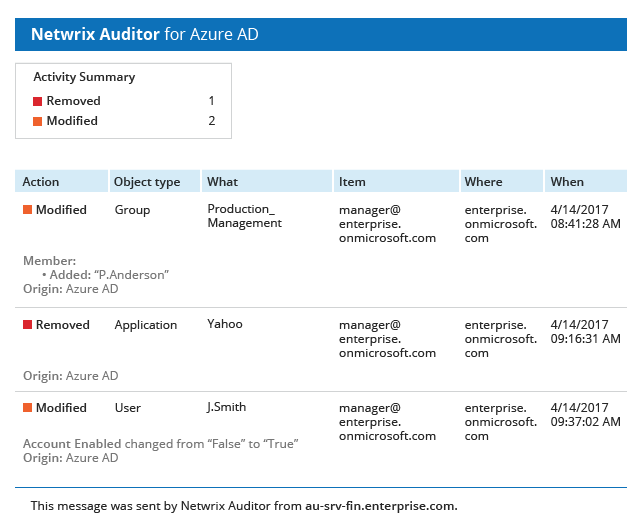
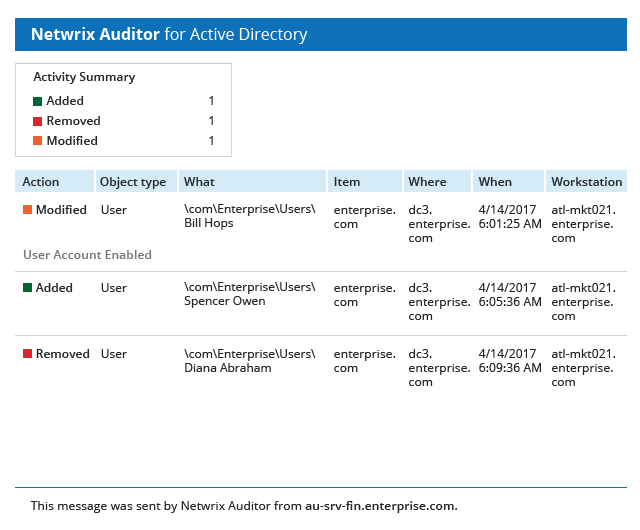
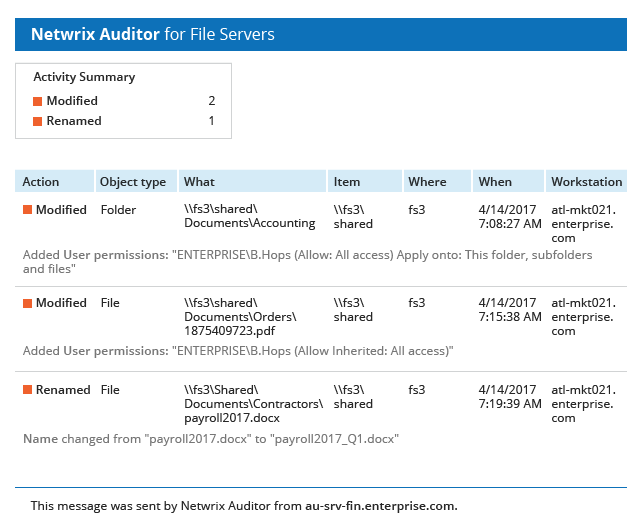
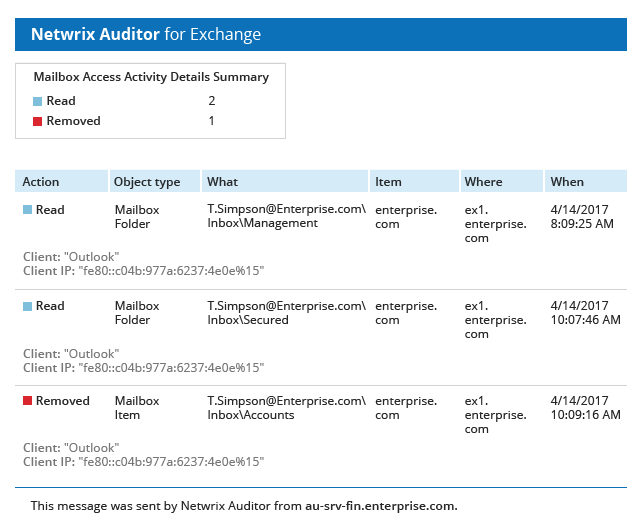
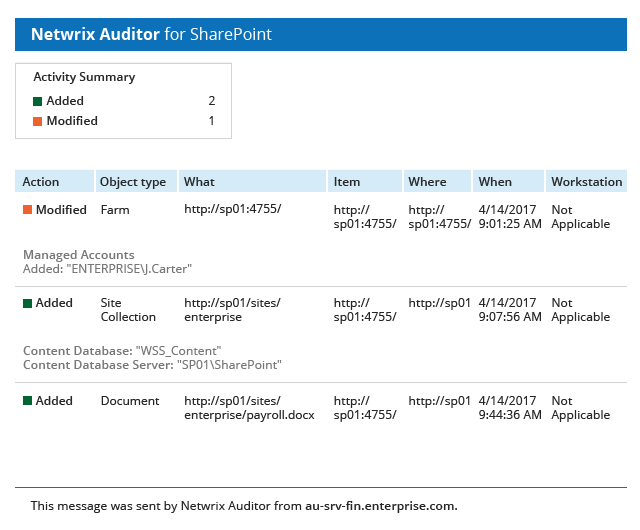
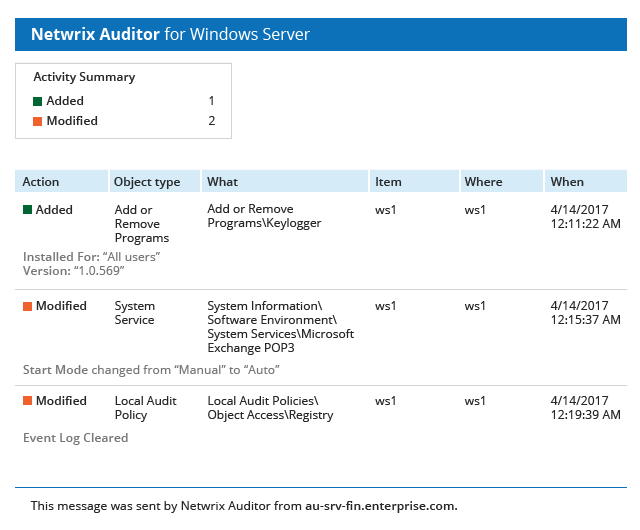
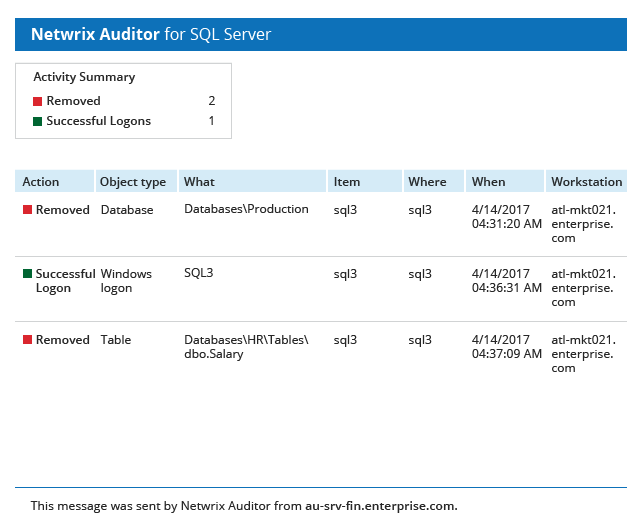
View a list of current vulnerabilities and their associated risk level. Includes passwordless users, loose permissions, sensitive data in filenames, and more. See which vulnerabilities are most critical and prioritize remediation.
Easily adjust risk thresholds so you only see what impacts your organization.