How to Detect User Account Changes in Active Directory
Native Auditing vs. Netwrix Auditor for Active Directory
Netwrix Auditor for Active Directory
- Run Netwrix Auditor → Navigate to "Reports" → Expand the "Active Directory" section → Go to "Active Directory Changes" → Select "User Account Changes" → Click "View".
If you want to get this report by email regularly, simply choose the "Subscribe" option and define the schedule and recipients.
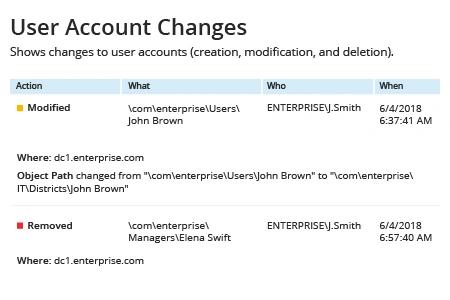
Native Auditing
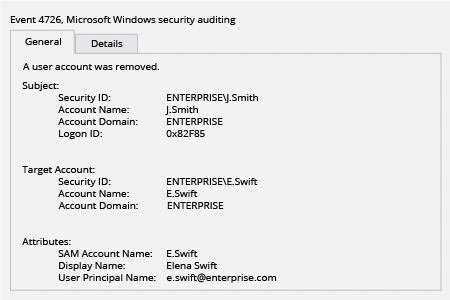
- Enable audit policies on the Default Domain Controller Security Policy GPO. Enable the "Audit user account management" audit policy.
- Look for event ID 4720 (user account creation), 4722 (user account enabled), 4725 (user account disabled), 4726 (user account deleted) and 4738 (user account changed).
- Keep in mind that when you initially create a user account, AD creates the account as disabled, makes several initial updates to it and then immediately enables it. Therefore you will always see a somewhat bogus occurrence of 4722 associated with each new account created.
Learn more about Netwrix Auditor for Active Directory
Monitor User Account Changes to Quickly Detect Intruders
Compliance and security considerations make tracking of user account changes in Active Directory very important. Modifications that can be a sign of malicious activity include a large number of newly created AD user accounts with extended permissions; a large number of inactive user accounts; AD user accounts that have been disabled or suspiciously modified; and accounts that have suddenly become active after a long period of account inactivity. Continuous monitoring of these kinds of changes helps IT pros detect malicious activity in a timely manner and thereby avoid leaks of sensitive data.
Netwrix Auditor for Active Directory detects AD user account changes and provides detailed audit reports that show who made each change and what was changed. An email subscription to the Active Directory Change Summary report will help you stay informed of all changes to user accounts in Active Directory and help you spot malicious modifications before they lead to the loss of sensitive data. In some cases, Netwrix Auditor can strengthen security even further; for example, the Inactive Users Tracking feature automatically disables inactive user accounts, making them unavailable for intruders.
Share on
