How to Detect Who Created a User Account in Active Directory
Native Auditing vs. Netwrix Auditor for Active Directory
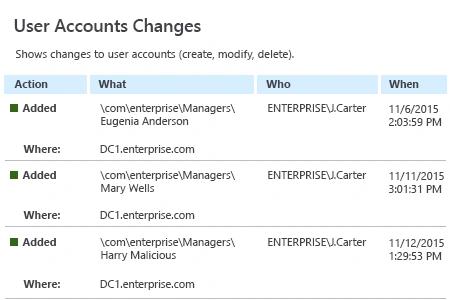
Netwrix Auditor for Active Directory
- Run Netwrix Auditor → Navigate to "Reports" → Expand the "Active Directory" section → Go to "Active Directory Changes" → Select "User Account Changes" → Click "View".
- Set the "Actions" filter to "Added" → Click "View Report".
If you want to get this report by email regularly, simply choose the "Subscribe" option and define the schedule and recipients.
Native Auditing
- Run gpmc.msc → open "Default Domain Policy" → Computer Configuration → Policies → Windows Settings → Security Settings:
- Local Policies → Audit Policy → Audit account management → Define → Success.
- Event Log → Define → Maximum security log size to 1gb and Retention method for security log to Overwrite events as needed.
- Open ADSI Edit → Connect to Default naming context → right click "DC=domain name" → Properties → Security (Tab) → Advanced → Auditing (Tab) → Click "Add" → Choose the following settings:
- Principal: Everyone; Type: Success; Applies to: This object and all descendant objects; Permissions: Create all child objects → Click "OK".
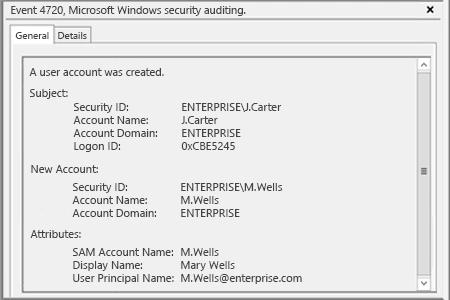
- In order to define what user account was created filter Security Event Log for Event ID 4720.
Learn more about Netwrix Auditor for Active Directory
Continuously Monitor Changes to Quickly Determine Who Created AD User Accounts
Malicious individuals who obtain administrative access to your Active Directory domain can breach the security of your network. Any changes to a user account password made by anyone other than the account owner or an IT administrator might be a sign of an Active Directory account hack. A malefactor who has stolen administrative credentials and used them to change a user account password has complete access to the account and can use it to read, copy and delete data in Active Directory. As a result, your organization can suffer system downtime, business disruptions or leaks of sensitive data.
By closely monitoring password changes, including every password reset in Active Directory, IT pros can detect suspicious activity and troubleshoot issues to stop attackers before it’s too late. Netwrix Auditor for Active Directory provides predefined reports that show which accounts had password changes, enabling IT admins to keep those changes under close control. Moreover, the application provides details on each user password reset, so you can easily see who has reset a user password in Active Directory and when and where the change was made.
Share on
