Netwrix Auditor: The Microsoft Exchange Monitoring Tool
Guard your inboxes with Exchange monitoring software. Monitor mailbox snooping, track permission changes, and catch configuration tampering across on-prem and cloud.
Read their Stories
Trusted by




































































An Exchange audit tool that offers complete visibility in hybrid environments
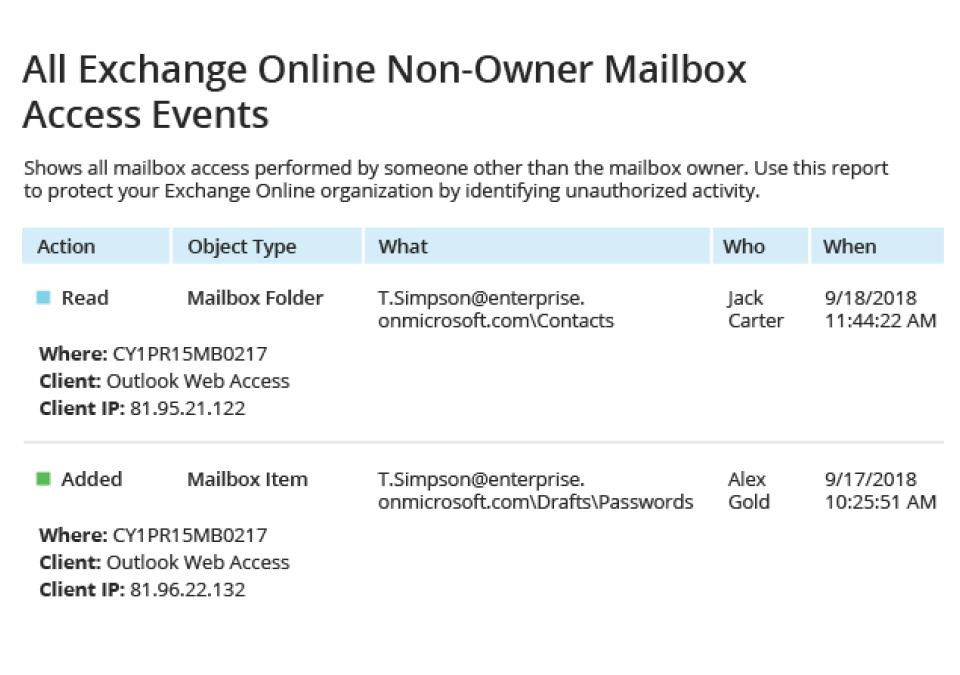
Detect and investigate security threats
Get complete visibility into changes, permissions, and access events across your on-premises, cloud, or hybrid Exchange ecosystem.
Prove compliance with less effort
Save time and money preparing for compliance audits with out-of-the-box reports for PCI DSS, HIPAA, GDP,R and many other compliance regulations.
Boost IT productivity
Slash helpdesk workload and avoid email disruptions by promptly detecting and investigating suspicious activity and quickly remediating improper changes.
Hybrid deployment support
Monitor on-premises Exchange Server and Exchange Online from one unified Microsoft Exchange monitoring tool without managing separate platforms.
Capabilities
Simplify audits and maintain service availability with smart Exchange auditing software
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.







