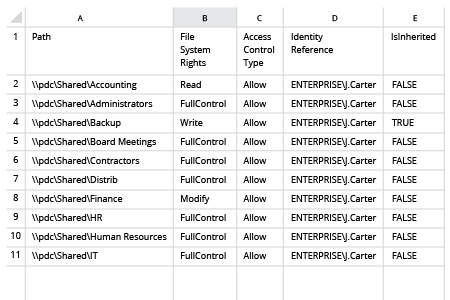
- Open Powershell ISE and create new script with the following code (define path on the file server and name of the user):
dir -Recurse \\fs1\Shared | where { $_.PsIsContainer } | % { $path1 = $_.fullname; Get-Acl $_.Fullname | % { $_.access | where { $_.IdentityReference -like "ENTERPRISE\J.Carter" } | Add-Member -MemberType NoteProperty '.\Application Data' -Value $path1 -passthru }} | Export-Csv "C:\temp\AccountPermissions.csv"
- Run the script.
- Open the file produced by the script in MS Excel.
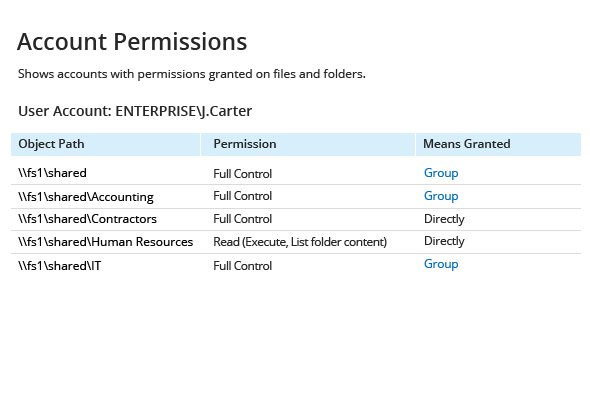
- Run Netwrix Audor → Click "Reports" → Navigate to File Servers → Choose "File Servers State-in-Time" → Select "Account Permissions"→ Click "View".
- To save the file, click the "Export" button → Select PDF format → Save as → Choose a location to save it.