Comprehensive VMware Reporting
Privacy Policy
What data can I get?
Inspecting native audit logs is usually a slow and difficult task; plus, it’s easy to get lost in all the noise and miss something critical. Monitor important events across your infrastructure, such as changes made to the configuration of hosts, individual VMware virtual machines and datastores, using the advanced VMware reporting in Netwrix Auditor. Quickly spot unwanted changes, such as the uncontrolled creation of virtual machines or VM snapshots, so you can remediate them before they lead to virtualization sprawl, performance issues and compliance failures.
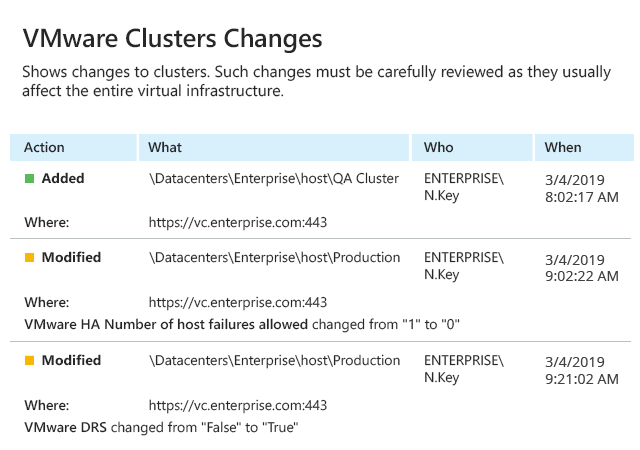
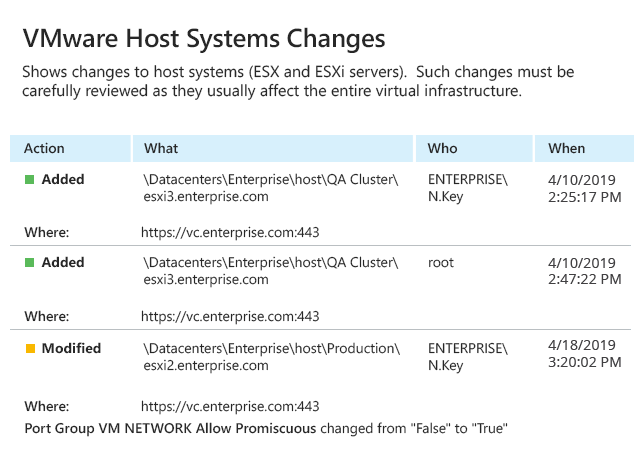
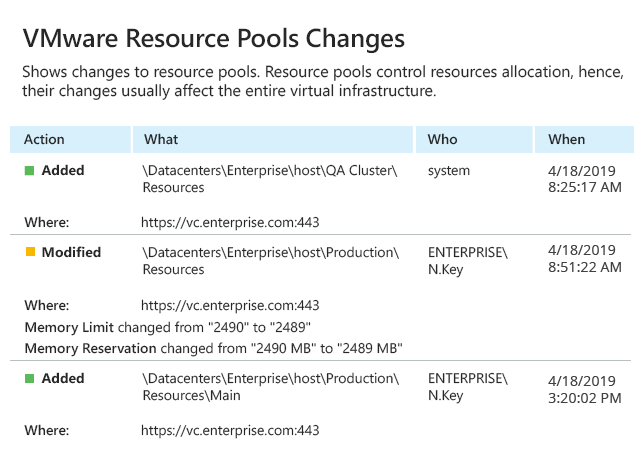
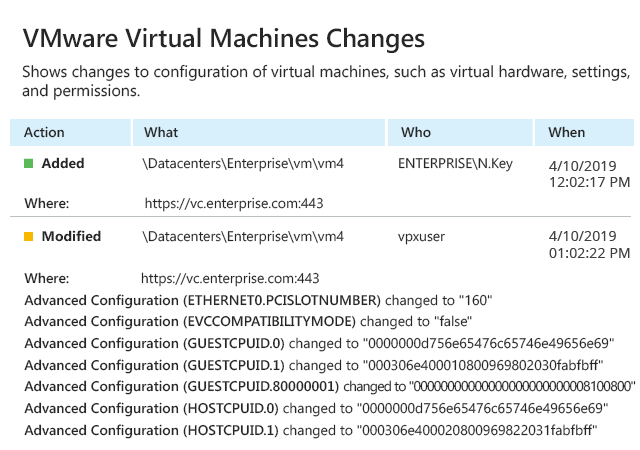
Inspecting native audit logs is usually a slow and difficult task; plus, it’s easy to get lost in all the noise and miss something critical. Monitor important events across your infrastructure, such as changes made to the configuration of hosts, individual VMware virtual machines and datastores, using the advanced VMware reporting in Netwrix Auditor. Quickly spot unwanted changes, such as the uncontrolled creation of virtual machines or VM snapshots, so you can remediate them before they lead to virtualization sprawl, performance issues and compliance failures.
Tracking logons to your VMware environment is crucial for ensuring IT security and business uptime. Without the right tools, it is easy to miss suspicious logons to ESXi hosts and vCenter that could indicate an attack. Netwrix Auditor makes it easy to detect failed logon attempts to your virtual environment and review successful ones, so you can validate your access controls, ensure IT security and maintain uninterrupted business processes.

The complex system of access permissions in VMware makes it difficult to ensure the security of your virtualized IT systems and the critical data they store. Understand who has access to what and remediate excessive rights that increase the risk of attackers getting their hands on your sensitive data, disrupting business processes or causing you additional audit findings.
.png)
_1595417699.png)
The complex system of access permissions in VMware makes it difficult to ensure the security of your virtualized IT systems and the critical data they store. Understand who has access to what and remediate excessive rights that increase the risk of attackers getting their hands on your sensitive data, disrupting business processes or causing you additional audit findings.
How can I use this data?
The tangled structure of VMware environments makes it difficult to stay on top of suspicious activity unless you have the right auditing tool. Netwrix Auditor can generate alerts on suspicious logons to your virtual environment and the modifications you deem most critical, such as the deletion of a virtual machine, updates made to host profiles or VMware cluster changes, so you can respond before the health of your VMware infrastructure is affected.
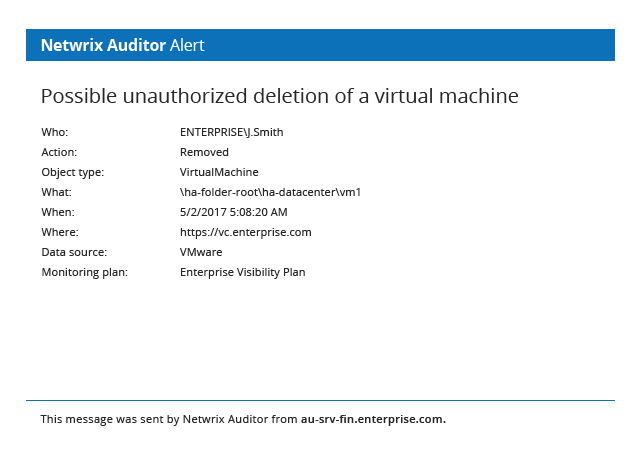
The tangled structure of VMware environments makes it difficult to stay on top of suspicious activity unless you have the right auditing tool. Netwrix Auditor can generate alerts on suspicious logons to your virtual environment and the modifications you deem most critical, such as the deletion of a virtual machine, updates made to host profiles or VMware cluster changes, so you can respond before the health of your VMware infrastructure is affected.
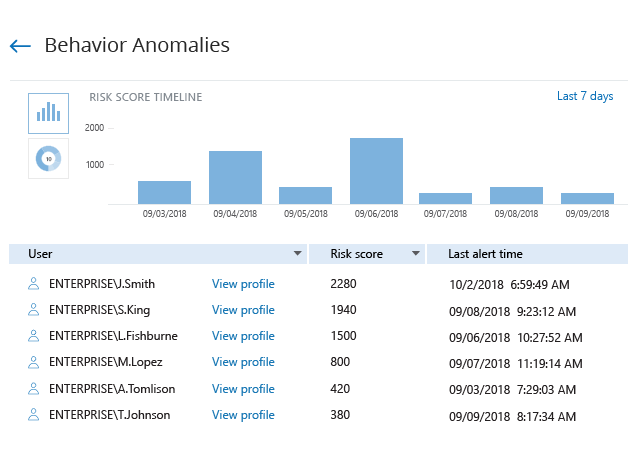
Some threats are more elaborate and stretch over time, so standard reports and alerts cannot spot them. Netwrix Auditor provides a unified view of all alerts triggered by an individual across all audited systems, and shows a list of suspicious users ranked by their cumulative risk scores. This functionality improves detection of threat actors and helps ensure the security of your systems.
Many events can disrupt your virtual infrastructure: A virtual machine can fail to connect to the network, storage utilization can become excessive, and critical changes can be made to VMware vSphere components or clusters in the VMware vCenter Server. Such issues have to be addressed promptly, before they impact the business. With Interactive Search, you can quickly display information about any event so you can remediate the problem fast and prevent it from occurring again.

Many events can disrupt your virtual infrastructure: A virtual machine can fail to connect to the network, storage utilization can become excessive, and critical changes can be made to VMware vSphere components or clusters in the VMware vCenter Server. Such issues have to be addressed promptly, before they impact the business. With Interactive Search, you can quickly display information about any event so you can remediate the problem fast and prevent it from occurring again.
To spot unusual spikes in user activity, you need an overview of all changes. It’s hard to grasp the bigger picture using native auditing tools. Netwrix Auditor’s consolidated dashboard helps you see at a glance which servers and objects were modified most, who made the most changes and when these changes happened.

Proving to auditors that your security controls work effectively is usually not an easy feat. Eliminate the stress of your next PCI DSS, HIPAA, SOX, GLBA, FISMA/NIST, CJIS, GDPR or other compliance audit and slash the preparation time with out-of-the-box compliance reports mapped to a broad range of regulatory standards.

Proving to auditors that your security controls work effectively is usually not an easy feat. Eliminate the stress of your next PCI DSS, HIPAA, SOX, GLBA, FISMA/NIST, CJIS, GDPR or other compliance audit and slash the preparation time with out-of-the-box compliance reports mapped to a broad range of regulatory standards.
What else do I get with Netwrix Auditor
for VMware?
A RESTful API makes it easy to integrate Netwrix Auditor with a variety of applications. This integration gives you a unified view of what’s going on across multiple systems and access your complete audit trail within one product. Free, ready-to-use add-ons are available for many common applications, including SIEMs, Linux and Unix, and Amazon Web Services (AWS).
A RESTful API makes it easy to integrate Netwrix Auditor with a variety of applications. This integration gives you a unified view of what’s going on across multiple systems and access your complete audit trail within one product. Free, ready-to-use add-ons are available for many common applications, including SIEMs, Linux and Unix, and Amazon Web Services (AWS).
A RESTful API makes it easy to integrate Netwrix Auditor with a variety of applications. This integration gives you a unified view of what’s going on across multiple systems and access your complete audit trail within one product. Free, ready-to-use add-ons are available for many common applications, including SIEMs, Linux and Unix, and Amazon Web Services (AWS).
Manually responding to basic incidents usually requires a lot of time. Netwrix Auditor can automatically run custom scripts when specific alerts are triggered, so you don’t have to handle them one by one. This feature helps you respond promptly to common issues while staying focused on more important tasks.
Manually responding to basic incidents usually requires a lot of time. Netwrix Auditor can automatically run custom scripts when specific alerts are triggered, so you don’t have to handle them one by one. This feature helps you respond promptly to common issues while staying focused on more important tasks.
Manually responding to basic incidents usually requires a lot of time. Netwrix Auditor can automatically run custom scripts when specific alerts are triggered, so you don’t have to handle them one by one. This feature helps you respond promptly to common issues while staying focused on more important tasks.
Storing the audit trail of your virtual environment is critical for both your own security investigations and compliance with certain regulations. Netwrix Auditor enables you to store your audit trail for more than 10 years in a cost-effective, two-tiered (file-based + SQL database) manner.
Storing the audit trail of your virtual environment is critical for both your own security investigations and compliance with certain regulations. Netwrix Auditor enables you to store your audit trail for more than 10 years in a cost-effective, two-tiered (file-based + SQL database) manner.
Storing the audit trail of your virtual environment is critical for both your own security investigations and compliance with certain regulations. Netwrix Auditor enables you to store your audit trail for more than 10 years in a cost-effective, two-tiered (file-based + SQL database) manner.
It’s critical to have only the right people managing VMware reporting configuration and viewing reports. You can grant appropriate access rights for Netwrix Auditor to IT administrators and business teams based on the scope of their responsibilities, whether that’s an entire virtual infrastructure or a standalone ESXi host.
It’s critical to have only the right people managing VMware reporting configuration and viewing reports. You can grant appropriate access rights for Netwrix Auditor to IT administrators and business teams based on the scope of their responsibilities, whether that’s an entire virtual infrastructure or a standalone ESXi host.
It’s critical to have only the right people managing VMware reporting configuration and viewing reports. You can grant appropriate access rights for Netwrix Auditor to IT administrators and business teams based on the scope of their responsibilities, whether that’s an entire virtual infrastructure or a standalone ESXi host.

Find out how Netwrix Auditor for VMware will help you detect critical changes to your virtual infrastructure, optimize your environment and streamline compliance audits.

Get the full list of features of Netwrix Auditor for VMware in a convenient format for comparing it with other security auditing tools.
Deploy Netwrix Auditor wherever you need it
Download a free 20-day trial of Netwrix Auditor and deploy it on Microsoft Windows Server.
Download our virtual appliance and start using Netwrix Auditor without having to provision any hardware or software.
