Centro de recursosGuia prático
Como Detectar Quem Concedeu Permissões de Acesso Total à Caixa de Correio de Outro Usuário
Como Detectar Quem Concedeu Permissões de Acesso Total à Caixa de Correio de Outro Usuário
Auditoria Nativa
- Abra o Exchange Management Shell e execute os seguintes cmdlets:
- Set-AdminAuditLogConfig – AdminAuditLogEnabled $true
- Set-AdminAuditLogConfig – LogLevel Verbose (para Exchange 2013).
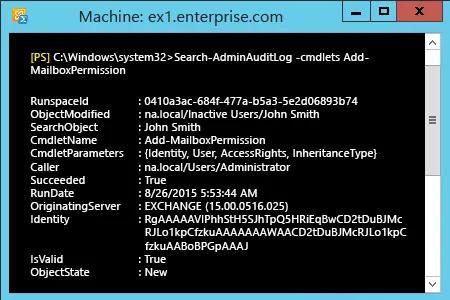
- Execute eventvwr.msc → Aplicativos e Logs de Serviços → MSExchange Management → procure pelo log com cmdlet "Add(Remove)-MailboxPermission" – onde você pode encontrar informações sobre quem alterou as permissões das caixas de correio, quando aconteceu, para qual caixa de correio e que tipo de acesso foi concedido a quem. Você também pode encontrar essas informações no Exchange Admin Center no seu navegador → Gerenciamento de Conformidade → Auditoria → clique em "Visualizar o log de auditoria do administrador".
- Você também pode encontrar essa informação no Exchange Admin Center no seu navegador → Gerenciamento de Conformidade → Auditoria → clique em "Ver o registro de auditoria do administrador".
- Também via power shell - Abra o Exchange Management Shell e execute o seguinte cmdlet:
- Search-AdminAuditLog –cmdlets Add(Remove)-MailboxPermission.
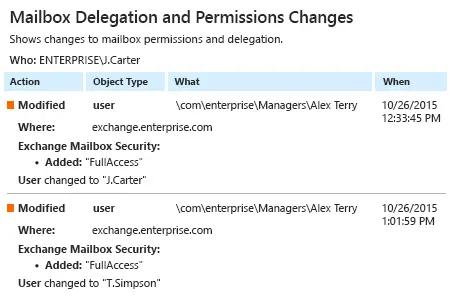
Netwrix Auditor para Exchange
- Execute o Netwrix Auditor → Clique em "Relatórios" → escolha Exchange → Escolha "Alterações de Delegação e Permissões de Caixa de Correio" → clique em "Visualizar".
Compartilhar em
