- Navigate to the required file share → Right-click it and select "Properties".
- Go to the "Security" tab → Click the "Advanced" button → Switch to the "Auditing" tab → Click the "Add" button and define auditing:
- Principal equals "Everyone"
- Type equals "All"
- Applies to: "This folder, subfolders and files".
- Select the following "Advanced Permissions":
- Traverse folder / execute file
- List folder / read data
- Create files /write data
- Create folders / append data
- Write attributes.
- Run gpedit.msc → Go to the "Edit" menu.
- Create a new policy → Edit → Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → Audit Policy:
- Audit object access → Define → Success and Failures
- Go to "Advanced Audit Policy Configuration" → Audit Policies → Object Access:
- Audit File System → Define → Success and Failures
- Audit Handle Manipulation → Define → Success and Failures
- Go to Event Log → Define:
- Maximum security log size to 4gb
- Retention method for security log to "Overwrite events as needed"
- To link the new GPO to the OU with file servers, go to "Group Policy Management" → Right-click the defined OU → Choose "Link an Existing GPO" → Select the GPO that you’ve created.
- To force the group policy update, go to "Group Policy Management" → Right-click the defined OU → Сlick "Group Policy Update".
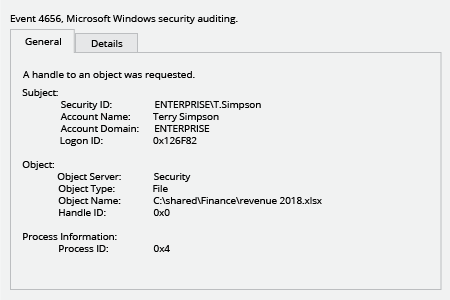
- Open Event Viewer → Search the Security Windows Logs for the event ID 4656 with the "Audit Failed" keyword, the "File Server" or "Removable Storage" task category and with "Accesses: READ_CONTROL" and Access Reasons: "WriteData (or AddFile) Not granted" strings. "Subject: Security ID" will show you who tried to change a file.
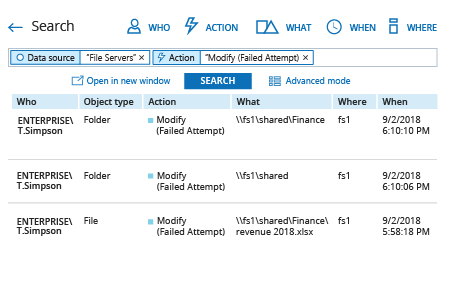
- Run Netwrix Auditor → Navigate to “Search” → Click on “Advanced mode” if not selected → Set up the following filters:
- Filter = “Data source”
Operator = “Equals”
Value = “File Servers” - Filter = “Action”
Operator = “Equals”
Value = “Modify (Failed Attempt)”
- Filter = “Data source”
- Click the “Search” button and review who tried to modify files and folders on your file server.
To create an alert on failed attempts to modify a file or a folder, do the following:
- From the search results, navigate to “Tools” → Click “Create alert” → Specify the new alert’s name.
- Switch to the “Recipients” tab → Click "Add Recipient" → Specify the email address where you want the alert to be delivered.
- Click “Add” to save the alert.