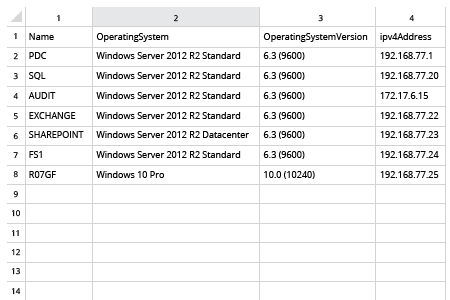
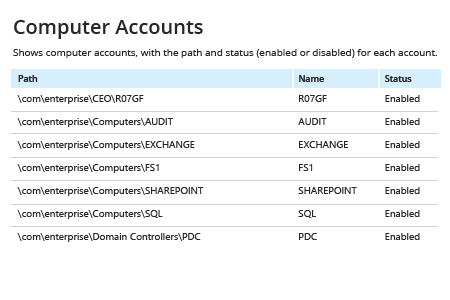
Every computer account, like every user account, is a door into your network. If computer accounts are not protected with proper password settings and disabled in a timely manner, or they are simply left unattended, they can be easily exploited by malicious actors. Regularly reviewing the list of all computers in your domain helps keep your IT environment clean and in line with proper security policy.
Netwrix Auditor for Active Directory gives you visibility into your Active Directory configuration. Unlike native methods that require PowerShell scripting, Netwrix Auditor requires exactly zero coding to export a list of computers from Active Directory to CSV or another format. Simply pull up one of the predefined reports or access the data using the Interactive Search feature. In both cases, the software provides flexible filters and multiple export formats, including PDF, CSV and Excel. The human-readable information includes all the critical details, including computer names, path and account status. You can then use this information to disable or delete idle computer accounts through Microsoft Active Directory Users and Computers, thereby closing off avenues for attackers to breach your network.