Netwrix Auditor for Active Directory
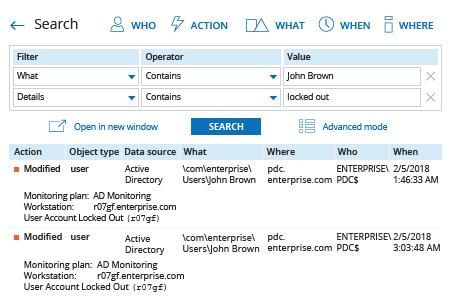
- Run Netwrix Auditor → Navigate to "Search" → Specify the following criteria:
- Filter – "What"
Operator – "Contains"
Value – "<account username>" - Filter – "Details"
Operator – "Contains"
Value – "Locked out"
- Filter – "What"
- Click "Search" and review the results.
Learn more about Netwrix Auditor for Active Directory
Native Auditing
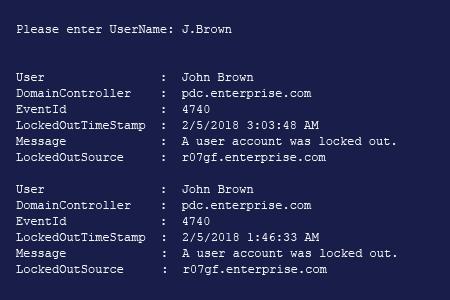
- Open the Powershell ISE → Run the following script, entering the name of the locked-out user:
Import-Module ActiveDirectory
$UserName = Read-Host "Please enter username"
#Get main DC
$PDC = (Get-ADDomainController -Filter * | Where-Object {$_.OperationMasterRoles -contains "PDCEmulator"})
#Get user info
$UserInfo = Get-ADUser -Identity $UserName
#Search PDC for lockout events with ID 4740
$LockedOutEvents = Get-WinEvent -ComputerName $PDC.HostName -FilterHashtable @{LogName='Security';Id=4740} -ErrorAction Stop | Sort-Object -Property TimeCreated -Descending
#Parse and filter out lockout events
Foreach($Event in $LockedOutEvents)
{
If($Event | Where {$_.Properties[2].value -match $UserInfo.SID.Value})
{
$Event | Select-Object -Property @(
@{Label = 'User'; Expression = {$_.Properties[0].Value}}
@{Label = 'DomainController'; Expression = {$_.MachineName}}
@{Label = 'EventId'; Expression = {$_.Id}}
@{Label = 'LockoutTimeStamp'; Expression = {$_.TimeCreated}}
@{Label = 'Message'; Expression = {$_.Message -split "`r" | Select -First 1}}
@{Label = 'LockoutSource'; Expression = {$_.Properties[1].Value}}
)
}}
- Review the results to find the source of the lockout.
Find an Account Lockout Source and the Reason for the Lockout using PowerShell or Netwrix Auditor
Locking out an Active Directory account after several failed authentication attempts is a common policy in a Microsoft Windows environment. Lockouts can happen for a variety of reasons, including forgotten passwords, expired service credentials in the cache, domain controller replication errors, incorrect drive mappings, disconnected terminal sessions on a Windows Server, and mobile devices accessing Exchange Server.
Before you unlock an account, you need to track down why the lockout happened in order to mitigate security risks and prevent the same issue from happening again. PowerShell is one tool you can use. The script provided above help you determine the account locked out source for a single user account by examining all events with ID 4740 in the Securitylog. The PowerShell output contains related details for further investigation: the computer where the account lockout occurred and the time when it happened.
Netwrix Auditor provides a more convenient way to find account lockout sources. The platform monitors the activity of all users in your environment, and provides detailed information about one or all account lockouts in an easy-to-read report that you can generate in just a few clicks.
Share on
