Identify, Assess and Reduce Risks to
Your
IT Infrastructure and Data
smarter IT security decisions and
close security holes.
in one place to improve detection of rogue
insiders and compromised accounts.
the excessive permissions to mitigate
the risk of privilege abuse.
workflows and maximize visibility
into your Linux environment.
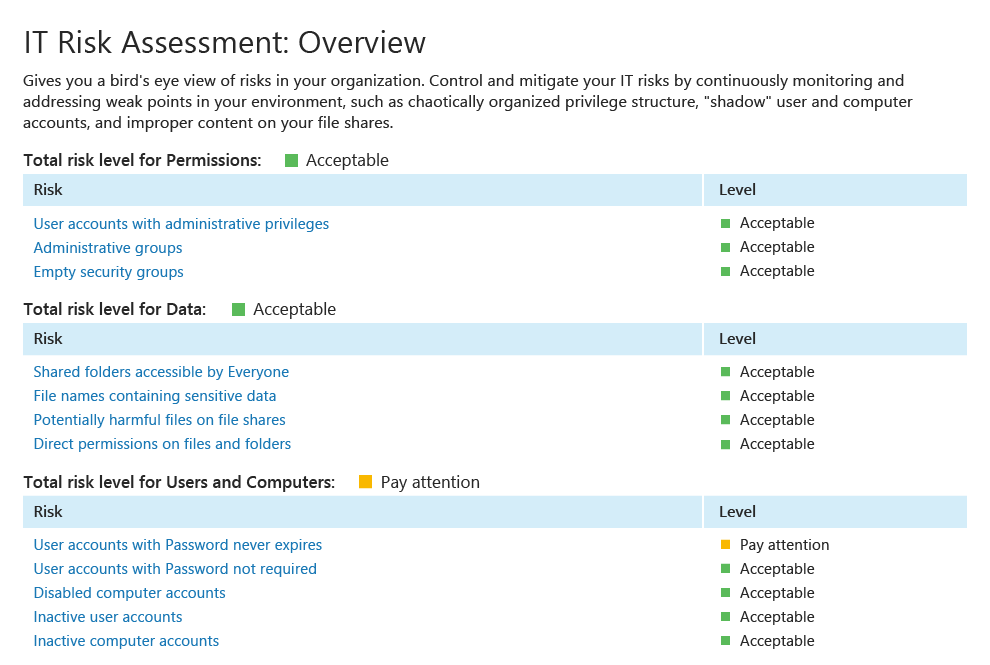
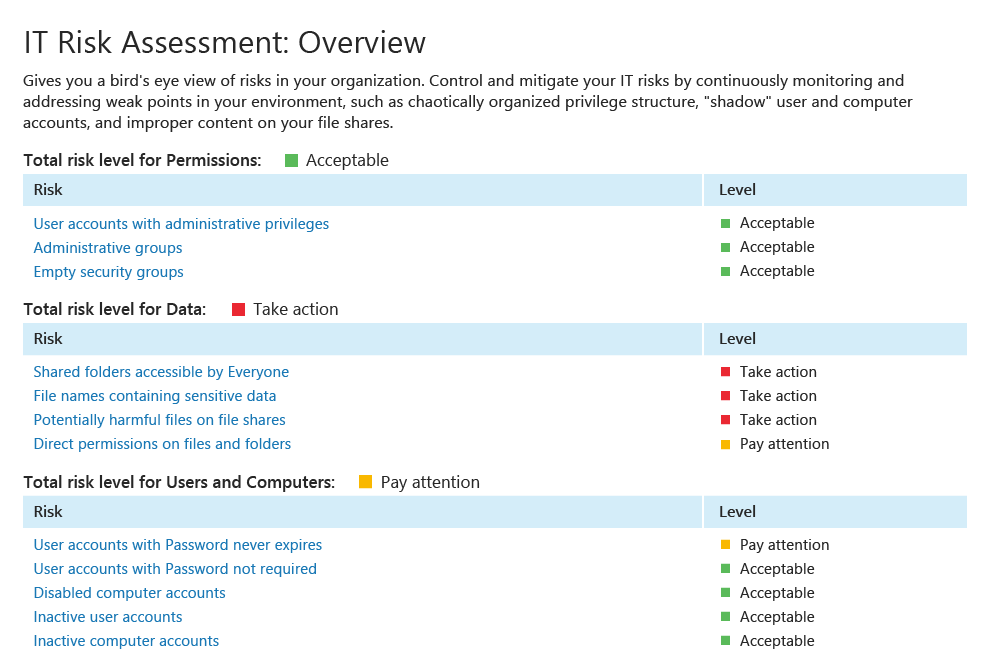
Close security holes by identifying
and prioritizing risks
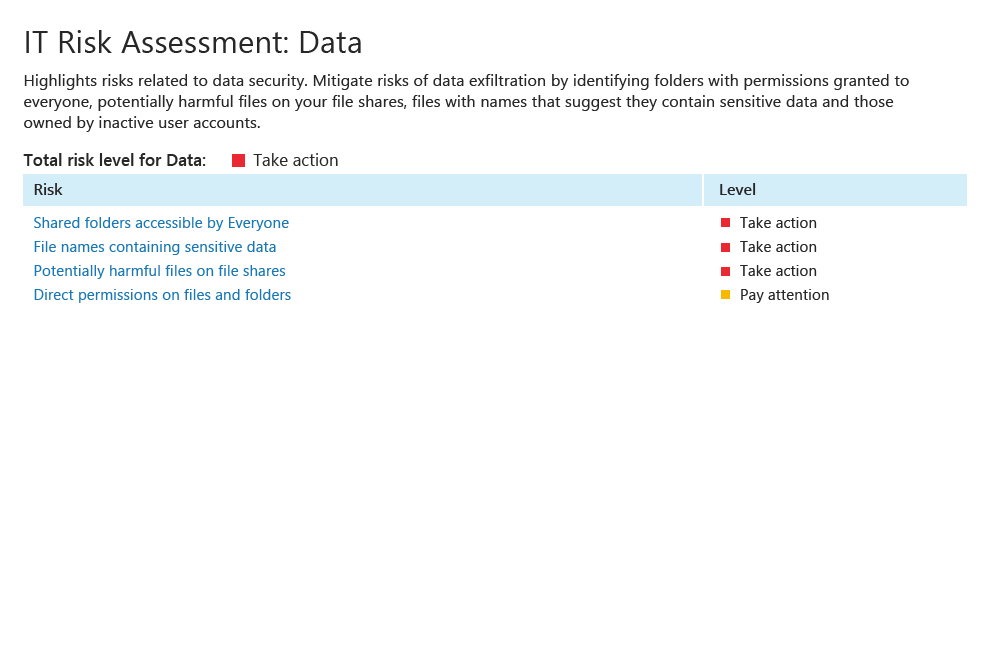
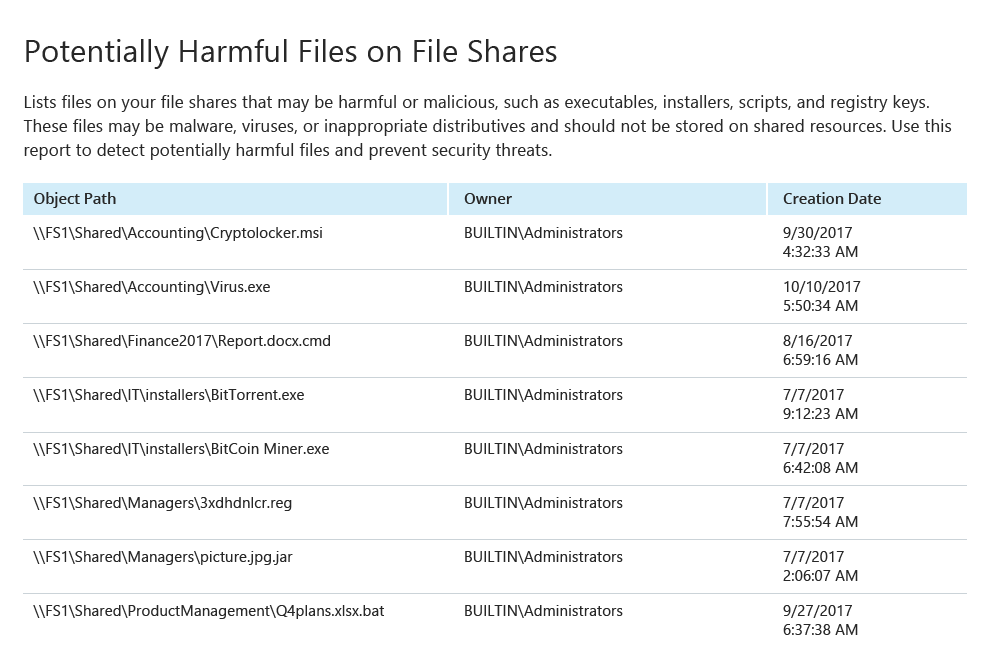
Minimize the ability of intruders and insiders to steal data or cause damage
by proactively reducing
your
attack surface area. Enable continuous
risk
assessment
with interactive risk
dashboards that
help you
detect,
evaluate and act on gaps
in security, governance and compliance
best practices.
