_1664276356.png)
Detect security threats, prove compliance and increase IT team efficiency with IT audit software
More and more organizations, regardless of size or industry, are recognizing the value of conducting regular internal and external IT audits. The benefits are many: IT auditing can help you improve security, pass compliance audits and optimize IT operations. But all too often, the process is far more cumbersome and time-consuming than it needs to be. Learn how Netwrix Auditor software can help you improve your security posture, ease the auditing burden and achieve your goals with far less effort.
Audit your most important IT systems from a centralized platform
Are you tired of juggling multiple auditing and reporting tools in an attempt to collect audit information from all your on-premises and cloud-based systems? Do you need a software solution that delivers that information in a unified and consistent way? Netwrix Auditor provides a consolidated audit trail across a wide variety of IT systems, including Active Directory, Windows Server, Oracle Database and network devices.
Get the information you need, when you need it, with IT audit software from Netwrix
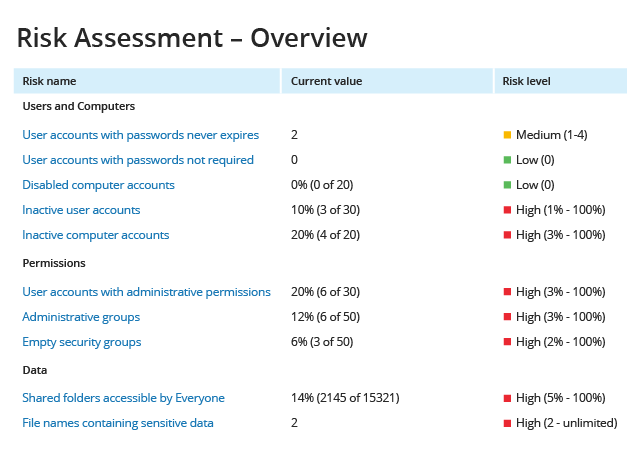
Mitigate weaknesses with risk assessment
Protect your sensitive data regardless of its location
Save time with change, access and configuration reports
Streamline user access reviews
Receive alerts on threat patterns
Improve detection of sophisticated threats
Spot even slight indicators of a threat
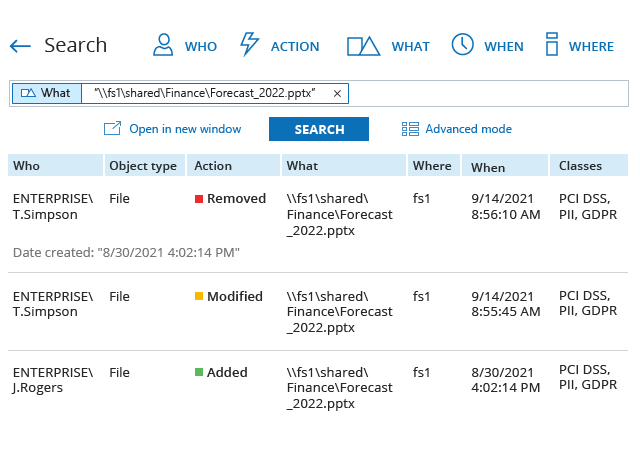
Find answers with Google-like search
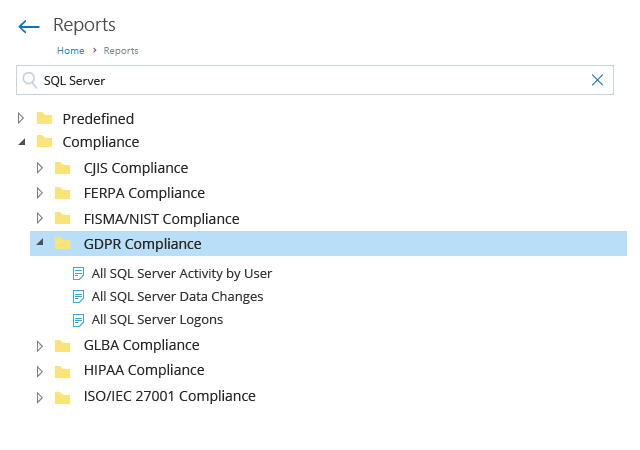
Pass compliance audits with less stress
Read how Netwrix Auditor helps organizations overcome their security, compliance and operational challenges

- Security audits to uncover threats and risky behavior.
- Compliance audits to demonstrate adherence to regulations like GDPR, HIPAA, or SOX.
- Access audits to verify least privilege.
- Operational audits to ensure processes and configurations support system stability and performance.