To enable Logon Auditing in Active Directory, follow the steps below.
- On your domain controller, run Group Policy Management Console (Press Win+R -> Type “GPMC.exe” -> Click “Run”).
- Create a new policy and link this new GPO to an organizational unit (OU) containing the computers where you’d like to track user activity.
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies. Then go to each of the following:
- System > Audit Security State Change — Set this to “Success.”
- Audit Policies > Logon/Logoff — Set both “Audit Logon” and “Audit Logoff” to “Success” and “Failure.”
- Audit Policies > Logon/Logoff > Audit — Set “Other Logon/Logoff Events” to “Success” and “Failure.”
To check user login history in Active Directory using Powershell, follow these steps:
- Open the PowerShell ISE as Administrator
- Run the following script, adjusting the timeframe:
# Find DC list from Active Directory
$DCs = Get-ADDomainController -Filter *
# Define time for report (default is 1 day)
$startDate = (get-date).AddDays(-1)
# Store successful logon events from security logs with the specified dates and workstation/IP in an array
foreach ($DC in $DCs){
$slogonevents = Get-Eventlog -LogName Security -ComputerName $DC.Hostname -after $startDate | where {($_.eventID -eq 4624) -or ($_.eventID -eq 4625) }}
# Crawl through events; print all logon history with type, date/time, status, account name, computer, and IP address if the user logged on remotely
foreach ($e in $slogonevents){
# Logon Successful Events
# Local (Logon Type 2)
if (($e.EventID -eq 4624 ) -and ($e.ReplacementStrings[8] -eq 2)){
write-host "Type: Local Logon`tDate: "$e.TimeGenerated "`tStatus: Success`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11]
}
# Remote (Logon Type 10)
if (($e.EventID -eq 4624 ) -and ($e.ReplacementStrings[8] -eq 10)){
write-host "Type: Remote Logon`tDate: "$e.TimeGenerated "`tStatus: Success`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11] "`tIP Address: "$e.ReplacementStrings[18]
}
# Logon Failed Events
# Local (Logon Type 2)
if (($e.EventID -eq 4625 ) -and ($e.ReplacementStrings[8] -eq 2)){
write-host "Type: Local Logon`tDate: "$e.TimeGenerated "`tStatus: Failed`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11]
}
# Remote (Logon Type 10)
if (($e.EventID -eq 4625 ) -and ($e.ReplacementStrings[8] -eq 10)){
write-host "Type: Remote Logon`tDate: "$e.TimeGenerated "`tStatus: Failed`tUser: "$e.ReplacementStrings[5] "`tWorkstation: "$e.ReplacementStrings[11] "`tIP Address: "$e.ReplacementStrings[18]
}}
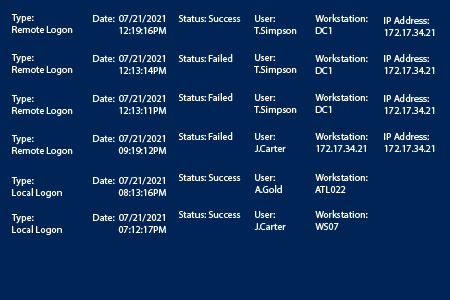
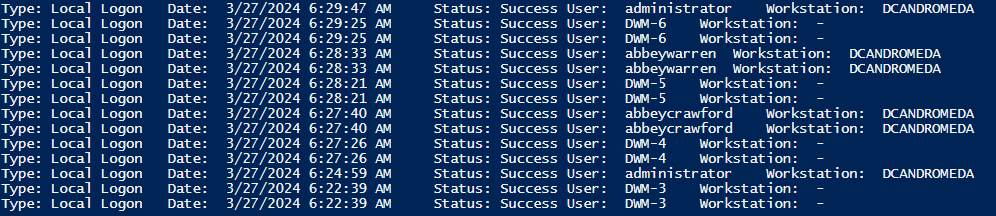
- Review the results:
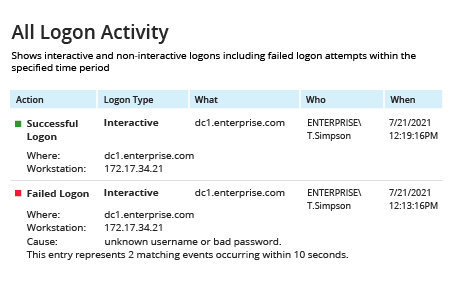
- Run Netwrix Auditor → Navigate to “Reports” → Open “Active Directory” → Go to “Logon Activity” → Depending on which logon events you want to review, select “Successful Logons,” "Failed Logons" or “All Logon Activity” → Click “View.”
- Review the report: