Netwrix Auditor: IT Audit Software
See who’s accessing what, when, and why. Netwrix IT audit software gives you the answers you need to identify risks, detect threats, and automate compliance.
Read their Stories
Trusted by




































































IT auditing just got a whole lot simpler
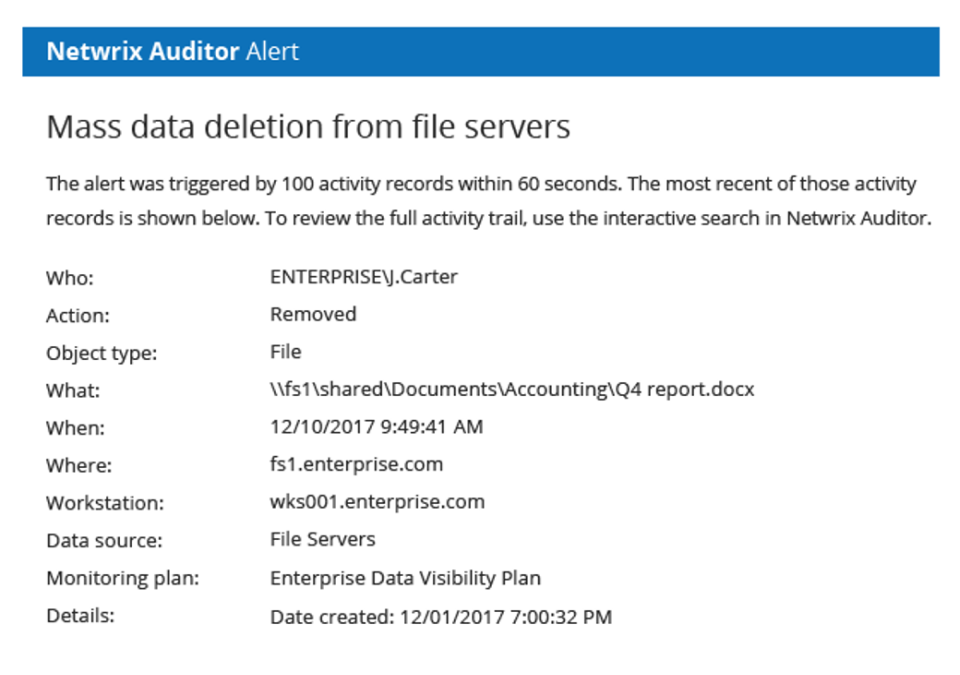
Prevent data breaches
Identify suspicious activities and unusual behavior as soon as they happen with customized alerts that help you take action fast.
Improve your security posture
Spot and mitigate risks around your sensitive data before you suffer a data breach.
Save time with built-in automation
Speed up routine tasks like auditing and reporting to free up your team and boost productivity.
Compliance made easy
Access prebuilt reports for HIPAA, PCI, SOX, and more. Plus, quickly address auditors’ questions.
Capabilities
Audit your most important IT systems from one centralized platform
Powerful IT auditing, wherever you work

Netwrix Auditor for Azure Files
Gain full visibility into activity across Azure Files so you can detect suspicious behavior, enforce compliance, and keep critical data safe.

Netwrix Auditor for Qumulo
Track changes, permissions, and access in Qumulo storage environments to reduce insider risk and simplify audits.

Netwrix Auditor for Synology
Monitor user actions and data access on Synology NAS systems to spot threats early and strengthen your compliance posture.
Ready to get started?
Solutions
Go beyond single-threat protection. Secure every angle with Netwrix solutions.
Trusted by professionals
Don’t just take our word for it





















