Netwrix Auditor: A Ferramenta de Monitoramento do SQL Server
Audite cada logon, elevação de permissão e alteração de esquema com uma ferramenta avançada e aprofundada de monitoramento do SQL Server.
Leia suas histórias
Confiado por





































































Software de auditoria do SQL Server simples que aumenta a segurança e a produtividade
Minimize o risco de violação de dados
Reforce a segurança de dados estruturados com ferramentas de monitoramento do SQL Server expondo permissões frouxas e identificando ações críticas.
Passe em auditorias de conformidade com menos esforço
Gere relatórios prontos para apresentação para PCI DSS, HIPAA, GDPR, SOX, GLBA, FISMA, CJIS e outros frameworks regulatórios.
Aumente a produtividade dos DBAs
Detecte, investigue e remedeie mudanças indesejadas, como a exclusão acidental de uma tabela de banco de dados.
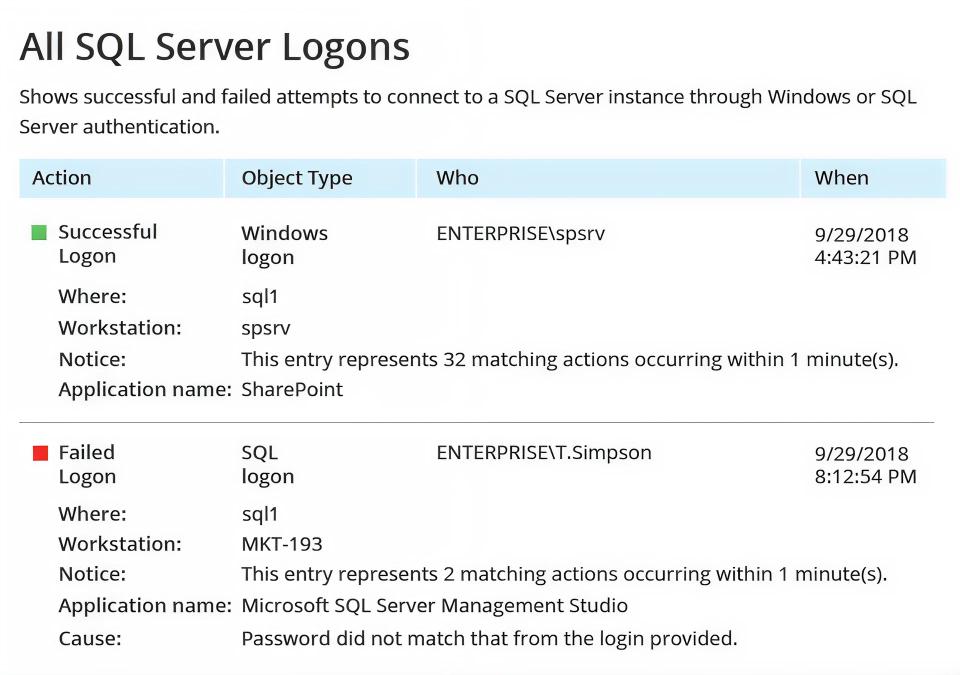
Cobertura de auditoria em toda a instância
Monitore alterações de configuração, modificações de banco de dados e atividades de usuários em todas as instâncias do SQL Server no seu ambiente.
Capacidades
Monitoramento do SQL Server que responde rapidamente a perguntas de conformidade, quando você mais precisa dos dados de auditoria SQL
Pronto para começar?
Soluções
Vá além da proteção contra uma única ameaça. Proteja todos os ângulos com as soluções Netwrix.