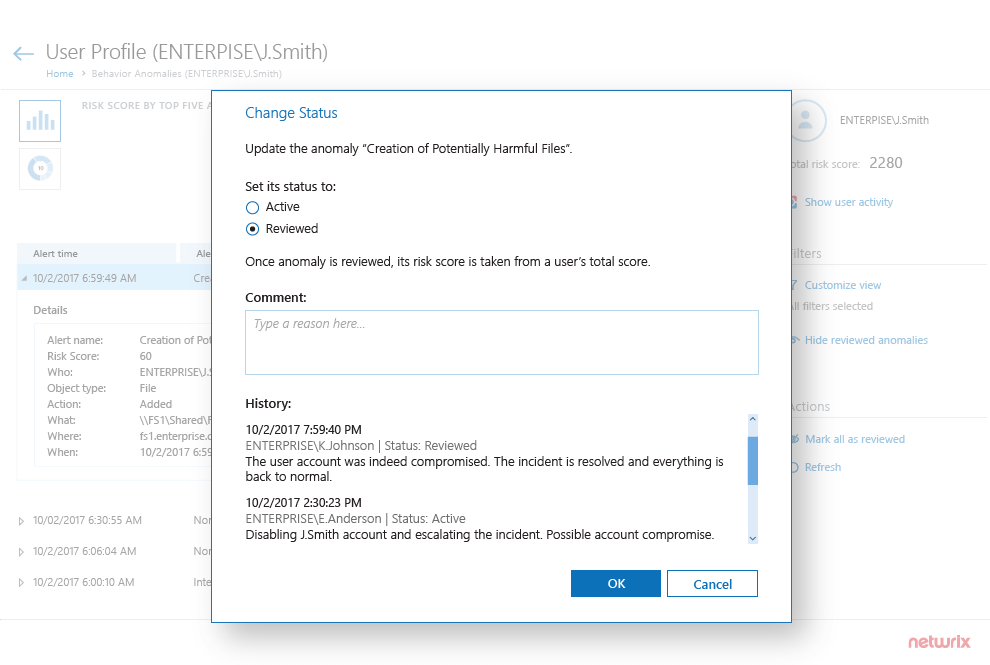
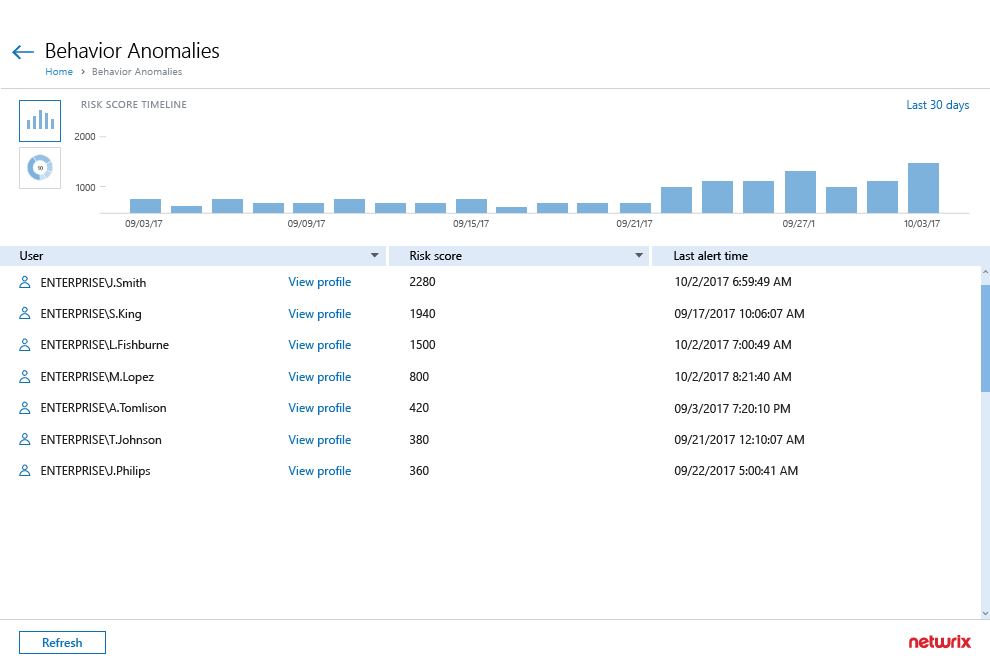
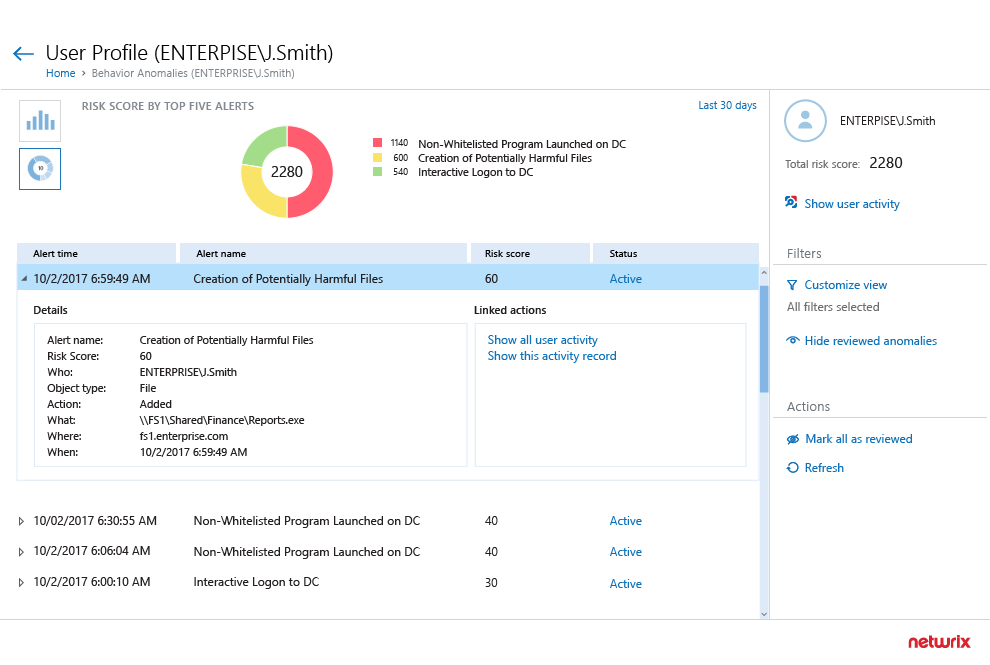
Improve detection of malicious insiders
and compromised accounts
Spot and investigate anomalies in user
behavior in time
to block external
attackers who
have compromised
valid
user accounts and thwart trusted
insiders who have gone rogue.
Speed incident response and maximize visibility
into your Linux environment
Streamline incident detection and response workflows and expand visibility across your
IT
environment using
free, ready-to-use add-ons.
Management
Provide initial incident support and enable faster and more accurate incident investigation with detailed tickets created automatically from Netwrix Auditor alerts.
Download Free Add-onon Linux and Unix Systems
Promptly identify and respond to improper behavior in your *nix-like systems by gaining full control over privilege elevations via the SUDO command and OpenSSH sessions.
Download Free Add-onSpot, investigate and block threats to your Linux environment with a single-pane view of what’s happening there. Stay alert to multiple authentication failures, failed attempts to run the SU command and other threat indicators.
Download Free Add-on
Learn about additional enhancements
that improve
usability, performance and scalability.

See the full list of Netwrix Auditor advantages and learn
more about
how to improve
your
ability to
assess IT security risks
and detect malicious insiders and compromised accounts.
Download New Datasheet.pdf
Recorded webinar
in
Netwrix Auditor 9.5