How to Get an Active Directory OU Permissions Report
Netwrix Auditor for Active Directory
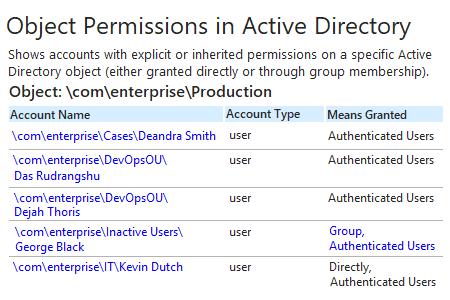
- Run Netwrix Auditor → Navigate to "Reports" → Expand the "Active Directory" section → Go to "Active Directory - State-in-Time" → Select "Object Permissions in Active Directory" → Click "View".
- Specify the values for the filters below and click "View Report":
- Object UNC Path
- Means Granted
- Permissions
- To save the report, click the "Export" button → Choose a format from the dropdown menu → Click "Save".
Learn more about Netwrix Auditor for Active Directory
Native Auditing
- Open the Powershell ISE → Create new script with the following code, specify Username and path for the export and run it:
$schemaIDGUID = @{}
#ignore duplicate errors if any#
$ErrorActionPreference = 'SilentlyContinue'
Get-ADObject -SearchBase (Get-ADRootDSE).schemaNamingContext -LDAPFilter '(schemaIDGUID=*)' -Properties
name, schemaIDGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.schemaIDGUID,$_.name)}
Get-ADObject -SearchBase "CN=Extended-Rights,$((Get-ADRootDSE).configurationNamingContext)" -LDAPFilter
'(objectClass=controlAccessRight)' -Properties name, rightsGUID |
ForEach-Object {$schemaIDGUID.add([System.GUID]$_.rightsGUID,$_.name)}
$ErrorActionPreference = 'Continue'
# Get OU.
$OUs = Get-ADOrganizationalUnit -Filter 'Name -like "Production"'| Select-Object -ExpandProperty
DistinguishedName
# retrieve OU permissions.
# Add report columns to contain the OU path and string names of the ObjectTypes.
ForEach ($OU in $OUs) {
$report += Get-Acl -Path "AD:\$OU" |
Select-Object -ExpandProperty Access |
Select-Object @{name='organizationalUnit';expression={$OU}}, `
@{name='objectTypeName';expression={if ($_.objectType.ToString() -eq '00000000-0000- 0000-0000-
000000000000') {'All'} Else {$schemaIDGUID.Item($_.objectType)}}}, `
@{name='inheritedObjectTypeName';expression={$schemaIDGUID.Item($_.inheritedObjectType)}}, `
*
}
# Export report out to a CSV file for analysis in Excel.
$report | Export-Csv -Path "C:\data\OU_Permissions.csv" -NoTypeInformation
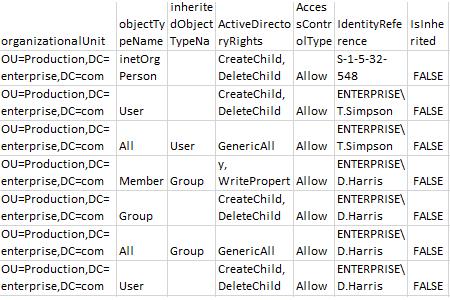
- Open the file produced by the script in MS Excel.
Sample report:
Get an Active Directory Permissions List for a Specific OU to Revoke Excessive Access Rights and Prevent Privilege Abuse
Strictly enforcing the least-privilege principle is essential for strong security. By reviewing a comprehensive Active Directory permissions report, you can determine who has access to what in the domain, see how user permissions were delegated (permissions were given directly or via group membership), and analyze whether each user’s access rights align with their responsibilities or no longer needed. Having this information will enable you to enforce the least-privilege model and minimize the risk of privilege abuse.
To keep an eye on permissions on an Active Directory group or OU, you can use native tools, such as PowerShell. But if you prefer not to spend all your time writing scripts and sifting through cryptic data, try Netwrix Auditor for Active Directory. It provides easy-to- read reports on explicit and inherited permissions for Active Directory objects, including domains, user groups, organizational units and more. On top of that, the solution delivers security intelligence rich in details about changes, access and configurations, so you can identify abnormal behavior, investigate threats and minimize the risk of privilege abuse.
Share on
