in Active Directory
Netwrix Auditor for Active Directory
- Run Netwrix Auditor → Navigate to "Reports" → Expand the "Active Directory" section → Go to "Active Directory - State-in-Time" → Select "Account Permissions in Active Directory" → Click "View".
- Specify the values for the filters below and click "View Report":
- Account UNC Path
- Means Granted
- Permissions
- To save the report, click the "Export" button → Choose a format from the dropdown menu → Click "Save".
Learn more about Netwrix Auditor for Active Directory
Native Auditing
- Open the Powershell ISE → Create a new script with the following code, specifying the username and path for the export → Run the script.
Import-Module ActiveDirectory
# Array for report.
$report = @()
$schemaIDGUID = @{}
# ignore duplicate errors if any #
$ErrorActionPreference = 'SilentlyContinue'
Get-ADObject -SearchBase (Get-ADRootDSE).schemaNamingContext -LDAPFilter '(schemaIDGUID=*)' -Properties name, schemaIDGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.schemaIDGUID,$_.name)}
Get-ADObject -SearchBase "CN=Extended-Rights,$((Get-ADRootDSE).configurationNamingContext)" -LDAPFilter '(objectClass=controlAccessRight)' -Properties name, rightsGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.rightsGUID,$_.name)}
$ErrorActionPreference = 'Continue'
# Get a list of AD objects.
$AOs = @(Get-ADDomain | Select-Object -ExpandProperty DistinguishedName)
$AOs += Get-ADOrganizationalUnit -Filter * | Select-Object -ExpandProperty DistinguishedName
$AOs += Get-ADObject -SearchBase (Get-ADDomain).DistinguishedName -SearchScope Subtree -LDAPFilter '(objectClass=*)' | Select-Object -ExpandProperty DistinguishedName
# Loop through each of the AD objects and retrieve their permissions.
# Add report columns to contain the path.
ForEach ($AO in $AOs) {
$report += Get-Acl -Path "AD:\$AO" |
Select-Object -ExpandProperty Access |
Select-Object @{name='organizationalunit';expression={$AO}}, `
@{name='objectTypeName';expression={if ($_.objectType.ToString() -eq '00000000-0000-0000-0000-000000000000') {'All'} Else {$schemaIDGUID.Item($_.objectType)}}}, `
@{name='inheritedObjectTypeName';expression={$schemaIDGUID.Item($_.inheritedObjectType)}}, `
*
} # Filter by single user and export to a CSV file.
$User ='Username'
$report | Where-Object {$_.IdentityReference -like "*$User*"} | Select-Object IdentityReference, ActiveDirectoryRights, OrganizationalUnit, IsInherited -Unique |
Export-Csv -Path "C:\data\explicit_permissions.csv" -NoTypeInformation
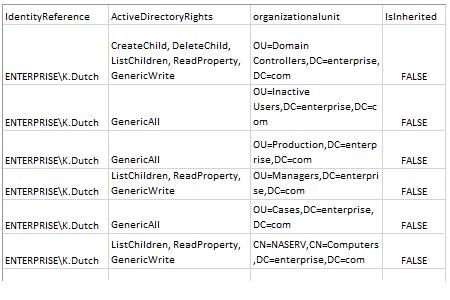
- Start MS Excel and open the file produced by the script.
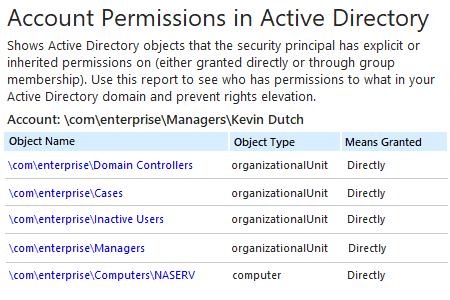
Sample report:
Reduce Your Attack Surface Areas by Continuously Checking Active Directory User Permissions Reports
For proper Active Directory management and better security, best practices require permissions to be inherited via Active Directory group membership rather than assigned explicitly. But ensuring that access rights follow this principle can be a challenge. IT administrators need to regularly view Active Directory user permissions reports that detail how permissions were granted so they can remove any that were assigned explicitly, as well as work with data owners to remove users from groups that grant them permissions they don’t need them for their everyday work. Regular permissions review and cleanup helps minimize the risk of privilege abuse and data breaches. But creating reports relying on a reporting tool such as PowerShell and reviewing cryptic output is both time consuming and error prone.
Netwrix Auditor for Active Directory overcomes the limitation of PowerShell scripting by delivering a comprehensive report listing all objects that a particular user has access to and whether the rights were granted through group membership or explicitly. You can easily drill down for more details, such as exactly which permissions the user has on a specific object.
Share on
