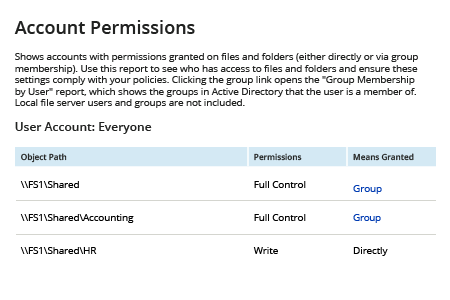
How to List Everyone Group Permissions
Netwrix Auditor for Windows File Servers
- Run Netwrix Auditor → Click “Reports” → Choose “File Servers” → Expand “File Servers State-in-Time” → Choose “Account Permissions” → Click “View” → Specify the File Share” → Click “View Report”.
Native Auditing
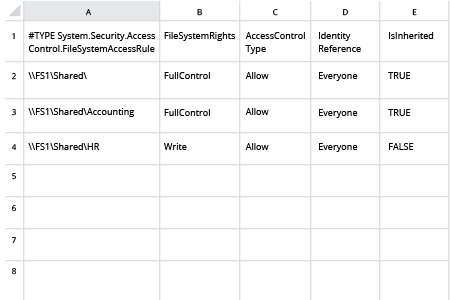
- To list Everyone group permissions in the NTFS file system, run the following script in PowerShell, specifying the appropriate values for the "Network File Share Path" and ".csv File Name And Path" parameters.
dir -Recurse | where { $_.PsIsContainer } | % { $path1 = $_.fullname; Get-Acl $_.Fullname | % { $_.access | where { $_.IdentityReference -like "everyone" } | Add-Member -MemberType NoteProperty -name "Network File Share Path" -Value $path1 -passthru }} | export-csv ".csv File Name And Path”
- Open the created .csv file in Microsoft Excel and check which shared folders the Everyone group has access rights to.
The importance of having control over “Everyone” group permissions
External attacks are not the only cause of security breaches. Practices such as granting NTFS permissions to the “Everyone” group or assigning permissions directly instead of through group membership can enable employees and other internal users to have access to data they shouldn’t be able to, possibly including sensitive data. And if the “Everyone” group has full control access to something, all Active Directory authenticated user accounts copy, distribute, read, modify and remove files — and so can all anonymous and guest accounts that are members of the Everyone group. This can lead to corruption, exfiltration or loss of data, as well as breaches of data privacy. To reduce these risks, system administrators should review share permissions granted to the "Everyone" group, as well as all permissions that were granted directly, on a regular basis.
Netwrix Auditor for Windows File Servers delivers complete visibility into user activity and who has access to what across your Windows-based file servers. State-in-time reports provide actionable details about which domain users have access to which files and show whether the permissions were granted directly or via AD group membership. With this intelligence, IT pros can easily detect permissions granted to the “Everyone” group and eliminate those properties to reduce the risk of data leaks and improve data security in their IT environment.
Share on
