Netwrix Auditor: The Oracle Database Monitoring Software
Capture every SQL statement, privilege change, and access attempt with the Oracle Database monitoring tool built for DBAs.
Read their Stories
Trusted by




































































Oracle Database monitoring that scales with your operation
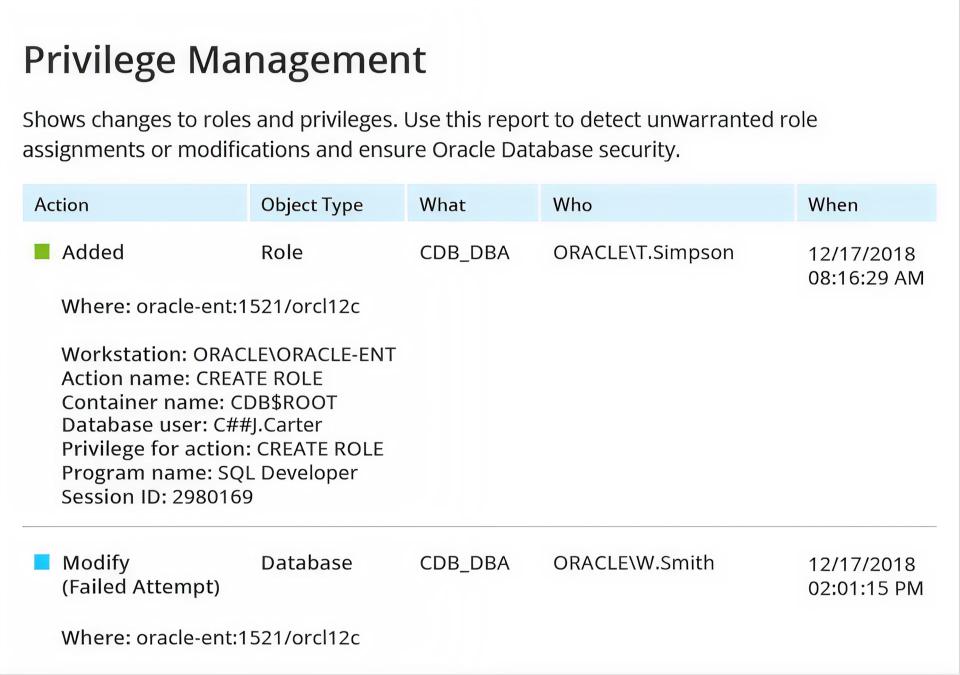
Detect database security threats
Gain visibility into suspicious logins, changes to permissions and database objects, and data access events with Oracle Database monitoring software.
Pass compliance with less effort
Deliver out-of-the-box compliance reports aligned with PCI DSS, HIPAA, SOX, GLBA, FISMA/NIST, CJIS, GDPR, and other regulations.
Increase DBA productivity
Slash the time required for reporting. Plus, spot and chase down unsanctioned activity, such as the alteration or deletion of a database.
See DBA activity accountability
Hold database administrators accountable by tracking all privileged operations, configuration changes, and system modifications.
Capabilities
Powerful Oracle Database monitoring tools that deliver actionable insights fast and when it matters most
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.







